Infamous Raccoon Stealer Operator Pleads Guilty, Gets 5-Year Sentence in Federal Prison
- Ukrainian Raccoon Stealer Maas operator was sentenced to five years in federal prison after pleading guilty.
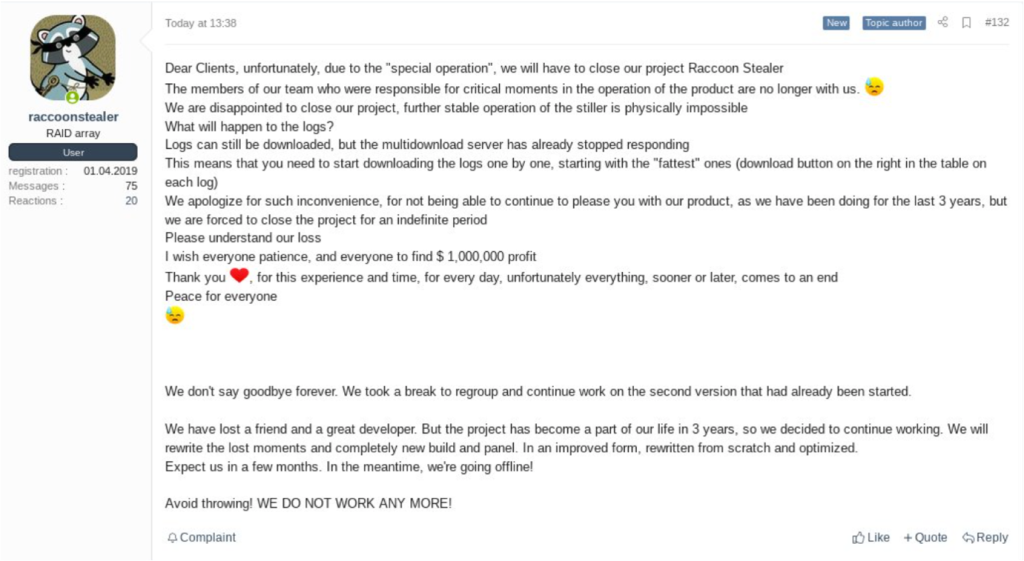
- The Raccoon Stealer cybercrime gang announced the suspension of their operations in 2022 around the individual’s arrest.
- Yet, it has been revived several times since then, emerging with improved data theft capabilities.
Ukrainian national and notorious malware operator Mark Sokolovsky, also known by aliases such as raccoon-stealer, Photix, and black21jack77777, was sentenced to five years in prison for operating Raccoon Stealer as a MaaS (malware-as-a-service).
Under this model, the malware was rented to other cybercriminals for $75 per week or $200 per month, according to recently unsealed court documents.
The malware is a highly sophisticated infostealer designed to compromise infected devices and steal a wide range of sensitive information. This includes user credentials, cryptocurrency wallets, credit card data, email information, and data from dozens of applications.
The stolen information was later used for further criminal activities, including fraud, identity theft, and ransomware attacks.
Sokolovsky's arrest unfolded in March 2022 when Dutch authorities apprehended him in the Netherlands. A coordinated effort between the FBI and law enforcement agencies in the Netherlands and Italy led to the dismantling of Raccoon Stealer’s infrastructure shortly after.
Simultaneously, the Raccoon Stealer cybercrime gang announced the suspension of their operations, attributing the pause to the death of a lead developer during Russia's invasion of Ukraine. However, despite these claims, newer versions of Raccoon Stealer reemerged in subsequent months, boasting even more advanced data theft capabilities.
Sokolovsky was ultimately extradited to the United States in February 2024, following his indictment in October 2022 on charges of fraud, money laundering, and aggravated identity theft. A year later, he pleaded guilty to his involvement and agreed to pay $910,844.61 in restitution.
“The infostealer was responsible for compromising more than 52 million user credentials, which were then used in furtherance of fraud, identity theft, and ransomware attacks on millions of victims worldwide," according to the FBI.
Following the dismantling of the Raccoon Stealer infrastructure, the FBI launched a website to assist victims in ascertaining whether their data was compromised through the malware. If affected, users will receive an email containing further guidance and resources.
Infostealers have become even easier to disseminate, as attackers have been seen distributing Lumma Stealer via Telegram, bypassing traditional detection mechanisms in India, the U.S., and Europe.