Amazon Criticized for Hosting Stalkerware Victims’ Data Weeks After Cocospy Breach Alert
- Tech media outlets worry about Amazon delaying action on hosting spyware-stolen data.
- Three surveillance apps were recently found using Cloudflare and AWS infrastructure to store exfiltrated sensitive data.
- The leaked data reportedly includes private photos and other personal details and impacts a total of 3.1 million people.
Amazon is facing criticism for hosting data from Cocospy, Spyic, and Spyzie apps weeks after being alerted to the issue, as the companies behind the spyware continue to upload sensitive phone data of a collective 3.1 million people to Amazon Web Services (AWS) servers.
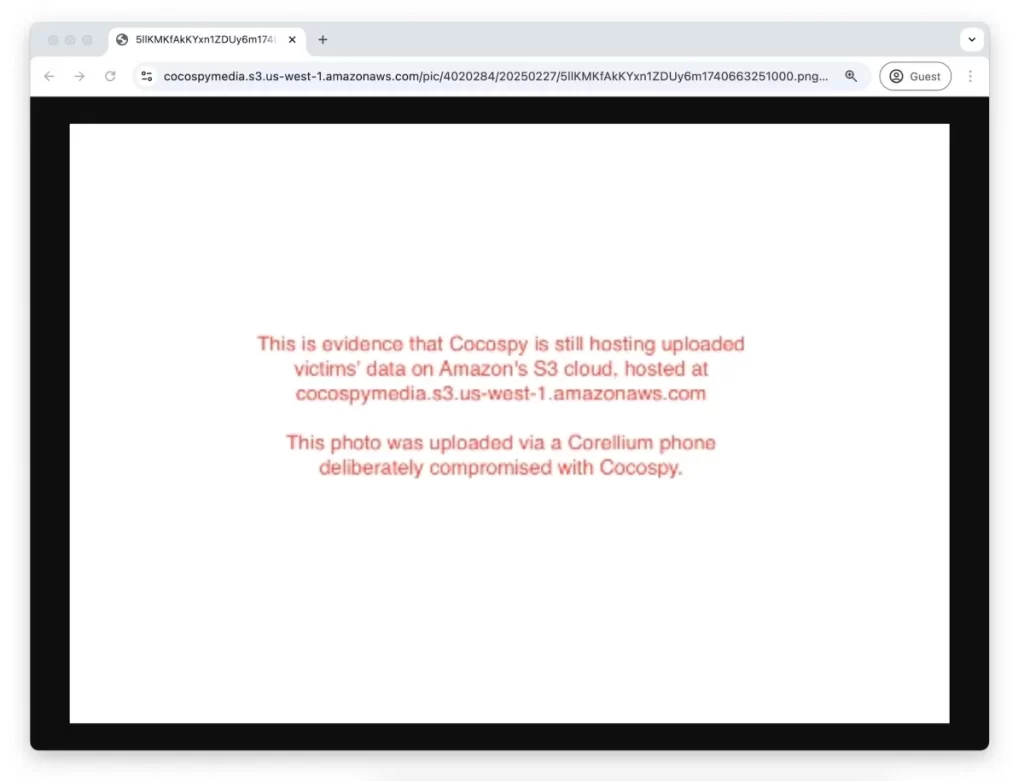
TechCrunch notified Amazon of the stalkerware-hosted data on February 20, providing specific storage bucket information where the data stolen from victims’ phones was being stored.
AWS responded by thanking TechCrunch for the report and provided a link to its abuse report form, but as of mid-March, no decisive action has been taken to disable the hosting servers.
Cocospy, Spyic, and Spyzie are Android apps that share identical source code and a known security flaw that’s relatively easy to exploit, and they are designed to collect phone data secretly. The current vulnerability exploits poorly secured servers used by these apps, allowing external access to exfiltrated data.
The servers used by the apps hinted at Chinese origins and stored data on a mix of Cloudflare and AWS infrastructure.
The Spyzie app was similarly uploading stolen data to its own Amazon bucket, and TechCrunch alerted Amazon about it on March 10.
Amazon states that AWS enforces strict acceptable use policies and responds to reports of misuse. However, the company's procedural response has drawn criticism for delaying action on hosting stolen data.
Stalkerware continues to thrive through direct downloads even though it is banned from official app stores, such as Google Play and Apple's App Store. While some vendors claim the apps are for legal purposes, their capabilities are often abused in ways that violate privacy laws.