D-Link Routers Flaw Exploited by FICORA and CAPSAICIN Botnets for Full Remote Control
- Two aggressive botnets target documented vulnerabilities in D-Link routers, aiming to gain full remote control of the devices.
- The main focus is on the routers’ Home Network Administration Protocol interface.
- The botnets' capabilities include DDoS attacks, brute-forcing, and eliminating competing malware.
A surge in cyberattacks leveraging legacy vulnerabilities in D-Link routers has been detected, with two aggressive botnets—FICORA and CAPSAICIN—actively exploiting these flaws in outdated and unpatched networking devices.
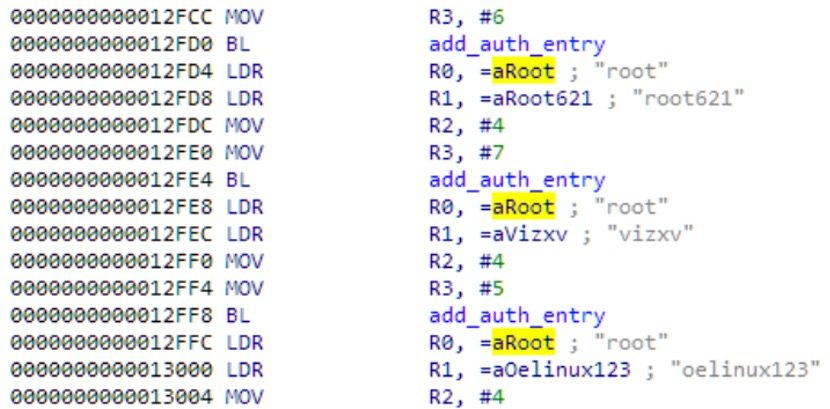
The targeted vulnerabilities primarily revolve around D-Link routers' Home Network Administration Protocol (HNAP) interface. These flaws allow remote attackers to execute malicious commands and gain full control of compromised devices, Fortinet’s Fortiguard Labs reports say.
Some of the exploited weaknesses have been documented under CVE identifiers, including CVE-2015-2051, CVE-2019-10891, CVE-2022-37056, and CVE-2024-33112.
Derived from the infamous Mirai malware, the FICORA botnet employs brute-force tactics to compromise vulnerable devices. It utilizes advanced encryption protocols, such as ChaCha20, to obscure its configuration and command-and-control (C2) details.
Fortinet researchers have noted that FICORA can launch distributed denial-of-service (DDoS) attacks across multiple protocols, including UDP and TCP, making it a highly effective tool for disruption.
Propagation of the FICORA botnet has been traced to servers in the Netherlands, specifically, IP addresses 185[.]191[.]126[.]213 and 185[.]191[.]126[.]248. However, the attacks are opportunistic rather than targeted, aiming to exploit any vulnerable device on a global scale.
Meanwhile, the Kaiten-based CAPSAICIN botnet takes a different approach. It prioritizes rapid deployment across infected devices while aggressively eliminating competing malware to maintain exclusive control of compromised systems.
The resurgence of activity from FICORA and CAPSAICIN underlines the ongoing risks of outdated network hardware. Despite years of warnings and available patches, many organizations and households have failed to address these vulnerabilities, leaving their networks exposed and open to exploitation.
Meanwhile, Androxgh0st botnet replaced Mozi as the dominant malware. By integrating the latter’s functionality, it can target IoT devices and web servers for DDoS attacks, data breaches, and mass surveillance operations.