CISA Warns of GitHub Action and Fortinet Authentication Bypass Flaws Ongoing Exploitation
- CISA added two actively abused vulnerabilities to its Known Exploited Vulnerabilities catalog.
- The GitHub Action exploit injects malicious code that allows remote access to sensitive data via action logs.
- The FortiOS and FortiProxy flaw permits unauthorized code or command execution.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical supply chain vulnerability impacting GitHub Actions and a Fortinet flaw to its Known Exploited Vulnerabilities (KEV) catalog.
The flaw that allows authentication bypass using an alternate path or channel could enable a remote attacker to gain super-admin privileges via crafted CSF proxy requests. It affects FortiOS 7.0.0 through 7.0.16 and FortiProxy 7.2.0 through 7.2.12, 7.0.0 through 7.0.19.
The GitHub vulnerability, identified as CVE-2025-30066 with a CVSS score of 8.6, has been actively exploited to access sensitive data via compromised action logs, according to CISA.
The issue affects the GitHub Action tj-actions/changed-files, which can be compromised to include embedded malicious code. Once exploited, the flaw allows remote attackers to access sensitive secrets stored in action logs.
These secrets may include AWS access keys, GitHub personal access tokens (PATs), npm tokens, and private RSA keys.
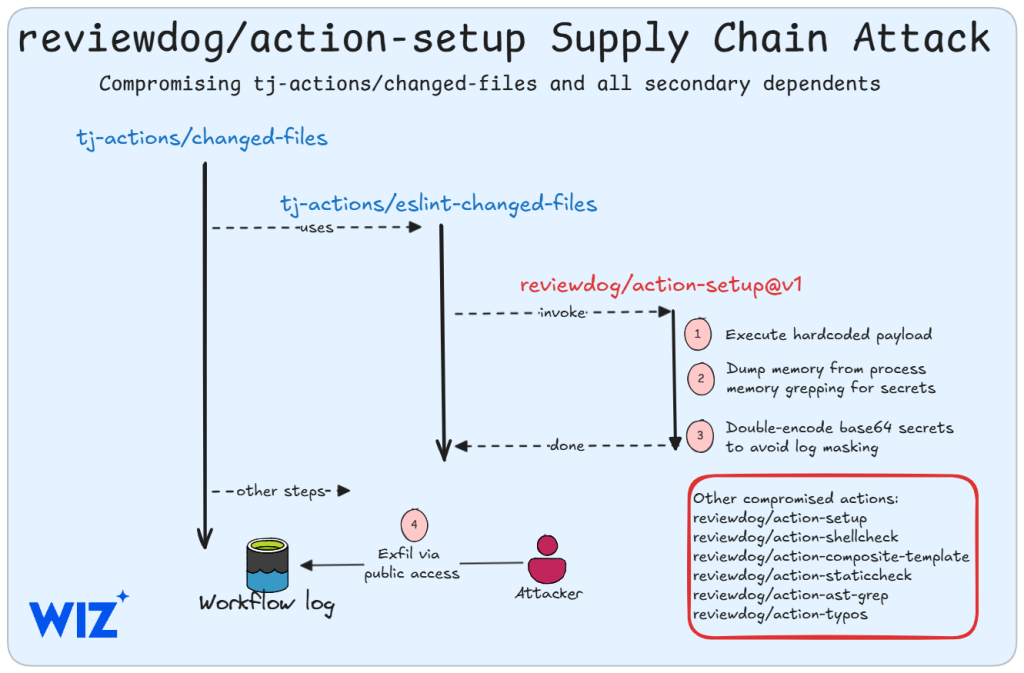
According to research by cloud security company Wiz, the attack appears to be a cascading supply chain compromise. Threat actors initially infiltrated the reviewdog/action-setup@v1 GitHub Action, which is believed to have been then used to compromise tj-actions/changed-files.
Attackers injected a Base64-encoded malicious payload into a file named install.sh, a component of CI/CD workflows.
The compromise of tj-actions/changed-files was traced to a GitHub Personal Access Token (PAT) compromise, enabling malicious actors to alter repository content with unauthorized code. The infiltration may have occurred on or before March 11, 2025.