New Lumma Stealer Campaign Leverages Fake CAPTCHA Verifications
- Hackers leverage common CAPTCHA codes to trick victims into running malicious commands on their machines.
- An HTML Application file is downloaded, triggering a multi-stage PowerShell script.
- The campaign’s focus appears to be on the telecommunication sectors in the United States and several other countries worldwide.
A global malware campaign uses fake CAPTCHA verification pages to deliver the Lumma information stealer specially targeting Windows users. This campaign has been detected targeting various industries, including healthcare, banking, marketing, and telecoms.
The new security report underlines the campaign particularly targets the telecom industry, redirecting victims to bogus CAPTCHA pages that initiate a complex attack chain.
Netskope Threat Labs has been tracking the spread of the campaign across countries such as Argentina, Colombia, the United States, the Philippines, and other regions worldwide.
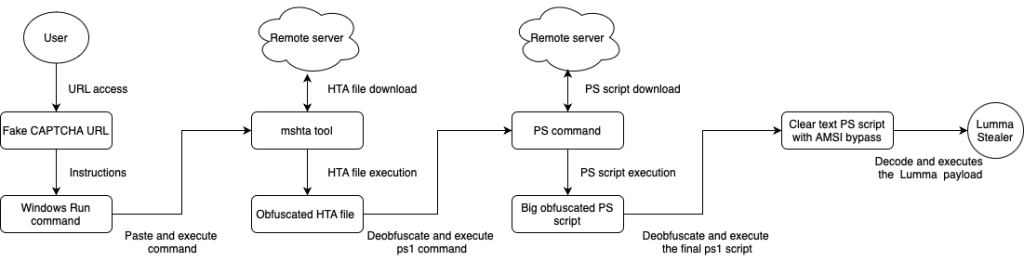
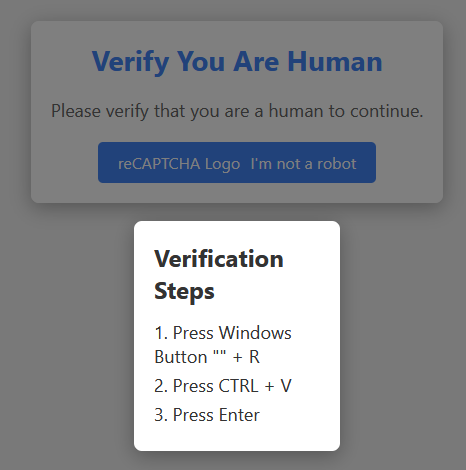
These pages deceive users into copying and pasting a specified command into the Windows Run prompt. The command executes using the native "mshta.exe" binary, enabling the download and execution of a malicious HTML Application (HTA) file from a remote server.
This initial file launches a multi-stage PowerShell – the HTA file executes a PowerShell command that downloads a secondary PowerShell script, which acts as a loader, decoding and delivering the Lumma Stealer payload.
The malware can bypass the Windows Antimalware Scan Interface (AMSI) by requiring user interactions outside the browser context.
The Lumma information stealer operates under the Malware-as-a-Service (MaaS) model, known for its highly active campaigns and complex detection challenges. Its delivery methods and payload structures evolve continuously to enhance resilience against countermeasures.
Additionally, researchers have reported that Lumma is being distributed via several legitimate channels, such as Telegram. Last year, many popular YouTube channel hijacks were reported, distributing RedLine Stealer, Vidar Stealer, and Lumma Stealer.