Operation 99: Lazarus Group Scams Web3 Devs via Fake LinkedIn Jobs Redirecting to Malware Sites
- The Lazarus Group is conducting a money laundering fraud campaign dubbed Operation 99 targeting users on LinkedIn.
- The hackers aim to deploy malware that steals cryptocurrency wallet keys, source code, and configuration files among others.
- Candidates were lured with freelance Web3 developer or cryptocurrency roles.
The Lazarus Group, also known as APT38, targeted LinkedIn users who were interested in freelance Web3 and cryptocurrency jobs. The threat actor relied on social engineering, sent links that redirected to duplicate websites, and stole from the victims’ crypto wallets.
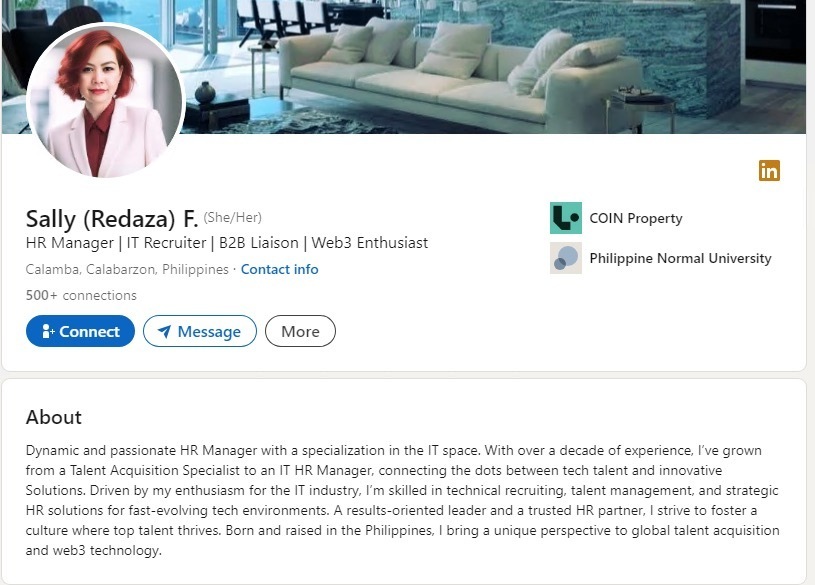
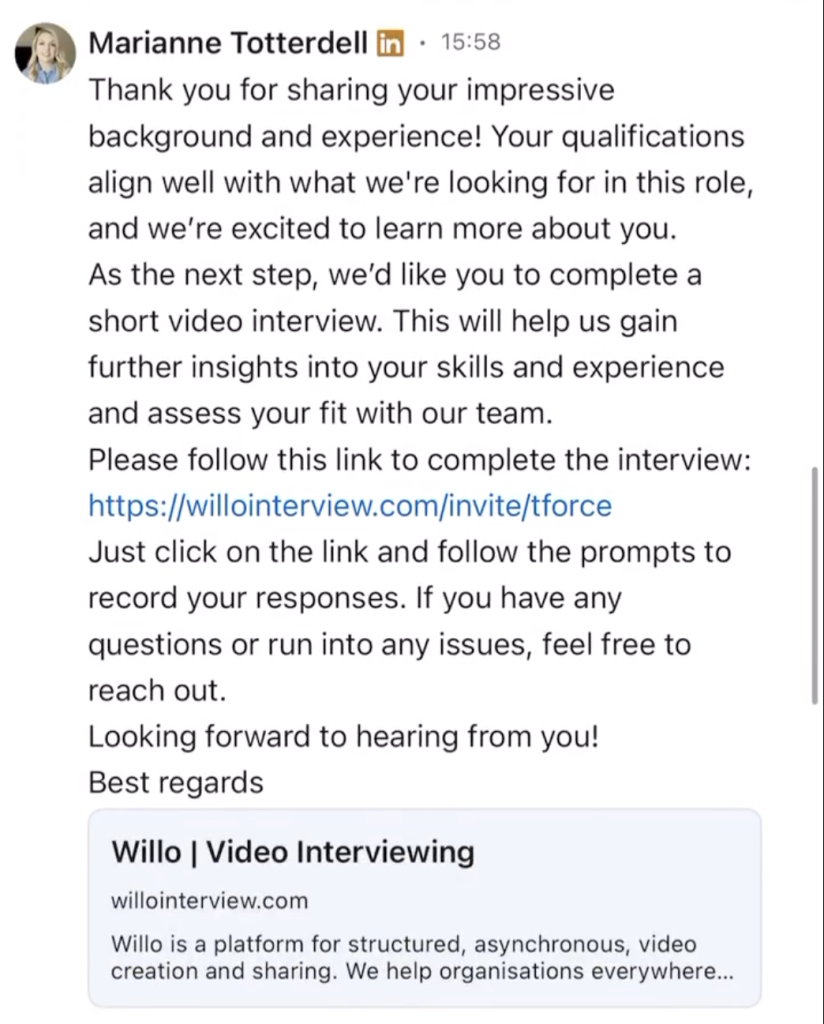
The Lazarus Group has targeted candidates with fraudulent LinkedIn recruitment campaigns in the past. This campaign, named Operation 99, starts with a group member posing as a recruiter and sending interview videos to candidates.
