Updated Version of the Separ Malware Shows that Simplicity is Key to “Live Off the Land”
- A new version of the Separ Malware has already infected 1200 systems in a couple of weeks.
- Separ is employing the good old tricks of “living off the land”, successfully getting past security checks.
- There’s no sophistication of obfuscation implemented in the process at all, proving that this is not an absolute prerequisite for a successful attack.
Separ is a credential stealer that has been widely used since 2013, leading many successful campaigns that left many thousands of victims behind. You would think that obsolete malware tools like Separ are not effective against current anti-malware solutions, but a recent report by Deep Instinct will make you reconsider. According to the researchers, there’s a new wave of attacks using an upgraded version of Separ, which remains versatile and able to bypass anti-malware checks thanks to its combination of very short scripts. This process is what the researchers call “live off the land” type, and it’s an old but still effective trick.
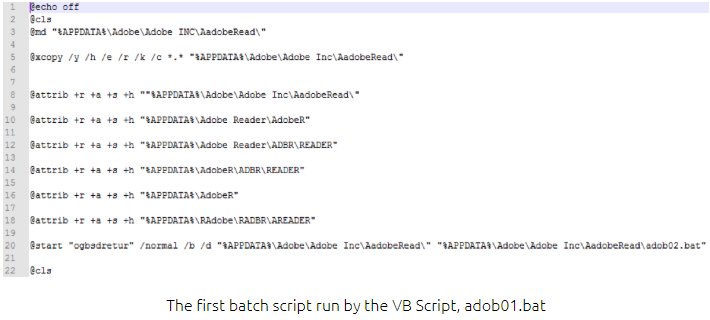
Carrying out short and seemingly legitimate steps that lead to exploitation is one way to trick the protection and security tools, but you still have to trick the users as well. To achieve this, Separ is posing as a PDF document attached to a phishing email. If the victim is convinced to open to file, a series of executions of administration tools takes place, as the file is not really a PDF file but a Visual Basic script binary. After running various batch scripts, a decoy image pops up to hide the activity from the user’s eyes. This malicious activity comprises of dumping passwords, launching an NcFTP client, and neatly bundling everything and uploading the collected data to the actors’ server.
source: deepinstinct.com
The researchers say that besides that ludicrous pop-up, there’s no obfuscation going on at all and that the attackers have left everything open for the investigators to analyze freely. This resulted in figuring out the current victims of this latest wave, comprising of 200 organizations and about a thousand of individuals. As much as the infection vector seems obvious, and as simple as the operation may seemingly be, Separ has managed to rob the credentials of 1200 victims over the period of a couple of weeks. This goes to show that developing highly sophisticated malware tools to trick people and override security checks is not the only way to go for attackers right now. Simple tools can do the job well enough, in a world full of instinctive curiosity and innocencecal naivety.
Have you ever encountered a file that looks like a PDF but has a different file-type extension? Share your experience in the comments section beneath, or on our socials, on Facebook and Twitter.