Malicious Google Ad Distributes Malware to ‘Cisco AnyConnect’ Users via Cloned University Site
- A malicious Google ad for Cisco AnyConnect ultimately disseminated a remote access Trojan.
- The attackers resorted to cloning a university webpage as part of the decoy strategy.
- The website that pretended to offer a legitimate Cisco download contained a fake installer laced with NetSupport RAT.
Attackers successfully evaded detection by leveraging a malicious Google ad impersonating Cisco AnyConnect. The use of advanced decoy tactics leveraging white pages helped bypass security systems to install NetSupport RAT (Remote Access Trojan).
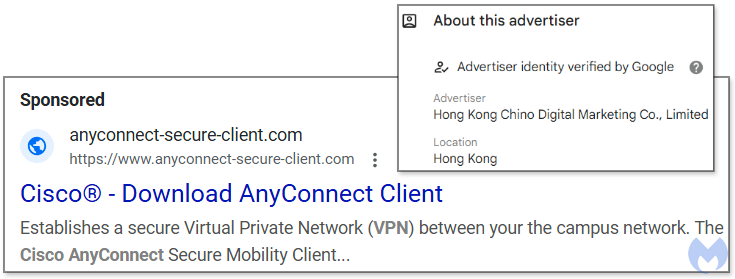
The attack begins with a Google search result for “Cisco AnyConnect,” a widely used remote access tool, returning a seemingly legitimate ad, a recent Malwarebytes report said.
The displayed URL appears credible, showing the domain "anyconnect-secure-client[.]com," but closer examination reveals the domain was registered less than 24 hours before the ad went live.
Clicking the ad initiates server-side validation to identify potential victims. Attackers use checks to filter out non-residential IP addresses, bots, VPNs, and proxies. Only real victims are targeted, ensuring the malicious operation stays under the radar of security systems.
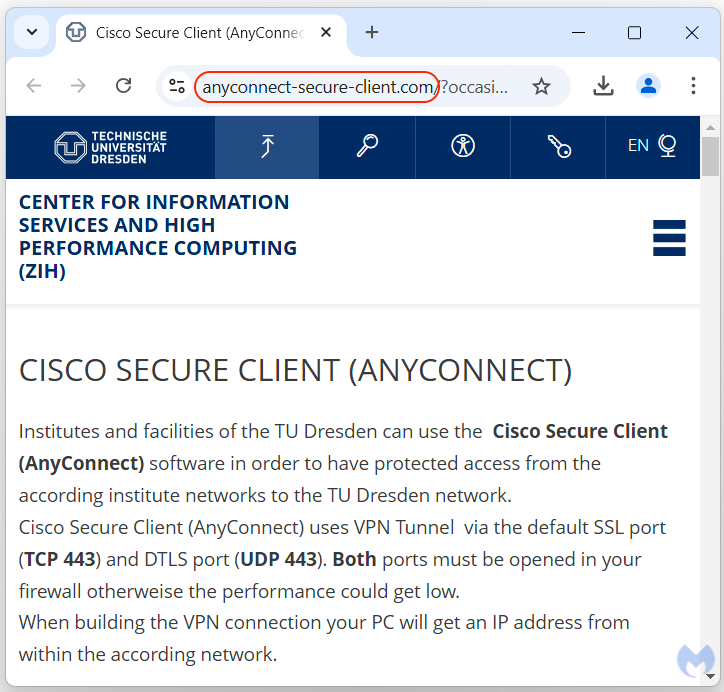
To deceive advertising algorithms and security crawlers, attackers generated a decoy web page resembling a legitimate university website. They copied content from Technische Universität Dresden (TU Dresden), a well-known German research university that uses Cisco AnyConnect. This page was carefully designed to pass as innocuous to detection systems.
The attackers’ mistake, however, was leaving behind a telltale trace within the copy-paste process, such as a cookie opt-in notification that leaked their browser language—Russian. While the decoy was cleverly crafted, such oversights provided key details about the perpetrators.
Genuine users clicking the malicious ad were not exposed to the fake university page. Instead, they were redirected to a phishing site mimicking Cisco AnyConnect’s official website. Here, victims were tricked into downloading a fake installer.
The malicious installer, digitally signed with a valid certificate, executed a file named “client32.exe,” commonly associated with the NetSupport RAT. Once executed, the Trojan established connections to two IP addresses, granting attackers full remote control over the victim's machine.
Although the approach was technically sophisticated, several factors prevented the attack from being flawless. The quick registration of the domain name could have flagged the ad for further scrutiny by Google.
Additionally, the attackers' unintentional inclusion of their language settings in the copied university code exposed a key detail about their likely country of origin. Despite these slips, the malware payload was digitally signed and evaded most detection mechanisms early on, increasing the campaign's chances of success.