To build trust, they created spoofed or duplicated Blockchain ledger and Bitgetglobal cryptocurrency exchange subdomains they used in the crypto stealing process.
Tweeting about the cryptocurrency trap and URLs, Cybersecurity Researcher Dominic Alvieri shared the following links:
- /VideoForRecruitment[.]com
- /app.VideoForRecruitment[.]com
- /autodiscover.complexassess[.]com
Alvieri shared that threat actors created fake versions of well-known websites and then redirected them to the official URLs.
According to a report by SecurityScorecard, threat actors are attacking developers in Web3 and cryptocurrency because it could create a ripple effect, making way for more victims via its supply chain.
The multi-stage malware they used relied on Main99, a downloader connected to the Command-and-Control (C2) server, and the implant Payload99/73 that allowed access to files and the target's keyboard movements.
Keylogging or monitoring someone’s keyboard strokes was also conducted using the MCLIP implant by Lazarus, which offered access to the copied content in the clipboard. They also used an implant called Brow99/73 that could steal credentials and worked on Windows, Linux, and macOS.
Their advanced C2 servers were hosted by “Stark Industries LLC” and deployed obfuscated Python scripts.
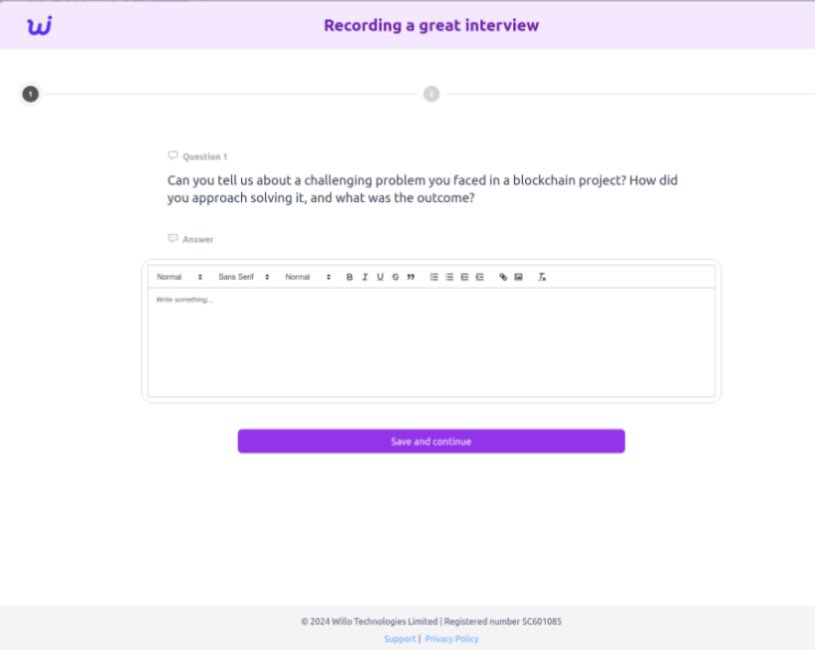
The group has used the platforms Blockchain, BitGet, Willo, Binance, You Hodler, and Robinhood to conduct the operation.
They sent emails with infected links to unsuspecting job seekers. When a user clicks on the link, they get redirected to the official website, adding legitimacy to the email sender – in this case, Lazarus posing as a recruiter.
Users were made to feel they were in a legitimate recruitment process by participating in project tests and code reviews. Eventually, the hackers gained access to cryptocurrency wallet keys, source code, configuration files, API keys, mnemonics, and more.
Victims of Operation 99 have shared their experiences on GitHub with additional details like screenshots, target lists, URLs, and LinkedIn profiles of Lazarus members posing as recruiters.
The cybercriminal group suspected to be associated with North Korea has also been involved in cyberespionage, which is likely how they find their potential victims. So far, Lazarus has stolen over $1 billion worth of cryptocurrency.