‘Cobalt Strike Cat’ Hits South Korean Govt Organizations and Businesses via Rust Beacon
- A publicly exposed server hosted a Rust-compiled Windows executable delivering Cobalt Strike Cat.
- The web server was accessible for less than 24 hours and contained tools linked to an intrusion campaign targeting South Korean organizations.
- Tools like SQLMap, Web-SurvivalScan, and dirsearch indicated a deliberate and well-organized attack.
A new and sophisticated approach targeting South Korean government and commercial entities with a variant of Cobalt Strike, known as ‘Cobalt Strike Cat,’ deployed via a Rust-based loader. Security researchers identified an open directory hosted on the EDGENAP LTD network in Japan.
The directory, which was briefly accessible on March 8, contained open-source tools to identify and exploit vulnerable web applications, including SQLMap, Web-SurvivalScan, and dirsearch.
Together, these tools enabled the attacker to identify and exploit vulnerable web applications systematically, cybersecurity researchers at Hunt.io said in a recent report.
Notably, the threat actor compiled a target list of over 1,000 South Korean domains, spanning government agencies, local municipalities, and commercial companies.
By automating reconnaissance activities through Python scripts like urls.py and utilizing tools such as Web-SurvivalScan, the attackers streamlined their subdomain enumeration, significantly improving their targeting capabilities.
The Rust-compiled loader marks a key innovation in this campaign. This Windows executable delivered the modified variant, Cobalt Strike Cat, which modifies functionalities of the widely used penetration-testing framework.
Originally circulated on a Chinese-language hacking forum, CS Cat provides advanced post-exploitation capabilities.
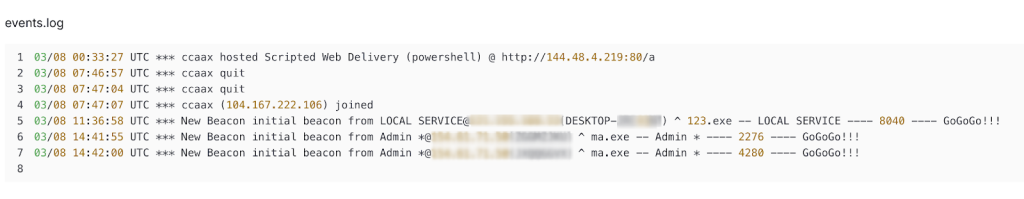
The investigation revealed beacon logs confirming active intrusions. By executing payloads like 123.exe and ma.exe, the attackers successfully established connections with compromised hosts.
Researchers also noted features such as misdirection tactics, with the loader redirecting sandbox analyses to the CIA’s official website.
Analysis of the malicious files uncovered Marte shellcode embedded in Rust-compiled binaries that acted as an intermediate layer. They decoded and executed the payload without directly dropping it on disk to evade detection and hinder forensic analysis.
While forensic review of tools and logs provided clarity on initial access tactics and post-exploitation activity, the full extent of the actions on victim systems, such as lateral movements or data exfiltration, remains undetermined.