Researchers Uncover “EagleMsgSpy,” Used by China’s Public Security Bureaus
- EagleMsgSpy is a Chinese actively developed spyware, in use since 2017.
- The spyware can collect and exfiltrate extremely sensitive information.
- It’s believed that a private company has developed this app for China’s police.
Cyber-security researchers at Lookout have identified a previously unknown Android spyware believed to be used by law enforcement agencies in China with highly intrusive data logging capabilities. The researchers have obtained several variants of the Android-targeted tool. However, internal documentation also shows evidence of an iOS version.
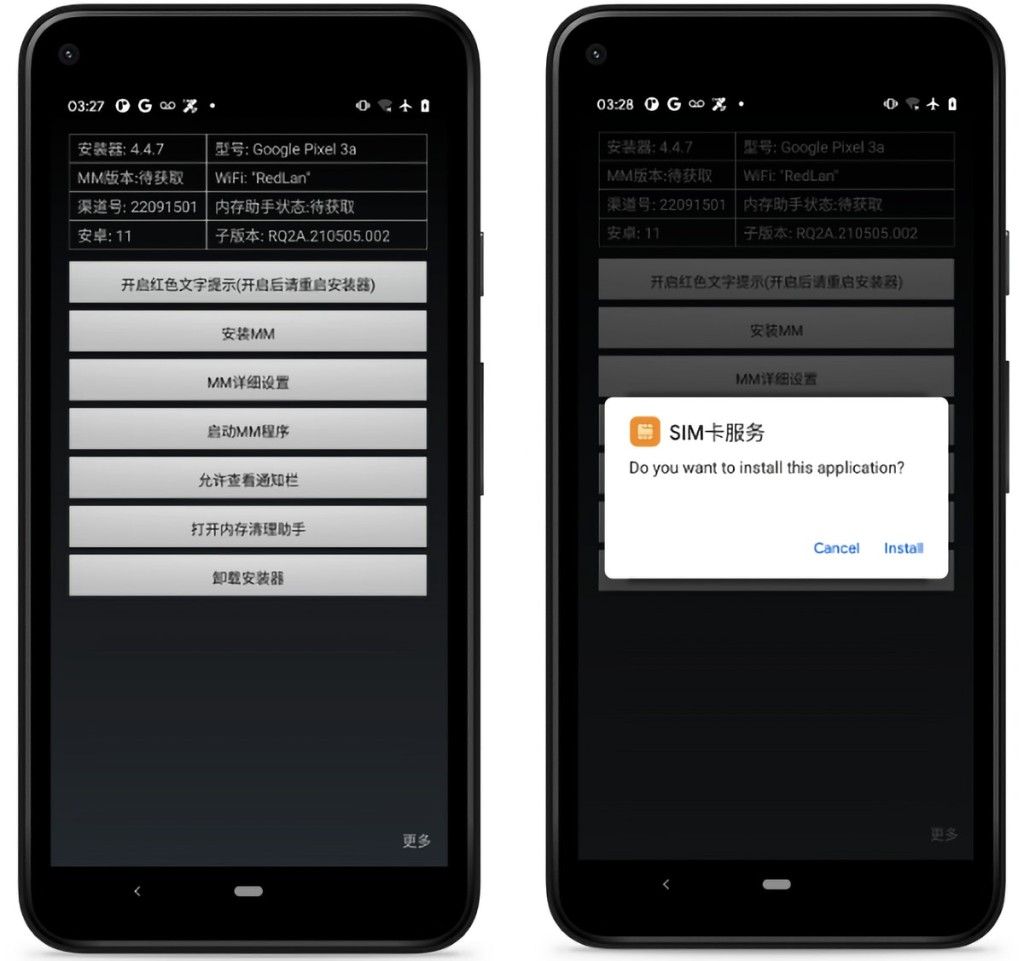
Called “EagleMsgSpy,” this spyware has two modules: an installation APK file and a surveillance client that runs heedlessly. Since there’s no trace of this APK file on the Google Play Store or other app stores, the app is probably installed through physical access, which can happen during confiscation, which isn’t rare in countries like China.
Once installed, the surveillance app can collect an extra-wide range of data about the victim’s device, including the following:
- Incoming messages and notifications.
- Messages from apps like QQ, WeChat, WhatsApp, Telegram, and Viber.
- Screen recording through the Media Projection service.
- Screen captures (screenshots).
- Audio recordings using the device’s microphone.
- Call logs, SMS messages, and device contacts.
- List of installed applications.
- Wi-Fi and Internet connectivity details.
- GPS coordinates.
- Files stored in external storage.
- Browser bookmarks.
Once data is collected, it is hidden in a directory of the device's file system. The data files can be compressed and password-protected anytime before being uploaded to the command-and-control (C2) server. Furthermore, the malware features an administrator panel called “Stability Maintenance Judgment System.”
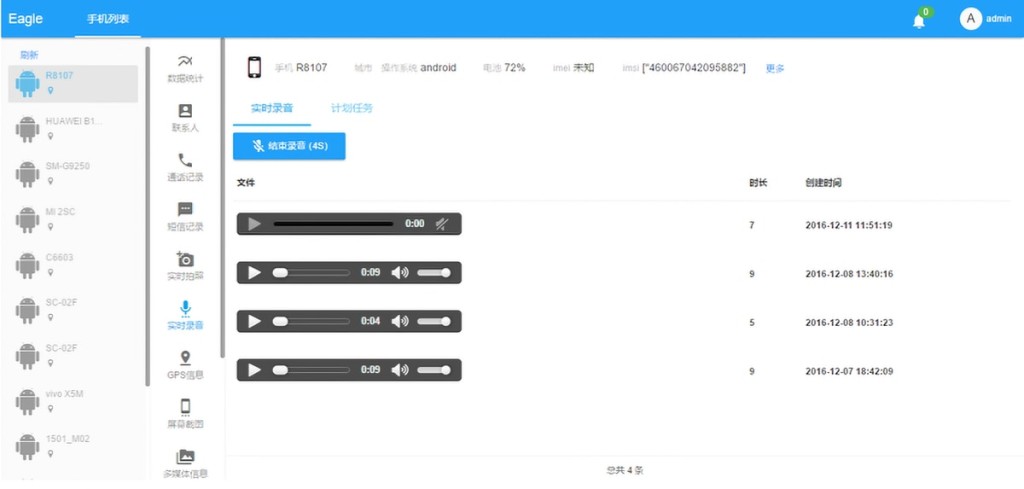
Based on the app’s newly discovered internal documentation, EagleMsgSpy’s admins can use the admin panel to collect graphs and heatmaps of geographical data, collect the top 10 most frequently contacted individuals, trigger real-time photo collection, block incoming calls and messages, initiate real-time audio recordings, and more.
Lookout’s researchers have also uncovered ties to a private Chinese technology company called Wuhan Chinasoft Token Information Technology Co., Ltd. The IP address used by one of the C2 servers, promotional material, and internal documentation revealed this link. In addition, infrastructure overlaps were also found that point to the use of EagleMsgSpy by public security bureaus in mainland China.
Lookout’s researchers have found links to the Yantai Public Security Bureau and its Zhifu Branch. Historical IPs also overlap with domains used by bureaus in Dengfeng and Guiyang.
In other recent news, the US Department of Justice has unsealed an indictment against a Chinese hacker who managed to exploit 81,000 Sophos firewalls, some of which were employed to protect critical infrastructure systems of US companies.