Hackers Exploit SourceForge to Distribute Miner and ClipBanker Trojan via Fake Microsoft Office Tools
- A seemingly legitimate "officepackage" project hosted on SourceForge contains fake Microsoft Office add-ins.
- These redirect visitors to malicious download pages disguised as software offerings that distribute a miner and ClipBanker.
- ClipBanker is a malware family that replaces cryptocurrency wallet addresses in the clipboard with the attackers’ own.
Attackers leveraged the features of SourceForge, a popular platform used for hosting and distributing software, to deploy cryptocurrency miners and a ClipBanker Trojan, a malware type that manipulates clipboard data to redirect cryptocurrency transactions to the attackers' wallets.
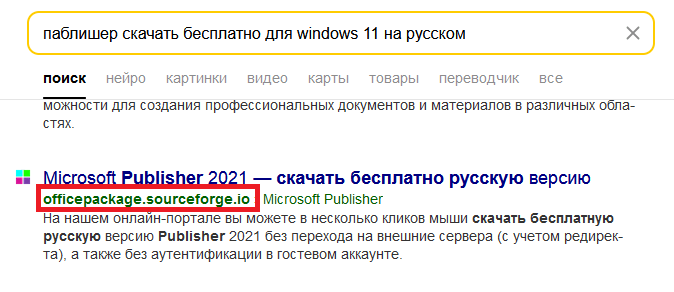
The campaign begins with a seemingly legitimate "officepackage" project hosted on SourceForge, appearing to contain Microsoft Office add-ins. However, this project is a front for a sophisticated malware scheme, a recent Kaspersky investigation reveals.
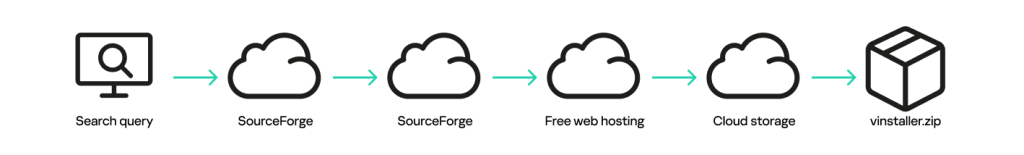
SourceForge automatically assigns a separate subdomain (e.g., officepackage.sourceforge.io) for each project, which attackers exploit to redirect visitors to malicious download pages disguised as software offerings.
Clicking these deceptive download buttons funnels victims through multiple redirections before downloading a suspicious file, vinstaller.zip. The size and format of the file are designed to reduce suspicion, with the expected software installer ultimately delivering malware.
The infection process involves several steps:
- Deceptive Archive: vinstaller.zip contains a password-protected archive, installer.zip, and a Readme.txt file with the password.
- Obfuscation Tactics: The extracted installer file, installer.msi, appears genuine, using file pumping techniques to inflate its size artificially.
- Execution and Payload: The installer deploys various components, including RAR archives, VB scripts, and batch files that execute advanced infection chains and persistence tactics.
AutoIt interpreter and scripts are used to inject two key malware payloads into the system: Miner for unauthorized cryptocurrency mining and ClipBanker Trojan for intercepting crypto transaction data from the clipboard.
This campaign is notable for its use of advanced persistence techniques. The attackers employ multiple mechanisms, including registry modifications to ensure auto-starting of malicious files, and the creation of fake services like "NetworkConfiguration" and "PerformanceMonitor."
The attackers also exploit Windows installer scripts (e.g., ErrorHandler.cmd) to sustain infection and support Command-and-control (C2) communication using Netcat and Telegram APIs for data exfiltration.
The campaign primarily targets Russian-speaking users, as evidenced by the language settings of the malicious sites and user telemetry. From January to March 2025, over 4,600 users in Russia encountered this scheme.
While the primary goal of this campaign appears to be cryptocurrency-focused, the attackers' sophisticated approach and persistence methods raise significant security concerns. The backdoor access they establish could be leveraged by other cybercriminal actors, posing a broad threat to infected systems.