More DeepSeek Mirror Websites Appear as Cybercriminals Exploit Its Popularity to Spread Malware
- Hackers keep impersonating AI tools, with even more mirrors of the official DeepSeek and Grok domains.
- Some fake websites distributed info-stealing executable files via downloaded archives.
- Some of these were promoted on social media services as legitimate but have since disappeared.
Cybercriminals exploit the popularity of DeepSeek, a reasoning large language model (LLM), to distribute malware under its guise. DeepSeek, initially lauded as a breakthrough comparable to ChatGPT, has become a target for malicious actors seeking to exploit its widespread appeal.
The attacks involve fake websites mirroring the official DeepSeek and Grok domains, tricking users into downloading malicious files allegedly tied to these AI services.
These campaigns employ sophisticated tactics, targeting individuals and organizations seeking to access AI technology, cybersecurity researchers at Kaspersky have uncovered.
Malicious domains:
- r1-deepseek[.]net
- v3-deepseek[.]com
- deepseek-pc-ai[.]com
- deepseek-ai-soft[.]com
- app.delpaseek[.]com
- app.deapseek[.]com
- dpsk.dghjwd[.]cn
- deep-seek[.]bar
- deep-seek[.]rest
- v3-grok[.]com
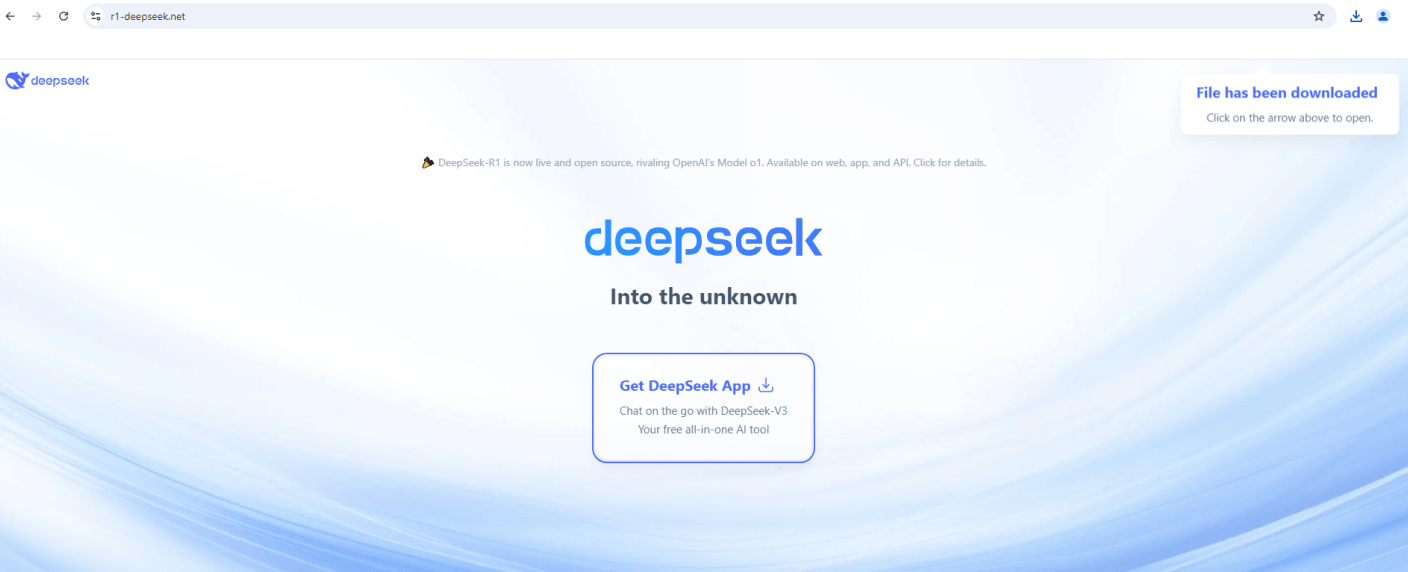
One tactic involves domains such as r1-deepseek[.]net and v3-deepseek[.]com, which mimic the official DeepSeek site but only offer a supposed desktop client. Unlike legitimate software, DeepSeek does not have a native Windows client.
When users click to download the client, they receive a .zip file containing a shortcut that triggers a sequence of downloads. These downloads lead to executing a Python-based stealer script, compromising personal data like browser cookies, login credentials, cryptocurrency wallet information, and sensitive files.
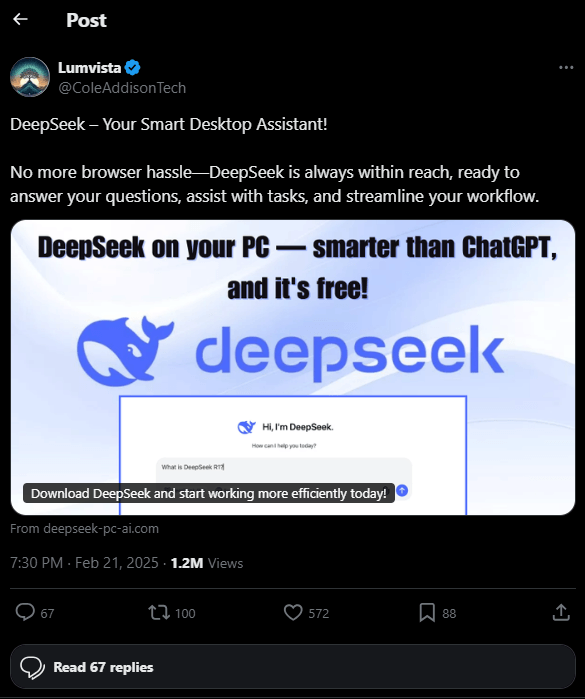
Another attack employs fake websites like deepseek-pc-ai[.]com, distributing malware embedded in installers masquerading as DeepSeek software. Once activated, these installers execute encoded PowerShell scripts, enabling attackers to access victims' devices remotely.
Alarmingly, these fake sites have been promoted on the social network X (formerly Twitter), accumulating over 1.2 million views, likely boosted by bot accounts.
Another variation involves targeting Chinese-speaking users with malicious executables disguised as software for running AI frameworks like Ollama.
Malware deployed through websites such as deep-seek[.]bar includes a Farfli backdoor, hidden using steganography, which establishes unauthorized tunnels for data exfiltration and remote access.
This phenomenon extends beyond DeepSeek, as attackers have similarly used ChatGPT as a lure in past campaigns, targeting both individuals and developers.