NoName057(16) and Z-Pentest Launch Cyber Attack on Sewage Treatment Plants in Poland
- The hacktivist groups NoName057(16) and Z-Pentest claimed that they have targeted Poland’s sewage treatment plant.
- They altered the parameters in the sewage treatment system thereby disrupting the service.
- The cyber attack was in support of Russia and against NATO nations that are pro Ukraine in the Russo–Ukrainian conflict.
The cybercriminal groups NoName057(16) and Z-PENTEST have together targeted a Polish entity with an aim to disrupt services.
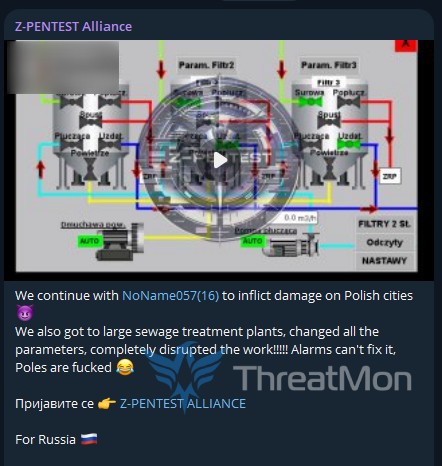
The dark web post by Z-Pentest read,”We continue with NoName057(16) to inflict damage on Polish cities.”
The Z-Pentest group mockingly remarked about targeting the Polish infrastructure and ‘changing all the parameters’ of its sewage treatment plants. This allegedly disrupted its operations despite the alarms going off.
They posted the following image as proof of the Polish sewage treatment plant disruption:
The dark web message ended with the slogan, “For Russia,” followed by the flag emoji of the country. Hacktivists have regularly been posting about targeting pro-Ukraine nations and NATO countries in the Russo-Ukrainian conflict.
The hacktivist group NoName057(16) has been known to launch Distributed Denial of Service (DDoS) attacks often targeting governments, telecommunication companies and transportation websites.
The pro-Russian group launches DDoS attacks that send a flood of requests to a network that slows or crashes it for a certain period of time. However, in this collaborative cyber attack, they allegedly manipulated services posing a threat to people and infrastructure.
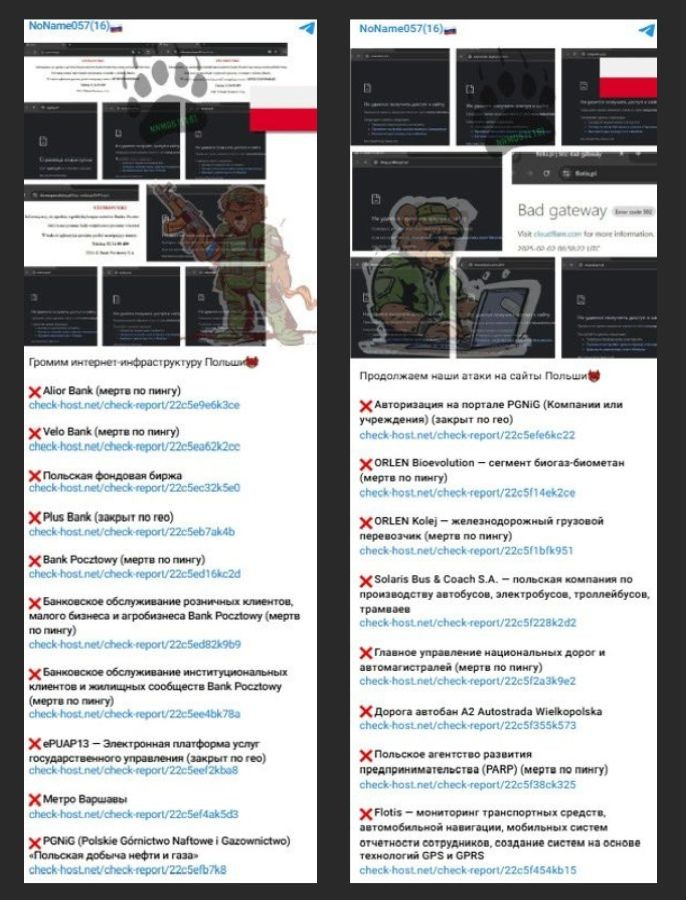
On February 2, NoName057(16) claimed that they launched cyber attacks on the following Poland-based websites:
- Electronic Platform of Public Administration Services (ePUAP)
- Warsaw Metro
- Polish Oil and Gas Mining
- Alior Bank SA
- VeloBank
- Warsaw Stock Exchange
- Plus Bank
- Bank Pocztowy
- Pocztowy24
- PGNiG Bioevolution
- Flotis
- ORLEN Kolej
- Solaris Bus & Coach
- General Directorate for National Roads and Motorways
- Polish Agency for Enterprise Development
- Autostrada Wielkopolska S.A
- Flotis
In addition to the above, the group named several brands owned by the Poland-based company Orlen S. A. on February 1. Some of them were ORLEN administration, ORLEN Asfalt, ORLEN Aviation, ORLEN Budonaft, and ORLEN Energia.
In yet another claim, NoName057()16 mentioned Polish websites and wrote, "We continue to harm the sites of Russophobic Poland."
The group was also reported of boasting about launching a DDoS attack using a car computer system last month.
Meanwhile, Z-Pentest has also collaborated with a new threat actor calling itself ‘Sector 16’ and allegedly targeted the Supervisory Control and Data Acquisition (SCADA) system that manages oil pumps and storage tanks in Texas.