Lazarus Group Targets Bitdefender Labs Researchers with Fake LinkedIn Job Offers
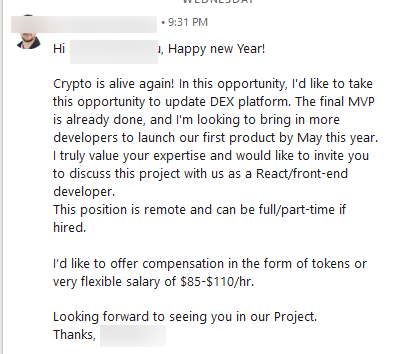
- A Bitdefender Labs researcher got a decentralized cryptocurrency exchange collaboration offer on LinkedIn.
- The social engineering campaign is aimed at ultimately asking victims to execute an MVP that contains hidden malware.
- Hackers rely on a heavily obfuscated script that dynamically loads malicious code from a third-party endpoint.
Bitdefender Labs researchers were the target of a sophisticated cyber campaign orchestrated by the North Korea-linked Lazarus Group (APT38). The operation is designed to compromise security credentials and deploy malware capable of extensive data theft and malicious activities.
These highly complex and multi-staged attacks point conclusively to a state-sponsored group. The Lazarus Group, previously implicated in similar operations, has advanced its toolkit to include sophisticated, cross-platform malware.
The campaign focuses on industry professionals, particularly those in sensitive sectors like defense, aviation, and blockchain, aiming to access classified or proprietary data, as detailed in the Bitdefender report.
APT38 focuses on professionals and organizations under the guise of LinkedIn job offers, which are often related to blockchain projects, cryptocurrency, or financial services and appear legitimate at first glance.
The interaction progresses with requests for resumes or GitHub portfolio links, which serve dual purposes – harvesting sensitive personal data and legitimizing the deceptive recruitment process. Once trust is established, the attackers request victims to execute a supposed "minimum viable product" (MVP) from a distributed code repository.
Attackers package a heavily obfuscated JavaScript file within the downloaded repository that appears innocuous but dynamically loads malicious scripts. This cross-platform infostealer malware subsequently infiltrates victim systems running Windows, macOS, or Linux.
The malware primarily targets cryptocurrency wallets and browser extensions. It collects sensitive data like login credentials, crypto wallet information, and browser payment details. The threat actors initiate their full-scale campaign by exfiltrating this data to attacker-controlled servers.
The campaign uses a suite of Python scripts and modules, each executing distinct malicious functions:
1. “mlip.py” - Hooks into keyboard events to track web browser activity, monitors clipboard content for cryptocurrency wallet addresses, and exfiltrates detected data immediately to command-and-control (C2) servers.
2. “pay.py” - Gathers and uploads system/network details, environment variables, and crypto mnemonics and maintains a persistent communication channel for ongoing attacker commands.
3. “bow.py” - Extracts browser credentials from Chrome, Brave, Opera, Yandex, and Edge and deploys a Tsunami Injector Python script, which connects to pasted URLs to install further payloads.
Additional payloads initiate a range of nefarious activities, such as crypto-miners, keyloggers, and backdoors for reconnaissance and stealing crypto wallet keys, browser passwords, and Discord account credentials. Integration with Tor proxies anonymizes communications between the infected system and the attackers' C2 servers.
Lazarus’ known objectives extend beyond simple data theft. Their operations have historically sought to exfiltrate corporate credentials, classified technologies, and other high-value assets through methods that exploit human trust.