Visual Studio Code Tunnels Exploited by Chinese Hackers to Target European IT Companies
- The abuse of Visual Studio Code is still rare in the world of cyber-security.
- Chinese hackers have reportedly used VSCode to target B2B IT organizations.
- This operation lasted three weeks and happened in June-July 2024.
Visual Studio Code tunnels enable developers to maintain connections to remote systems via Microsoft’s Remote Development tools using Microsoft Azure infrastructure. As such, they provide a secure way for developers to execute commands and access files on remote devices. However, according to a newly published report, VSCode tunnels can also be exploited maliciously.
Sentinel Labs and Tinexta Cyber report that Chinese hackers abused VScode tunnels between June and July 2024 in an operation dubbed “Operation Digital Eye.” The cybersecurity researchers have detected and blocked these activities and have now shared more detailed information about this new APT tactic.
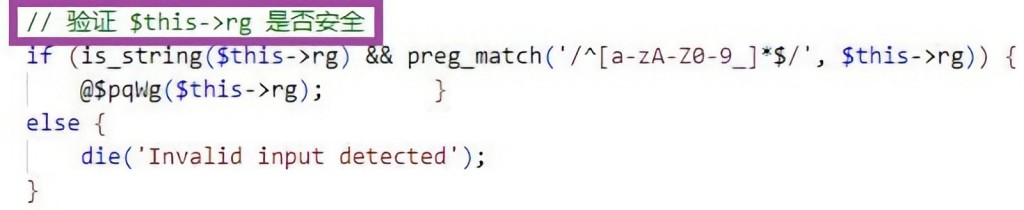
The malicious actors used the SQL injection tool called ‘sqlmap’ to gain initial access to the target systems, followed by using a PHP-based webshell to gain the ability to execute commands remotely and introduce additional software/code payloads. Furthermore, the hackers used RDP and pass-the-hash attacks for lateral movement.
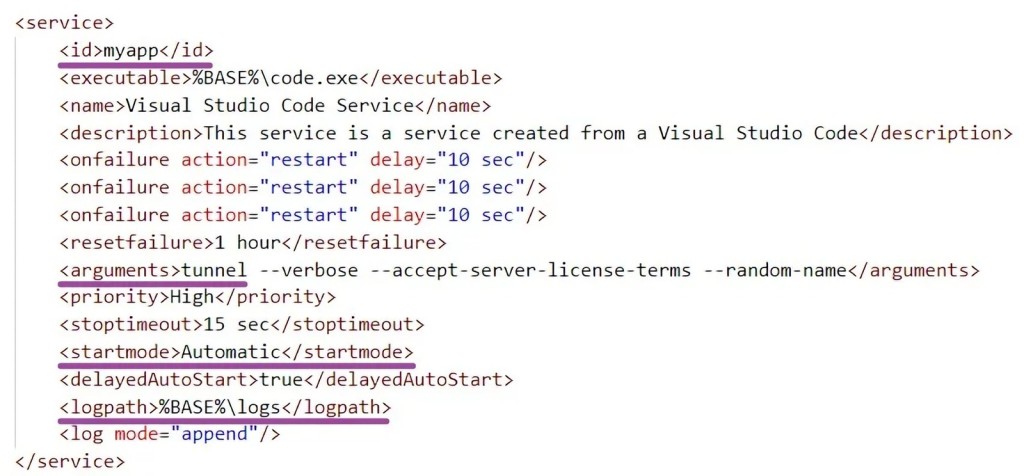
The attackers used a portable, legitimate version of Microsoft Visual Studio Code to gain persistent access to breached devices. The ‘winsw’ tool was used to set it up as a persistent Windows service. A web interface was used to access the devices and authenticate with a GitHub or Microsoft account.
This three-week operation primarily targeted Southern Europe's business-to-business (B2B) IT service providers. In other words, the hackers targeted organizations that provide data, infrastructure, and cybersecurity solutions to different industries.
Sentinel Labs notes that evidence points to Chinese ATP groups such as STORM-o866 or Sandman. However, as of right now, it’s impossible to say who was behind this operation. Analyzing timestamps all points to a potentially China-sanctioned operation, as the operators were primarily active during typical work hours in China, between 9 am and 9 pm CST.
Using Visual Studio Code tunnels is still a relatively new technique hackers use. Regarding Chinese APT groups using this technique, Unit 42 reported in September 2024 the use of VSCode by ‘Stately Taurus’ in espionage operations that targeted organizations in Southeast Asia. However, Sentinel Labs notes that the two operations are not related.