DarkCrystal RAT Targets Ukrainian Defense Employees Through Signal Messaging App
- Employees of enterprises and representatives of the Defense Forces of Ukraine are targeted with malware.
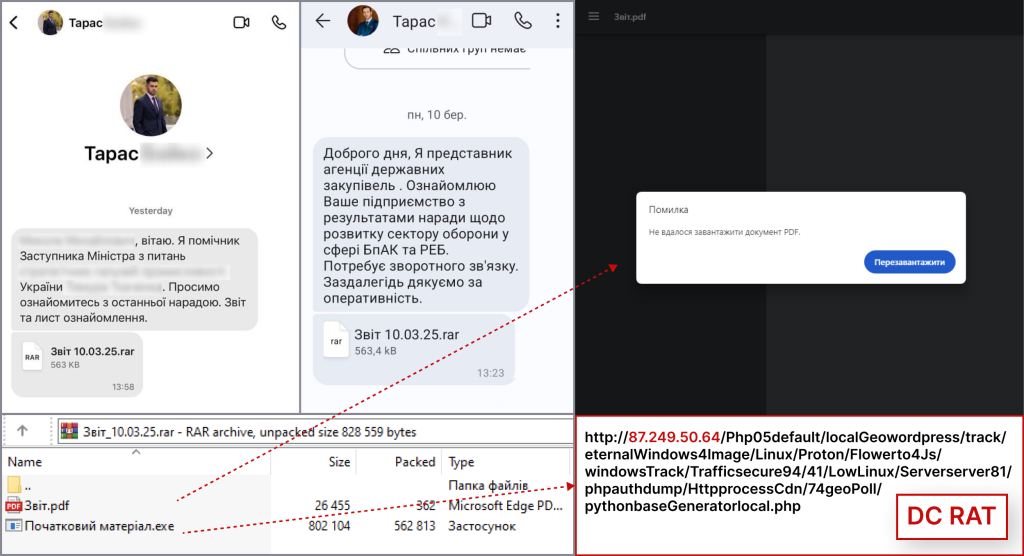
- The campaign employs malicious messages sent via the Signal messaging app, sometimes from contacts compromised in advance.
- They contain archive files that include a decoy PDF document and an executable, ultimately deploying DC RAT.
A new cyber campaign targeting the Ukrainian defense sector involves the deployment of the notorious DarkCrystal RAT (DC RAT), a powerful remote access trojan, through the Signal messaging app.
The attack focuses on employees of defense enterprises and representatives of Ukraine's Defense Forces. By exploiting Signal's communication platform, cybercriminals are delivering malicious messages disguised as official meeting minute files.
The Computer Emergency Response Team of Ukraine (CERT-UA) raised the alarm regarding this new cyber campaign. These messages often originate from compromised Signal accounts, increasing the likelihood that recipients will trust and open them.
These malicious messages contain archive files that include a decoy PDF document and an executable. The executable leverages a sophisticated .NET-based crypter, known as DarkTortilla, to decrypt and execute the DC RAT malware on the target system.
Once deployed, DC RAT enables attackers to execute arbitrary commands, steal sensitive data, and maintain full remote control over infected devices. CERT-UA has attributed the campaign to a threat cluster identified as UAC-0200, which has been active since at least the summer of 2024.
CERT-UA has highlighted the risks associated with using popular messaging apps like Signal for both work and personal communications. The use of these platforms significantly expands the attack surface, creating uncontrolled information exchange channels that adversaries can exploit.
The threat actors behind these attacks are not operating in isolation. Reports from Microsoft and Google have documented increasing Russian attempts to compromise WhatsApp and Signal accounts by exploiting device-linking features.
This trend coincides with Ukrainian citizens shifting to Signal as a more secure alternative to Telegram for communication.
Last year, the Russian military cyber-espionage group Sandworm, also referred to as UAC-0113, APT44, Telebots, Voodoo Bear, IRIDIUM, Seashell Blizzard, and Iron Viking, was linked to a series of malware campaigns targeting Windows users in Ukraine with DC RAT.