Cloud Atlas Group Now Uses VBCloud in Its Attacks, Adds VBShower Backdoor
- The cyberespionage group uses the VBShower backdoor as the loader and VBCloud as a new module in their attacks.
- Evading detection is helped by tweaking the RTF and HTA payload downloads.
- The multi-stage infection chain aims to steal data from victims’ devices, and phishing emails remain the initial access point.
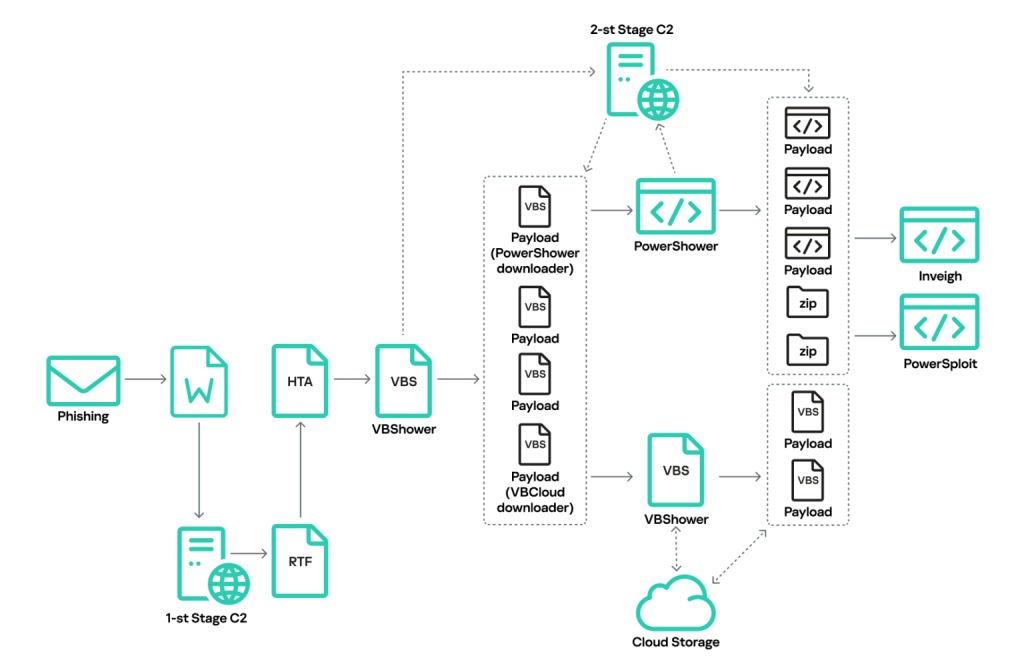
Cloud Atlas is using a previously undocumented toolset in its campaigns while continuing to rely on phishing emails as its primary attack vector. The threat actor focuses on minimizing detection and now delivers the VBCloud backdoor.
These emails contain malicious documents exploiting a flaw in Microsoft Word's formula editor (CVE-2018-0802). The cyber-espionage group, active since 2014, can then download and execute malicious code, as per Kaspersky’s latest security report.
When a victim opens the malicious document, the file downloads a template, formatted as an RTF document, from a remote server controlled by the attackers. This RTF file contains a formula editor exploit that downloads and executes an HTML Application (HTA) file from the same command-and-control (C2) server.
Cloud Atlas has implemented restrictions to minimize detection. The RTF and HTA payload downloads are time-restricted and tied to specific victim IP addresses, ensuring only requests from target regions are allowed.
The HTA file launches and writes multiple files to the disk, which are components of the VBShower backdoor. VBShower then facilitates the download and installation of another backdoor known as PowerShower.
VBShower, previously used alongside the PowerShower module to facilitate infiltration, now delivers the VBCloud backdoor, first detected in active use in August 2024. Using VBShower and PowerShower modules, VBCloud can download and execute plug-ins, establish secure communications with C2 servers, and exfiltrate sensitive files.
Cloud Atlas groups have updated their toolkit, deploying numerous variations of VBCloud to evade detection. These backdoors allow for advanced reconnaissance, data theft, and further network exploitation. Specifically, VBCloud also collects system data and steals files carrying extensions of interest, such as DOC, DOCX, XLS, PDF, RTF, and JPG.
A sample attack observed in September 2024 illustrates the operation of Cloud Atlas's updated toolkit. Once initiated, VBShower and PowerShower module execution led to an in-depth infiltration of the local network. PowerShower facilitated reconnaissance in the targeted systems, while VBCloud successfully extracted data and remained covert.
VBCloud also managed the theft of business-critical documents. The malware's use of public cloud services for staging and exfiltration highlights an added layer of sophistication aimed at blending malicious traffic with legitimate network activity.
In September, Lazarus Group was seen delivering a new backdoor that targets professionals from the aerospace and energy sectors worldwide, using fake job offers as a lure and contacting victims via email and WhatsApp.