TA397 Delivers Espionage RATs wmRAT and MiyaRAT in the Turkish Defense Sector
- The Bitter APT actor, tracked as TA397, was seen targeting a Turkish organization in the defense sector with espionage RATs.
- Starting with spearphishing, the hackers ultimately implemented the TA397-specific malware wmRAT and MiyaRAT.
- The campaign used fake World Bank infrastructure project attachments as a lure.
Advanced persistent threat (APT) actor TA397, also known as Bitter, deployed a sophisticated attack chain targeting a Turkish defense sector organization. This operation utilized spearphishing tactics and advanced payload delivery techniques to distribute remote access trojans (RATs) engineered for intelligence gathering and exfiltration.
Given its scope, Proofpoint assesses this campaign as contributing to intelligence-gathering efforts that are aligned with South Asian governmental objectives.
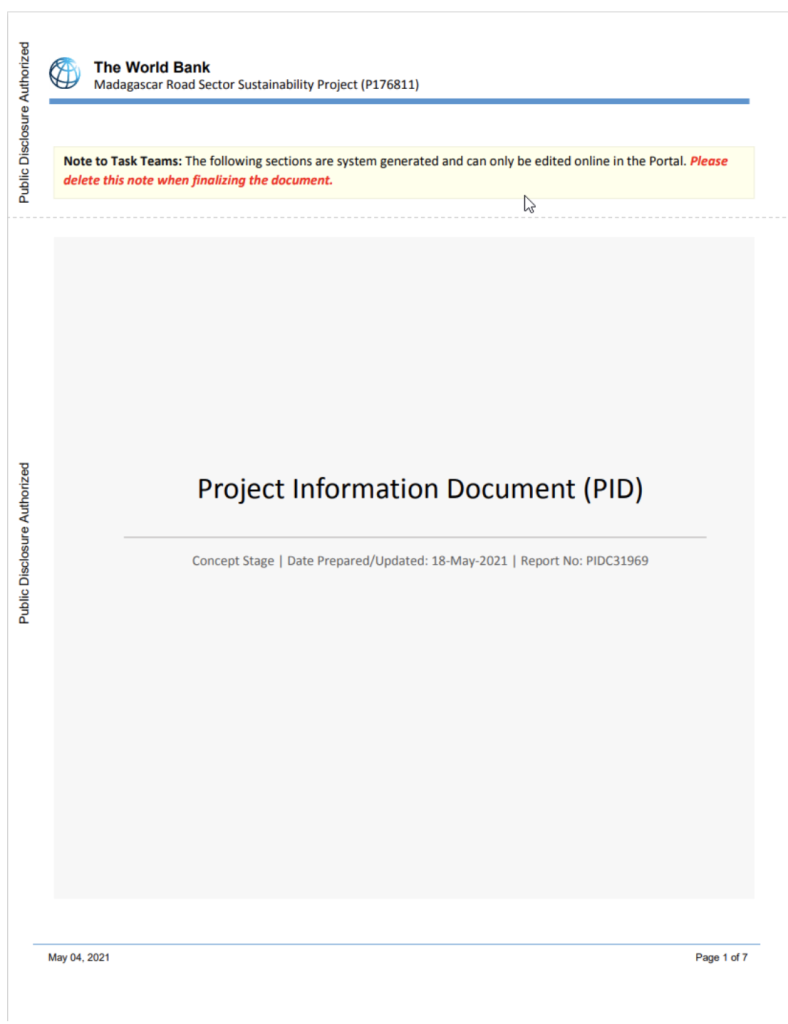
Proofpoint researchers observed the attack on November 18, 2024, and it involved spearphishing emails originating from a compromised government account. The emails targeted a Turkish defense organization with a lure titled “PUBLIC INVESTMENTS PROJECTS 2025 _ MADAGASCAR,” referencing a World Bank infrastructure project.
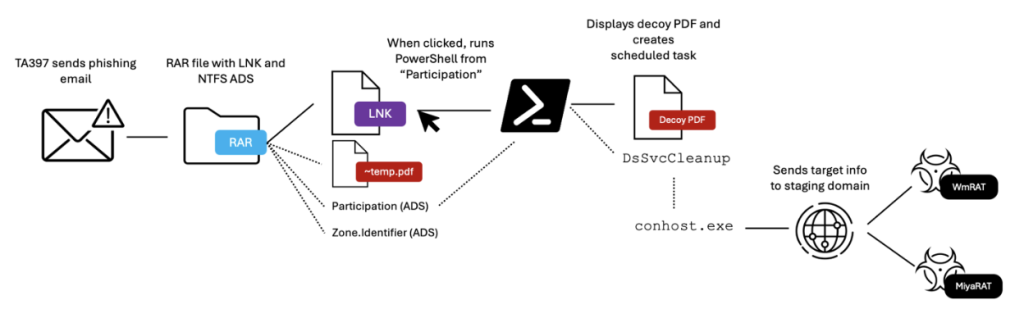
The email attachment contained a RAR archive packed with malicious artifacts, including a shortcut (LNK) file disguised as a PDF and alternate data streams (ADS).
TA397’s strategy leverages RAR archives as a delivery mechanism, utilizing the LNK file to execute PowerShell commands. This triggered a scheduled task, "DsSvcCleanup," which transmitted host system data to the domain jacknwoods[.]com and executed further payloads.
The campaign also utilized tactics to disguise its malicious components—including hidden ADS within the archive—to deceive users.
The attack demonstrated advanced usage of NTFS alternate data streams (ADS), specifically the “Participation” and “Zone.Identifier” streams. The Participation stream contained a base64-encoded PowerShell blob that manipulated the victim’s defenses while creating a scheduled task.
ADS are a core component of NTFS file systems, allowing additional data streams to attach invisibly to files hidden from standard Windows extraction tools like WinRAR but discernible via 7-Zip.
TA397’s ultimate objective was the deployment of two espionage-focused RATs—WmRAT and MiyaRAT. Both malware families serve as tools for gathering intelligence on the targeted systems, supporting campaigns likely associated with South Asian government interests.
WmRAT, written in C++, offers robust capabilities for remote operations, including file uploads and downloads, directory enumeration, command execution, and screenshot capture. MiyaRAT, another C++ implementation, introduces newer features, including an encryption algorithm to obscure its command-and-control (C2) domain, decoded as samsnewlooker[.]com.
In October, a concerning phishing campaign surfaced, leveraging the open-source Gophish framework to deliver DarkCrystal RAT (DCRat) and a new variant known as PowerRAT to Russian-speaking users.