Over 4M VPN Servers and Home Routers Exposed to Hijacking via Tunneling Protocol Issues
- Individual research highlighted tunneling protocols could expose millions of internet-facing systems worldwide to DDoS and DNS spoofing.
- Researchers identified several protocols prone to exploitation, which include IPIP/IP6IP6, GRE/GRE6, 4in6, and 6in4.
- The vulnerabilities allow threat actors to execute anonymous attacks by abusing hosts’ misconfigured capabilities.
Over 4 million systems across the internet could be exposed to significant security risks due to tunneling protocol flaws. These included VPN servers, home routers provided by ISPs, core internet routers, mobile network gateways and nodes, and Content Delivery Network (CDN) nodes.
The researchers scanned the internet and discovered 4.26 million vulnerable hosts. Alarmingly, over 1.8 million of these were classified as spoofing-capable.
Geographically, the largest concentration of vulnerable hosts was found in China, followed by France. All of these hosts are susceptible to being hijacked for anonymous attack operations.
These findings, published by renowned professor at KU Leuven University Mathy Vanhoef and PhD student Angelos Beitis, were conducted in partnership with VPN testing company Top10VPN.
Tunneling protocols enable networks to transport data between systems, even operating under different standards. For instance, they allow IPv6 traffic to traverse IPv4 networks by encapsulating packets within other packets.
The research demonstrates how these protocols may serve as attack vectors when misconfigured. Vanhoef and Beitis identified several tunneling protocols prone to exploitation, which include IPIP/IP6IP6, GRE/GRE6, 4in6, and 6in4.
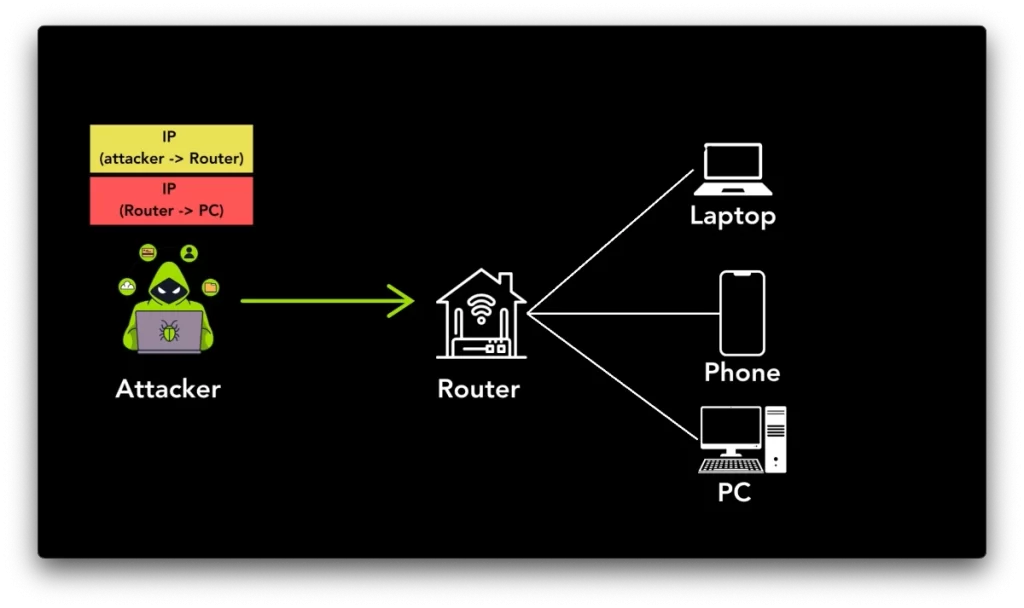
A key issue lies in the misconfiguration of systems, which fail to authenticate the source of tunneling packets and permit attackers to send specially crafted packets to vulnerable hosts.
Some potential attack methods include internal access to internal networks and associated IoT devices and using hosts as one-way proxies, which lets attackers redirect packets through vulnerable hosts, obscuring their own IP address.
Other risks include Distributed Denial-of-Service (DDoS) attacks via weaponized compromised hosts to amplify and launch attacks on other systems and DNS spoofing to redirect victims to malicious sites.
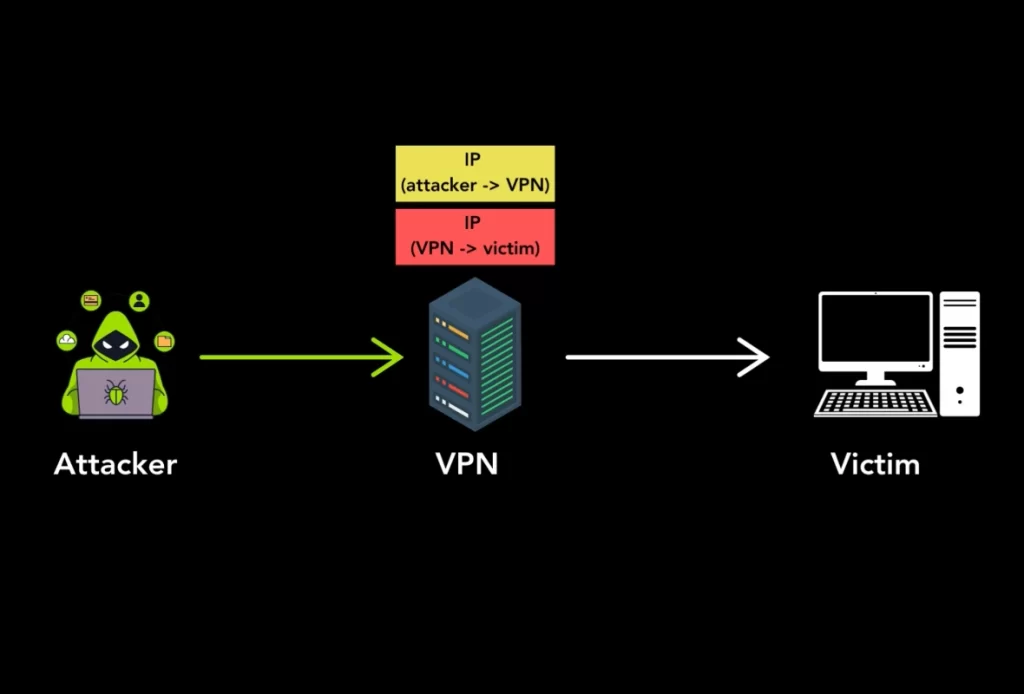
While attackers leveraging basic tunneling misconfigurations can be traced back to the compromised host, the situation becomes significantly more complex with spoofing-capable hosts.
These systems enable attackers to mask the origin entirely via arbitrary IP addresses, which ensures anonymity for the attacker and hampers efforts to identify and secure compromised hosts.
“The outer packet headers containing an attacker’s real IP address are stripped, leaving the compromised host accountable for the attack,” noted the researchers. However, the scenario worsens for spoofing-capable systems as attackers can generate inner packets with any IP address as the source.
The vulnerabilities have been assigned the CVE-2024-7595, CVE-2024-7596, CVE-2025-23018, and CVE-2025-23019 identifiers. The two reports offer technical documentation outlining these weaknesses.
The researchers have proposed mitigation strategies targeting both individual hosts and ISPs, including strengthening packet validation and limiting the acceptance of unauthenticated tunneling traffic.
Recently, Novel Belsen Group published sensitive access details like IPs, private keys, and firewall rules of more than 15,000 FortiGate devices on the dark web.