Massive Legacy RogueKiller Antirootkit Driver Exploitation Campaign Delivers Gh0st RAT Variant
- A sophisticated cyberattack leverages legacy vulnerabilities and phishing tactics to deploy RATs.
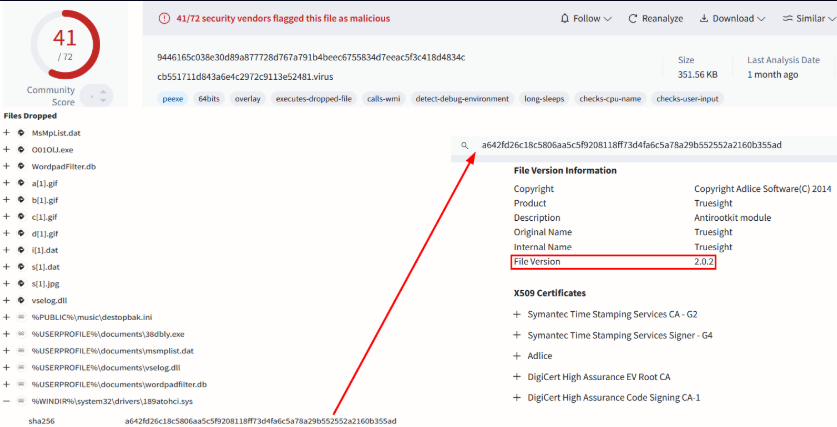
- The attack targets a RogueKiller Antirootkit Driver within the Adlice product suite.
- This malicious campaign has impacted thousands of devices globally, mainly in China.
Cyberattackers have launched a large-scale campaign exploiting an outdated and vulnerable version of the Truesight.sys driver, which is used in the RogueKiller Antirootkit Driver within the Adlice product suite.
Security researchers identified over 2,500 variants of the driver (version 2.0.2) that were specifically manipulated to bypass modern security mechanisms.
This campaign has impacted thousands of devices globally since its discovery in June 2024. At least 75% of known victims are located in China, with the rest spread across regions such as Singapore and Taiwan, the latest Check Point Research (CPR) report says.
The attackers relied on phishing techniques, compromising unsuspecting users through deceptive applications and websites. One example is a phishing website advertising deals on luxury goods containing app icons that redirect to a phishing channel within the corresponding messaging app, such as Telegram, Instagram, WhatsApp, etc.
CPR highlights the sophistication of the campaign, particularly the attackers' ability to exploit a known outdated Truesight.sys version 2.0.2 vulnerability, which permits arbitrary termination of security processes.
Avoiding detection was achieved by bypassing Microsoft's Vulnerable Driver Blocklist and the LOLDrivers protection mechanism and disguising malicious files as well-known applications via multiple phishing vectors like spoofed websites and messaging app links.
The attackers subtly altered file attributes to generate over 2,500 signed driver variants – but maintained their valid signatures, staying under the radar of hash-based detection systems.
The attackers used a multi-stage infection pipeline. The initial stage involved distributing disguised files via phishing, which acted as downloaders for the next stages and the manipulated Truesight.sys driver.
In the secondary stage, files downloaded further payloads and applied persistence mechanisms.
The final stage delivered advanced malware such as a variant of Gh0st RAT, which is designed for unauthorized data access and surveillance. CPR assesses this Gh0st RAT variant to be the same as HiddenGh0st.
The attackers exploited a loophole in Windows' Driver Signature Policy, allowing legacy-signed drivers issued before July 29, 2015, to be loaded on modern Windows systems. This oversight was critical in enabling the malicious use of the Truesight.sys driver.
Additionally, extensive use of the VMProtect tool made forensic analysis challenging, while techniques like DLL side-loading further obfuscated the source of malicious activities.