SonicWall SSL VPN Sessions Exposed to Hijacking Due to Critical Vulnerability
- A critical SonicWall VPN flaw grants an attacker access to key session details.
- An attacker could bypass session validation, logging out the legitimate user.
- Approximately 4,500 internet-exposed SonicWall SSL VPN servers remained unpatched as of February 7.
CVE-2024-53704 is described as a critical vulnerability in certain SonicOS SSL VPN application versions. This flaw enables unauthenticated attackers to hijack active SSL VPN sessions, granting unauthorized access to private networks.
Security researchers at Bishop Fox first raised the alarm about the vulnerability in a bulletin on January 7, warning of its high exploitation potential, and recently published detailed exploitation techniques.
The vulnerability affects SonicOS versions 7.1.x (up to 7.1.1-7058), 7.1.2-7019, and 8.0.0-8035, used across multiple models, including Gen 6 and Gen 7 firewalls and SOHO series devices. Addressing the issue requires updates to SonicOS 8.0.0-8037 or higher, 7.0.1-5165 and higher, 7.1.3-7015 and higher, and 6.5.5.1-6n and higher.
On January 22, following extensive reverse-engineering efforts, Bishop Fox confirmed the viability of SonicWall's initial concerns by crafting an exploit for CVE-2024-53704.
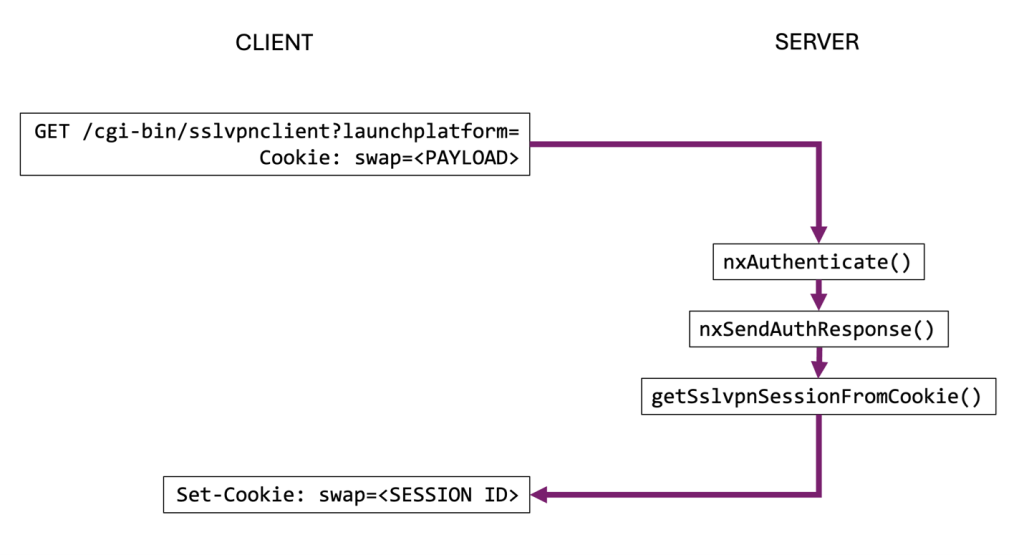
The researchers disclosed that the vulnerability allows an attacker to hijack an active SSL VPN session by sending a specially crafted session cookie with a base64-encoded string of null bytes to the SSL VPN authentication endpoint (“/cgi-bin/sslvpnclient”).
This bypasses session validation, logging out the legitimate user and granting the attacker access to key session details.
Using their proof-of-concept exploit code, Bishop Fox demonstrated how this method reveals usernames, domain information, VPN client configuration settings, and internal network routes accessible via Virtual Office bookmarks.
Additionally, attackers could open VPN tunnels to access sensitive network resources.
"With this exploit, we were able to identify the username and domain of the hijacked session, along with private routes the user was able to access through the SSL VPN," the researchers confirmed.
After providing administrators with time to apply the fixes, Bishop Fox released the full exploitation details on February 12. Alongside this alarming disclosure, the researchers revealed a concerning statistic—approximately 4,500 internet-exposed SonicWall SSL VPN servers remained unpatched as of February 7.
Organizations utilizing vulnerable versions of SonicOS must act swiftly to apply the necessary firmware updates to mitigate this critical security flaw. The involved versions include 7.1.x, 7.1.2, and 8.0.0 across various SonicWall hardware models.
In the past months, Fog and Akira ransomware gangs have compromised corporate networks via SonicWall VPN account flaws exploits. SonicWall addressed it with a fix in August 2024, but the SSL VPN access control flaw is still abused.