Mongolock Ransomware is Taking a Straight Forward Deletion Approach
- Mongolock skips the server storing part and simply deletes all key user files on the infected system.
- People who are falling victims are still paying the ransoms in Bitcoin, hoping to get their files back.
- Threat actors are giving only 24 hours to the victims, creating a sense of urgency.
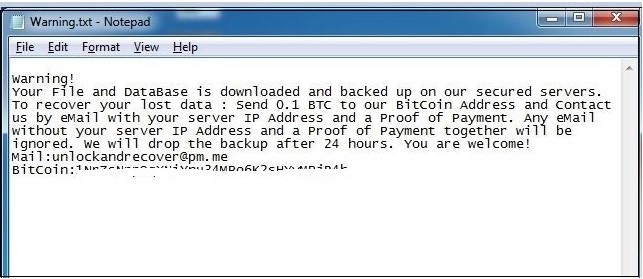
Mongolock is one nasty piece of ransomware that has been targeting unprotected MongoDB databases and asking for around $3600 for each instance. As previously observed, the ransomware was exporting the database information to its command and control server, and then deleted the local files instead of encrypting them. According to a recent analysis and report by Quick Heal researchers, Mongolock is now skipping the exporting and storing part, and simply deleted the local files. The ransom note is not making this known to the victims of course, as they are still promised the restoring of their data if they pay the ransom.
image source: blogs.quickheal.com
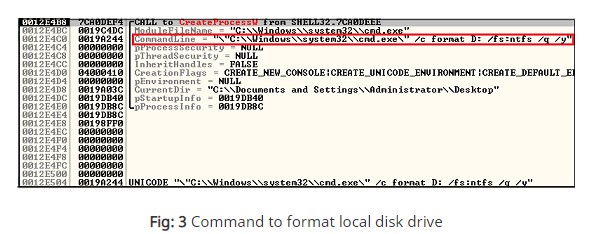
Mongolock starts its activity by scanning the user’s critical folders like the “Documents”, “Videos”, “Desktop”, etc. It then runs the “format.com” command on all these folders as well as any hard drives that have been detected. Using Wireshark, the Quick Heal researchers have captured some form of communication between the ransomware and the CnC server, but it was only limited to sending some identification data about the victim’s machine. No files are exported and stored there, so there’s no way for the attackers to restore the deleted files.
image source: blogs.quickheal.com
According to the findings of other researchers, Mongolock has received quite a lot of ransom payments from victims in the previous months, in the form of Bitcoins, while their CnC sits behind a Tor Network. This means that the actors have not been traced yet, so security firms are monitoring its activity and warning people not to pay, especially in this case. To protect MongoDB databases against Mongolock, all you need to do is to disable “remote access” and enable “authentication” steps. MongoDB has published a detailed checklist regarding the steps that administrators need to follow.
As for the non-database users who want to avoid falling victims of Mongolock, updating their antivirus solution regularly, taking backups of important data in external drives or the cloud, and disabling their office suite macros are all steps to the right direction. If the prevention measures fail, note that restoring deleted files is possible for hard disk drives and by using specialized software tools like EaseUS for this purpose, as long as no overwriting has occurred. This means that if Mongolock deleted your files, you should immediately try to restore them and not continue using the system, writing new data on the disks.
Have you had any experience with Mongolock? Let us know of the details in the comments section below, and help us warn people by sharing this story through our socials on Facebook and Twitter.