HexaLocker Ransomware V2 Displays Smarter and Powerful New Tools, Deploys Skuld Stealer
- The novel and updated version of the HexaLocker ransomware introduces enhanced persistence and encryption tools, such as the powerful ChaCha20.
- Skuld Stealer was added to the latest malware variant along with double extortion.
- Infostealers target browser credentials and history, and cryptocurrency wallet details.
The novel HexaLocker V2 is a more advanced and dangerous iteration of the notorious ransomware, introducing cutting-edge features such as enhanced persistence mechanisms, advanced encryption techniques, and integration with an open-source stealer.
V2 adopted double extortion tactics, an aggressive strategy where attackers steal sensitive data before encrypting it. This dual-pronged approach amplifies pressure on victims by threatening with data loss and public exposure of the stolen information.
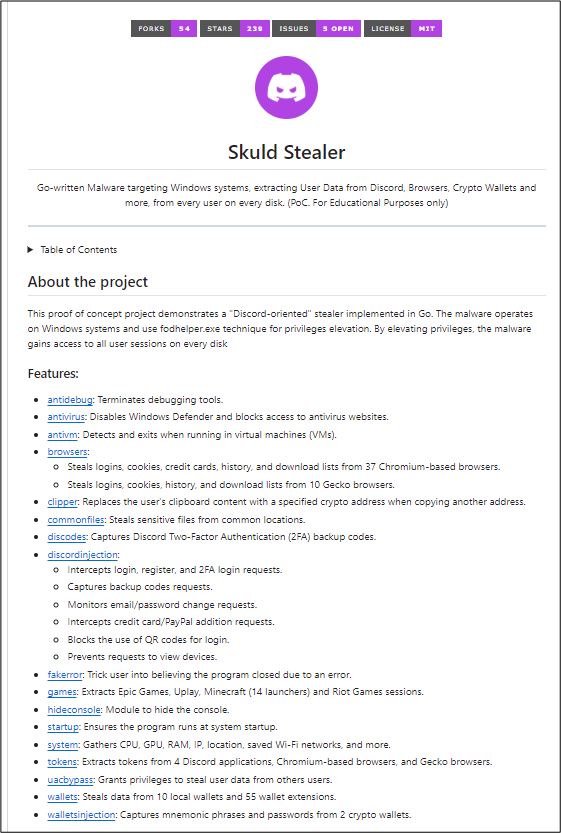
One noteworthy addition to HexaLocker V2’s arsenal is the integration of Skuld Stealer, an open-source information-harvesting tool. Before encrypting files, HexaLocker V2 downloads and executes Skuld Stealer from a remote server.
Skuld targets sensitive data such as browser credentials, browsing history, and cryptocurrency wallet details, primarily from Chromium and Gecko-based browsers like Google Chrome, Mozilla Firefox, and Opera.
The data is exfiltrated after it is compressed in a ZIP archive. This exfiltration phase adds another layer of leverage during ransom negotiations and opens additional revenue streams for attackers through the potential sale of data on dark web forums.
One of the critical improvements in HexaLocker V2, which TrendMicro also added, is its ability to embed deeply into a victim's system. The persistent ransomware replicates itself upon execution and ensures it runs on system reboot.
HexaLocker V2 evades detection via dynamic string obfuscation and advanced encryption techniques. It uses AES-GCM for string encryption, Argon2 for key derivation, and ChaCha20, a high-speed stream cipher, for file encryption. The malware scans for files with specific extensions, targeting documents, images, audio, and video files.
First detected in mid-2024, HexaLocker gained infamy for its straightforward yet effective file encryption tactics. Originally leveraging TOXID for communication and a basic file-encrypting approach, the ransomware disrupted organizations across various sectors.
By late 2024, security researchers began discovering the enhanced HexaLocker V2, whose communication system replaces TOXID with a unique hash-based protocol.
In other news, the infamous LockBit ransomware announced its intention to return in February with the launch of the 4.0 version.