MirrorFace’s Operation AkaiRyu Targets Europe with Japan EXPO Lures, Deploys ANEL Backdoor
- China-aligned APT group MirrorFace exhibits advanced tactics ahead of Japan’s Expo 2025.
- The threat actor used event-related lures in phishing emails that ultimately deployed malware.
- MirrorFace made use of a customized AsyncRAT strain and the ANEL and HiddenFace backdoors.
China-aligned advanced persistent threat (APT) group MirrorFace, known for its focus on cyberespionage in Japan, was observed targeting a Central European diplomatic institute for the first time. Their spearphishing campaign involved Expo 2025-themed emails.
Cybersecurity experts at ESET have identified a recent campaign, named "Operation AkaiRyū" (Japanese for "Red Dragon"), which marks a notable shift in MirrorFace's operations.
The operation, detected between Q2 and Q3 of 2024, was linked to Expo 2025, an international event scheduled to take place in Osaka, Japan.
Using carefully crafted spearphishing emails exploiting themes tied to the expo, MirrorFace infiltrated its target, showcasing its expanding geographic reach while maintaining its strategic focus on Japan-related activities.
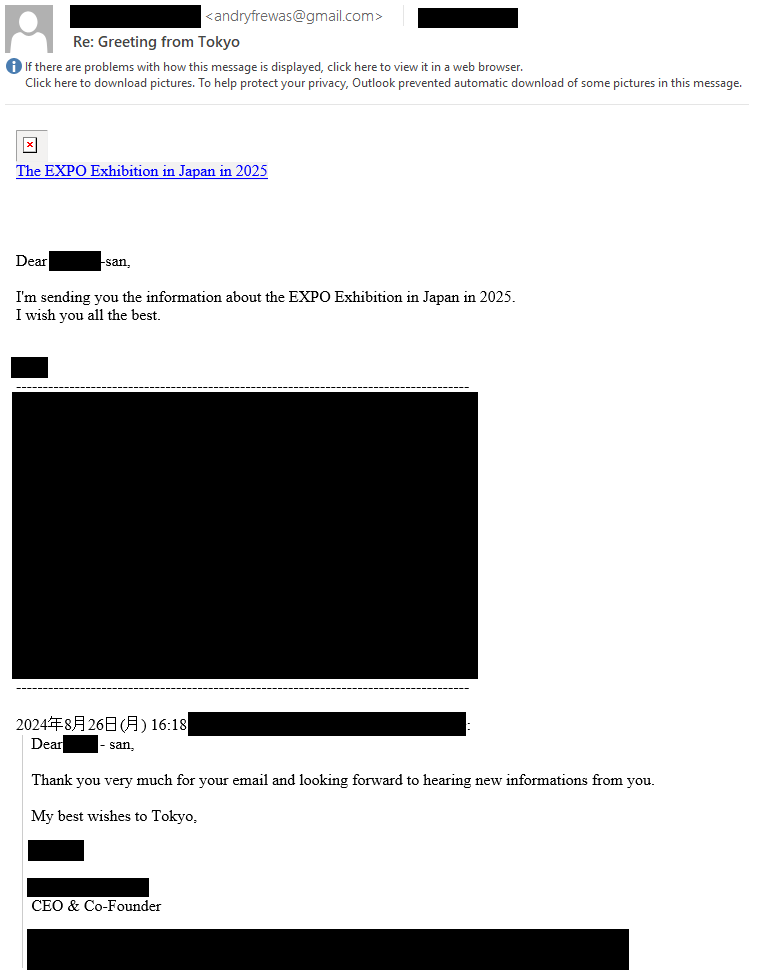
ESET's collaboration with the targeted Central European diplomatic institute provided a rare insight into the attack. Spearphishing emails initially masqueraded as professional correspondence linked to a Japanese nonprofit organization, referencing Expo 2025.
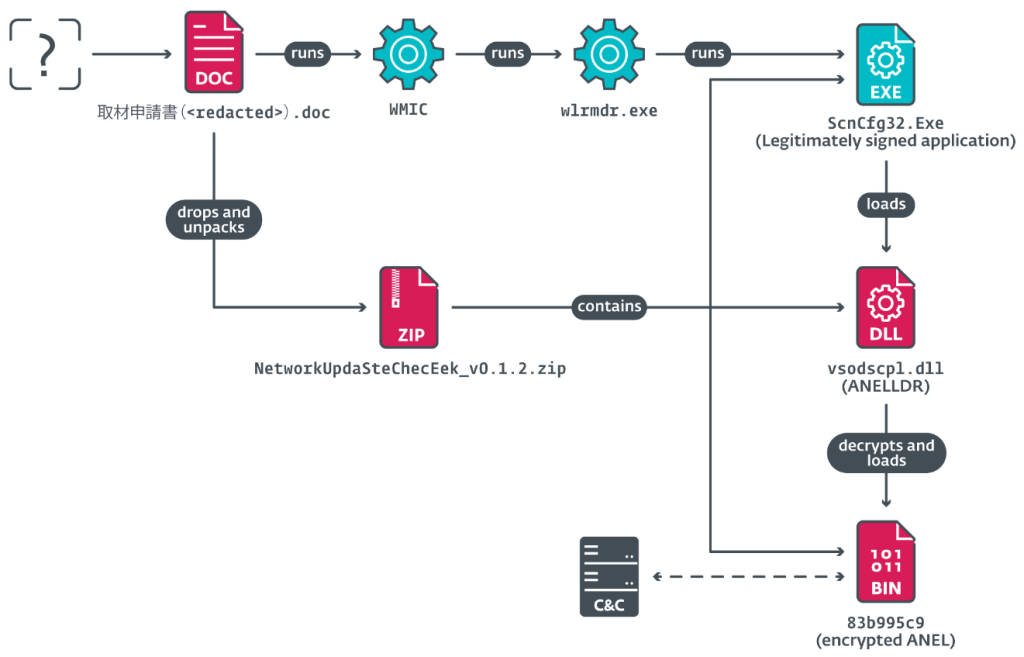
Malicious attachments, disguised as Word documents, launched a complex chain of compromise, ultimately deploying tools for infiltration and data exfiltration.
MirrorFace has enhanced its arsenal, reintroducing the ANEL backdoor, a tool previously associated exclusively with APT10 operations. The backdoor had been abandoned since 2018, but its reappearance suggests renewed development.
This provides further evidence for the debated connections between MirrorFace and APT10 (also known as Red Apollo, Cicada), with ESET concluding that MirrorFace is likely a subgroup under the APT10 umbrella.
A customized AsyncRAT version is deployed using a sophisticated execution chain running in Windows Sandbox to evade detection after being introduced via legitimate 7-Zip executables and libraries, 7z password-protected archives named setup.exe, and batch scripts that unpack and run the RAT.
Visual Studio Code (Microsoft’s free source-code editor) remote tunnels are leveraged for stealthy remote access and code execution, while the gang’s flagship HiddenFace modular backdoor serves as a key persistence mechanism during the later stages of attacks.
The attackers adjusted their tactics based on their targets, using different tools and backdoors according to their objectives. On one machine, data exfiltration focused on personal information, while another targeted deeper network access.