US License Plate Readers Leak Live Streams and Vehicle Data due to Misconfiguration
- Misconfigured license-plate-recognition systems are revealing the live streams of individual cameras across the U.S.
- The data they collect about every vehicle passing them is also exposed to the public internet due to misconfigured Motorola ALPR cameras.
- The sensitive details include high-resolution pictures of vehicles and their license plates, location, time, and more
A critical vulnerability in automated license plate recognition (ALPR) systems in the U.S. has exposed live video feeds and sensitive vehicle data, including vehicle makes, models, colors, and even license plate details.
Over a span of just 20 minutes, an ALPR system in Nashville, Tennessee, captured detailed information from nearly 1,000 vehicles passing by.
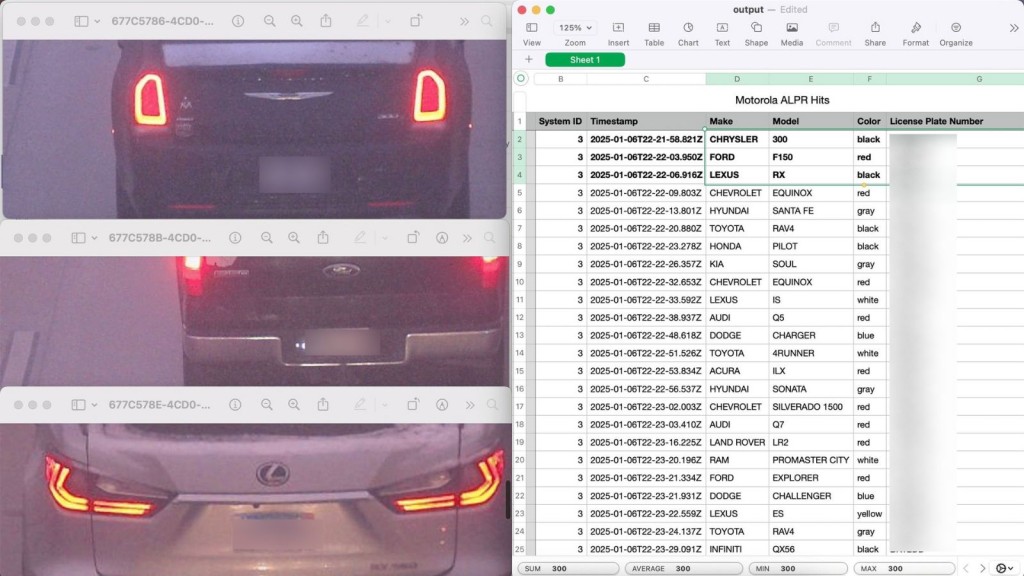
A flaw discovered by cybersecurity researcher Matt Brown revealed that this data, along with live video feeds, had been exposed to the public internet due to misconfigured Motorola ALPR cameras.
Brown, who operates Brown Fine Security, identified security misconfigurations in over 150 Motorola ALPR systems. These cameras, placed in fixed locations across the United States, were effectively broadcasting live video feeds and vehicle data without any form of authentication, making the information accessible to anyone online.
Brown confirmed, along with other technologists, that exposed data included high-resolution photographs of vehicles and logs of license plates as well as location, time, and metadata such as vehicle make and model.
Live footage from these cameras, spanning cities as varied as Omaha, Nebraska, and New York City, was accessible through unique, unsecured streaming URLs. Thirty-seven exposed camera systems were analyzed, revealing that within 20 minutes, nearly 4,000 vehicles had been recorded—some up to three times as they passed multiple cameras.
The exposed ALPR systems, a product of customer-modified network configurations, were inadvertently placed on open, public internet networks rather than private ones. This misconfiguration allowed the data to bypass Motorola’s recommended security settings.
Brown initially discovered the flaw by reverse engineering a Motorola ALPR camera purchased on eBay. Using distinct text from its “404 error” pages, Brown identified IP addresses linked to the vulnerable systems.
Will Freeman, DeFlock creator, made a GitHub script that lets you see the vulnerability in action. As the script page mentions, "Log license plates, vehicle make, vehicle color, and vehicle model to a CSV along with a JPEG image of the vehicle from Motorola ALPRs exposed to the public internet."
Motorola confirmed the issue in a statement, indicating that instances of exposure were tied to non-compliance with their security recommendations. "If customers use our recommended configurations, there is no risk of exposure," said Jehan Wickramasuriya, Motorola's corporate vice president overseeing license plate recognition products.
To address the flaw, Wickramasuriya stated that Motorola is proactively assisting customers in reconfiguring systems and plans to introduce a firmware update with enhanced security measures.
In other news, Volkswagen Group’s automotive software division compromised the precise location of thousands of vehicles across Europe, possibly due to an unsecured server, exposing sensitive vehicle information for several months.