Oracle Cloud Data Breach Validated by Security Experts, Affecting Over 140,000 Tenants
- An alleged Oracle Cloud data breach was reportedly verified by security experts.
- The incident may have exposed SSO and LDAP credentials, OAuth2 keys, and customer tenant information.
- The threat actor claims to have exfiltrated 6 million records from Oracle Cloud.
Cybersecurity researchers say a significant breach affected Oracle Cloud, reportedly involving over six million records. An investigation by cybersecurity firm CloudSEK challenges Oracle’s earlier denial of any compromise.
The breach allegedly exposed sensitive Single Sign-On (SSO) and Lightweight Directory Access Protocol (LDAP) credentials, OAuth2 keys, and customer tenant information. Proven real, the breach poses a serious threat of supply chain attacks on affected organizations.
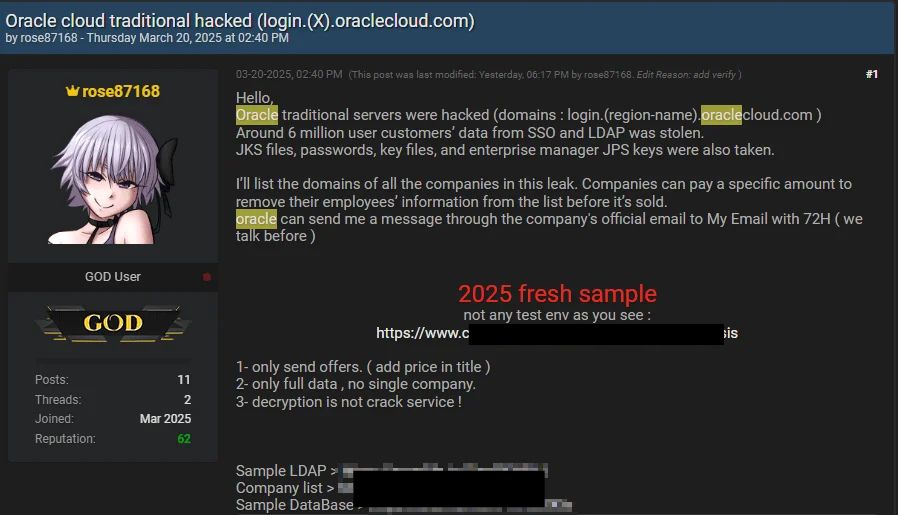
CloudSEK’s XVigil platform first flagged the breach on March 21, 2025, when a user named “rose87168” posted on BreachForums, offering the compromised records for sale. The breach took place approximately 40 days before.
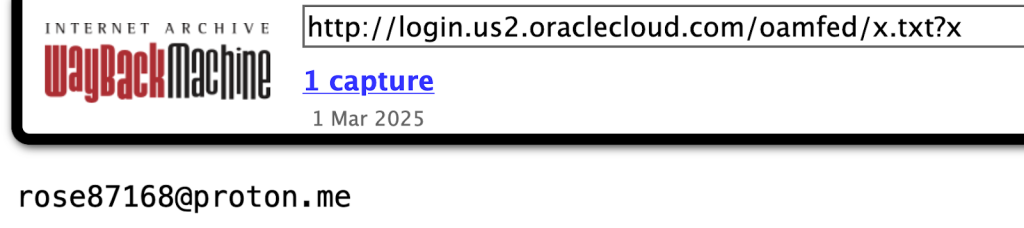
A thorough investigation by CloudSEK confirmed the use of a compromised production SSO endpoint, login.us2.oraclecloud.com, affecting real customer data and indicating production access rather than test environments.
Key findings in CloudSEK’s report reveal real evidence, authentic customer data, and the exposure scope.
Manual reviews and corroborations showed consistent authentication credentials and functionality related to Oracle’s SSO endpoint beyond mere test environments. CloudSEK also verified attacker claims using archival public data and GitHub repositories referencing Oracle’s SSO setups.
Domains such as nucor-jfe.com and sbgtv.com, listed in the leaked sample by the attacker, matched live configurations across public repositories. Notably, these domains were used in production environments, raising the stakes of this compromise.
A 10,000-line sample released by the attacker affected 1,500+ unique organizations, lending credence to the breach’s authenticity. Compromised records also included email addresses.
Oracle categorically denied any breach in an initial response, asserting that “there has been no breach of Oracle Cloud.” The cybersecurity community has since scrutinized this claim, citing extensive evidence provided by CloudSEK and its independent validation efforts.