Banking Trojan Campaign Targets Brazilian Windows Users in Finance and Hospitality
- The Coyote Banking Trojan is disseminated via multi-stage operations targeting Windows users.
- Several LNK files contain PowerShell commands that execute malicious scripts and connect to remote servers.
- These campaigns target crypto platforms, financial institutions, and hospitality services in Brazil.
A newly identified malware campaign targets Brazilian Windows users, deploying the Coyote banking Trojan to compromise financial data via a multi-stage attack method. The malware has keylogging, phishing, and real-time screenshot capabilities.
The latest iteration incorporates several updates to enhance its attack success. It now targets financial institutions, cryptocurrency traders, and hotel management systems and interacts with an attacker-controlled server to determine subsequent actions when victims access targeted websites.
The Coyote Banking Trojan can record user credentials and private data, mimic legitimate interfaces via phishing overlays, and capture compromised systems’ screens to visualize the entered private information, according to a recent Fortinet FortiGuard Labs analysis.
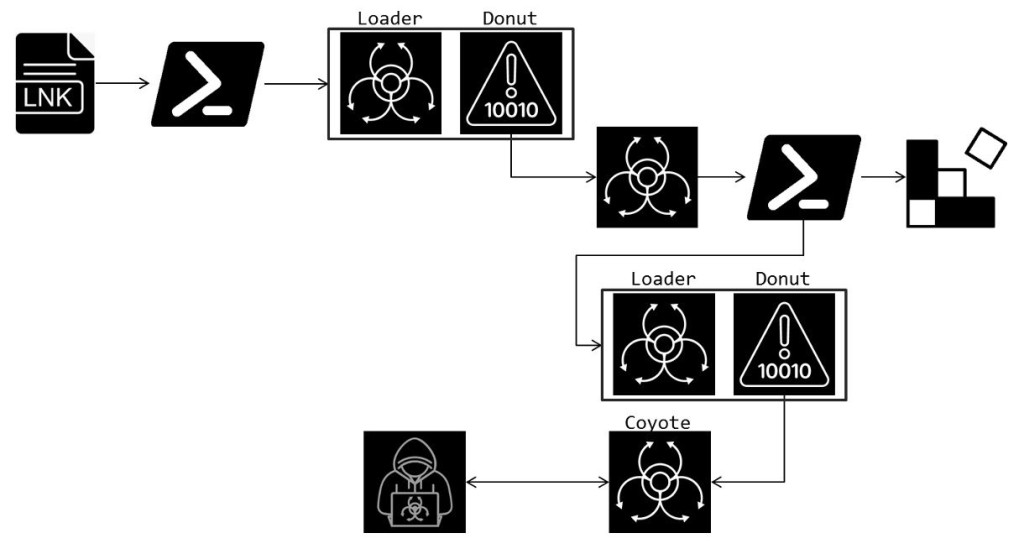
The current version of the infection leverages Windows Shortcut (LNK) files and PowerShell commands as an entry point. The attack commences with an LNK file that executes a PowerShell command to retrieve a secondary payload from a remote server at "tbet.geontrigame[.]com."
The PowerShell script initiates a loader that triggers an interim payload. This step utilizes Donut, a tool that decrypts and executes Microsoft Intermediate Language (MSIL) payloads.
The decrypted MSIL payload modifies the registry to establish persistence, embedding it with a customized PowerShell command to enable the download and execution of further malicious scripts from a Base64-encoded URL.
Upon activation, the banking Trojan collects system information and inventories existing antivirus products. Evading detection is aided by rigorous checks to bypass sandbox and virtual machine environments.
First documented in early 2024, Coyote initially targeted users in Brazil, exploiting over 70 financial applications to collect sensitive information.
Recent campaigns have significantly evolved in complexity, with the latest version expanding its target list to over 1,030 websites across various sectors.
These include cryptocurrency platforms (e.g., mercadobitcoin.com.br, foxbit.com.br) and hospitality services (e.g., augustoshotel.com.br, blumenhotelboutique.com.br).