Windows Executable Delivers Adware and Info Stealers on Mac Systems
- A new malware targeting Mac OS systems has been detected on the wild.
- The malware is using a Windows executable to override the usual Mac OS protection and security tools.
- The “.exe” file runs thanks to a special bundling of a mono framework in the DMG installer.
As discovered and unveiled by Trend Micro researchers, there’s a new menace for Mac OS users that are able to override the Gatekeeper (Mac’s security and protection system) and deliver adware and info-stealing software. Trend Micro’s telemetry data shows that the majority of infections right now are in the UK, US, South Africa, and Australia. There are various software packages that can possibly contain the malicious executable, with one prominent example being a Little Snitch installer that Mac users download from torrent websites. This is the sample that was analyzed by Trend Micro security researchers as well.
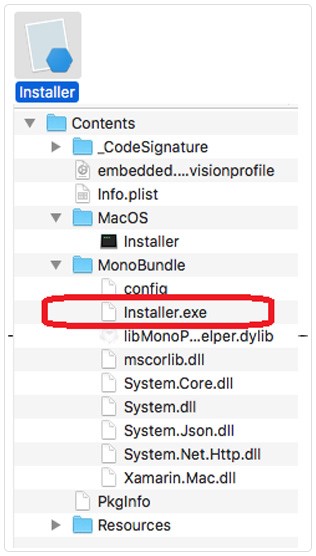
The examination of the downloaded DMG installer file revealed that it contains a Windows executable named as “Installer.exe”. These executables don’t run on Mac OS systems unless they are wrapped with a framework, and in this case, a mono framework that is bundled in the DMG along with everything else makes its execution possible without the user even realizing. As the Gatekeeper is set to ignore Windows executables, the malware runs on the system seamlessly, collecting crucial information about the infected system and sending it to its command and control server. This information includes system details, serial numbers, software versions, and a list of the installed apps.
source: blog.trendmicro.com
Once the preliminary data collection step is concluded, the malware is downloading more malicious applications and saves them in “Library/X2331139MAC/Temp/:”. These apps are masqueraded to look like popular software such as Adobe Flash Player, but in reality, they are just adware. Mac OS users may have trouble locating the source of the trouble that will rise from then on, as everything looks legit in the process and no system alerts are indicating that something is wrong with the downloaded files.
Trend Micro researchers believe that this malware is currently acting as a testbed for them, experimenting with security evasion techniques like the bypassing of digital certification checks. Managing to bundle non-native executables inside a DMG file with a mono wrapper seems to be working fine for now, as all dangers are totally ignored by Gatekeeper. The fact that the infection patterns look random right now is adding credibility in this scenario, as cybercriminals may need to perfect their tools before going full throttle with them. Users are advised to refrain from downloading files and software programs from non-trusted sources such as torrent sites, as these places act as next-gen malware incubators more often than not.
Have you ever had a Windows executable run in your Mac OS system without using an emulator? Let us know of your experience in the comments section below, and help others stay protected by sharing this piece through our socials, on Facebook and Twitter.