Lotus Blossom Espionage Group Expands Cyber Attack Arsenal with Sagerunex Backdoor Variants
- Sagerunex malware and its variants are now part of the Lotus Blossom cyberespionage group.
- Among them are a Zimbra webmail version and a Dropbox & Twitter version to evade detection.
- The new malware campaign focuses on critical sectors across Southeast Asia.
The Lotus Blossom espionage group has once again emerged with a sophisticated campaign. Also known by aliases like Spring Dragon, Billbug, and Thrip, it has been active since at least 2012 and has intensified its operations across Southeast Asia.
Over the past months, the group has targeted critical sectors, potentially disrupting operations and stealing sensitive information, as per a detailed Talos Intelligence security report.
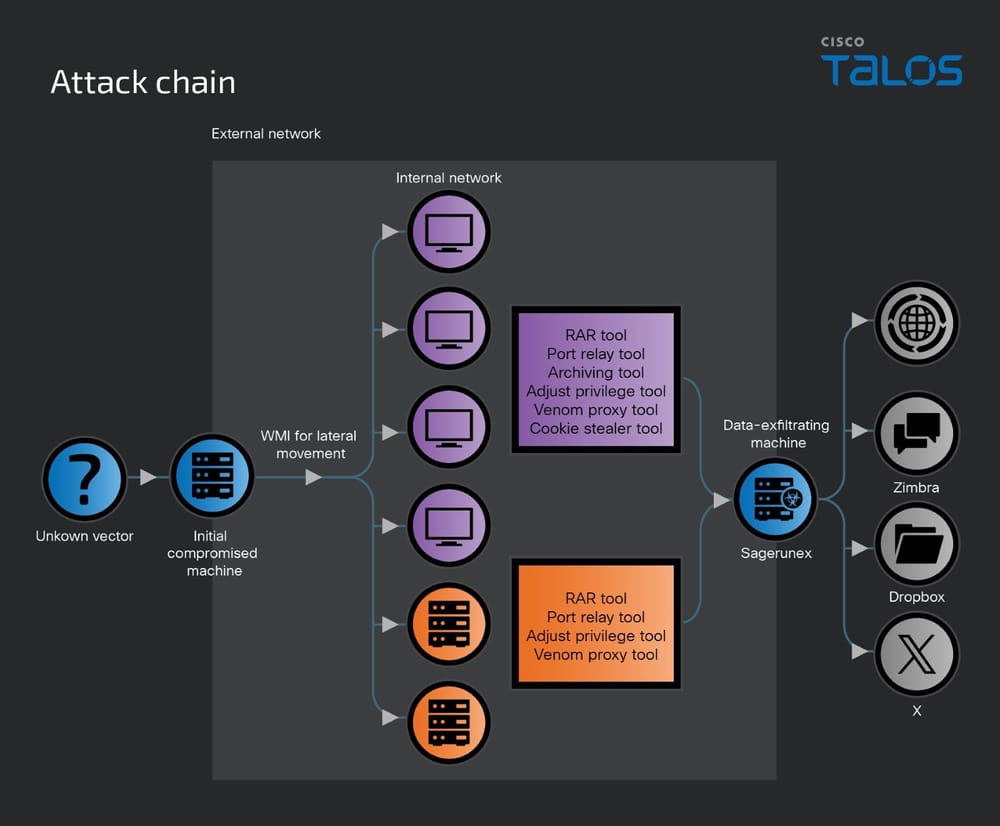
At the heart of their campaign lies the Sagerunex backdoor, a versatile malware tool configured to ensure prolonged access to compromised systems. Key methods include installation within the system registry and persistence tactics that run the malware as a service on infected devices.
The group employs a unique strategy for establishing Command and Control (C2) communication. Beyond traditional C2 servers, they use third-party services like Dropbox, Twitter, and Zimbra open-source webmail to evade detection and sustain C2 connectivity.
A Beta version is designed for debugging and testing, another variant uses Dropbox & Twitter API as C2 services to exploit social media platforms for C2 communication, and one variant improves streamlined malware management by employing the Zimbra API to connect to a legitimate Zimbra webmail services and use it as a C2 channel to exfiltrate victim information.
Lotus Blossom's arsenal is well-stocked with custom-built and repurposed tools, such as a Chrome cookie stealer bundled in Python, the Go-written Venom language proxy solution, a privilege adjuster that enhances malicious processes by leveraging elevated privileges, an archiving and encryption tool.
They also use the port relay tool "mtrain V1.01" based on the existing HTran proxy design and a RAR tool for archiving large data batches before exfiltration.
Using tools such as Impacket, Lotus Blossom simplifies remote process execution and extends its foothold within compromised networks. The group also incorporates reconnaissance commands like ipconfig, netstat, and tasklist to map network activities and potential vulnerabilities.
The group's tactics and tools evolved, indicating a sustained focus on government, manufacturing, telecommunications, and media sectors in the Philippines, Vietnam, Hong Kong, and Taiwan.