Novel Advanced MaaS Platform for Android Used in Phishing Campaign Impersonating Banks
- The SuperCard X fraud campaign enables unauthorized POS payments and contactless ATM withdrawals.
- Attackers combine NFC relay techniques with social engineering to conduct highly effective fraud operations.
- This advanced Android malware is distributed via a Chinese-speaking MaaS platform.
An advanced Android malware distributed via a Chinese-speaking Malware-as-a-Service (MaaS) platform was discovered. Attackers use phishing techniques via text or social media messages to impersonate legitimate banks to obtain sensitive details or install malicious apps.
Dubbed SuperCard X, it exploits Near-Field Communication (NFC) technology and enables unauthorized Point-of-Sale (POS) payments and contactless ATM withdrawals. While the current campaign targets Italy, the availability of SuperCard X as a MaaS platform suggests a wider potential impact.
Cleafy Threat Intelligence has uncovered that SuperCard X operates through a multi-pronged attack strategy executed via a carefully crafted fraud lifecycle, which includes social engineering and advanced malware deployment.
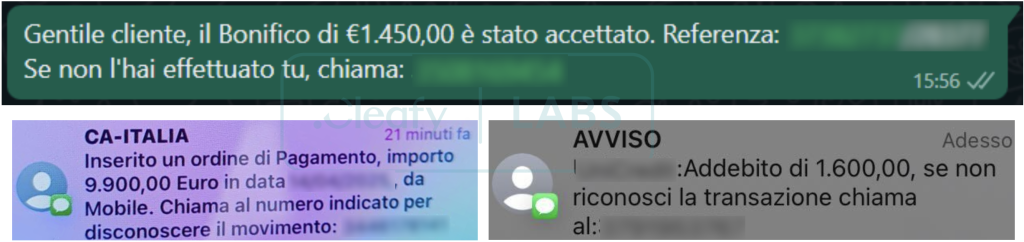
Victims receive fake SMS or WhatsApp messages mimicking official bank alerts, triggering urgency around a fictitious fraudulent transaction. Using direct phone calls and persuasive scripts, attackers convince victims to divulge sensitive information like PINs and install a malicious app disguised as a legitimate security tool.
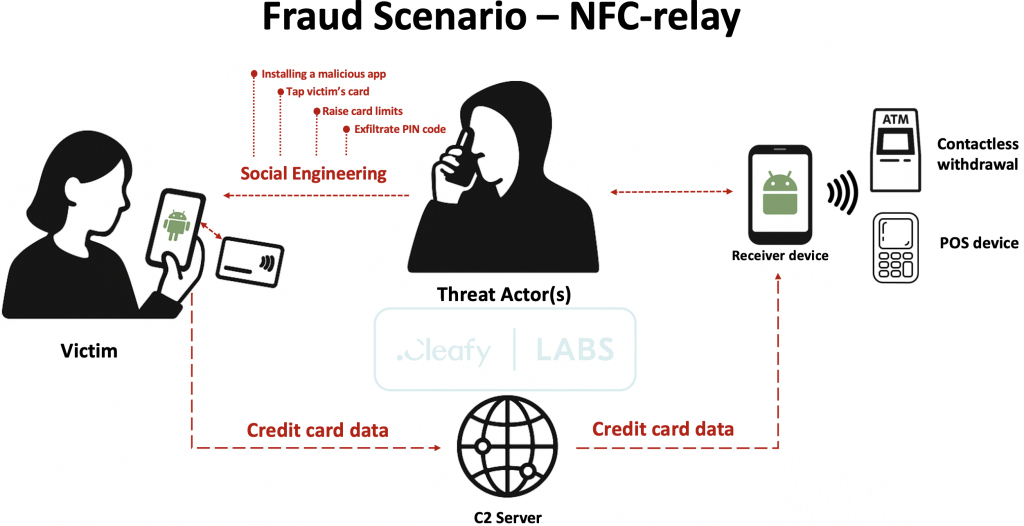
The malware silently intercepts NFC data from victims' payment cards, transmitting it in real time via the attackers' Command and Control (C2) infrastructure to execute fraudulent payments or withdrawals.
Unlike traditional banking fraud methods requiring direct interaction with financial institutions, SuperCard X exploits NFC capabilities to bypass such controls entirely. The malware supports "instant payment," allowing attackers to directly access stolen funds without detection delays.
The use of NFC technology in malware isn't new, but rarely has it been applied with this level of sophistication. The coordinated design of SuperCard X, with paired “Reader” and “Tapper” applications connected via C2 servers, represents a new frontier in mobile malware.
Developers of SuperCard X have leveraged a streamlined and stealthy architecture, focusing narrowly on its NFC relay capability. The minimalistic permission model, requesting only NFC access and standard app permissions, evades traditional antivirus tools and behavioral analysis mechanisms.
Mutual TLS (mTLS) secures communication between victim devices and C2 servers, complicating interception and analysis by defenders.
Regional adaptations of the malware, such as those observed in Italy, indicate a flexible MaaS model designed to evade detection and attribution.
Affiliates using this model can localize attacks, allowing threat actors to target victims in multiple regions. An alarming overlap with previously identified NGate malware also points to increasing collaboration and code reutilization within the cybercriminal ecosystem.