Ultralytics AI Model Found to Propagate Cryptominer Through Hijacked Code
- A supply chain attack, with potentially very serious consequences, affects multiple versions of the Ultralytics package.
- Malicious code was injected into the PyPI release artifacts, and wasn’t present in the public GitHub repository.
- As of right now, Ultralytics version 8.3.47 is safe to install.
Ultralytics is a software development company best known for its YOLO (You Only Look Once) AI model, which accurately detects objects in video streams in real-time. This tool is open-source, which means that practically anyone can utilize it—and on GitHub, this project has had close to 6,500,000 downloads in the last month alone.
Last Friday, Ultralytics 8.3.41 and 8.3.42 were released to the public. However, those who installed it might now have a cryptominer on their device. Upon installing the Ultralytics versions in question, an XMRig Miner is installed at “/tmp/ultralytics_runner” and connects to “connect.consrensys[.]com:8080.”
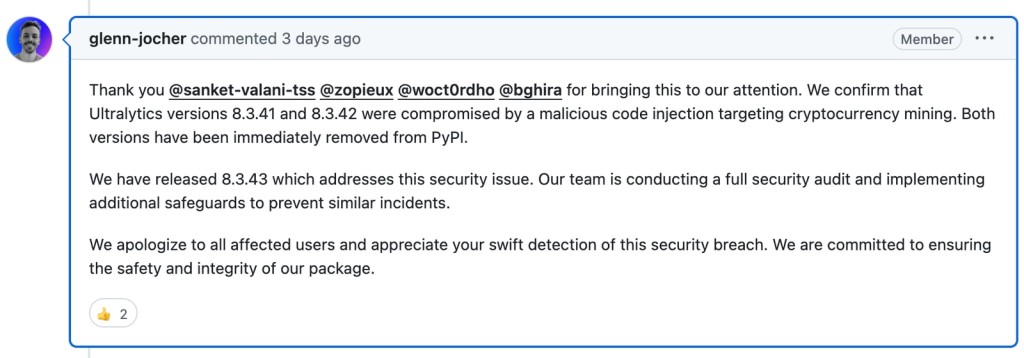
Glenn Jocher, the creator of YOLOv5 and YOLOv8 and the founder of Ultralytics, confirmed on Github that a malicious code injection occurred. He added that the affected versions were removed from PyPI and that a new version (8.3.43) has been released to address this issue.
That said, new reports have surfaced that PyPI still suffers from trojanized releases, which means the cryptominer is still present in package versions 8.3.45 and 8.3.46. In the meantime, version 8.3.47 has been released and is free of the cryptominer in question.
Per the preliminary reports, as uncovered by Jocher, the compromise appears to originate from code injection in the branch names submitted by a user in Hong Kong. That said, it’s unknown if the malicious code performs crypto mining only or perhaps if data logging is involved as well.
To alleviate the issue, you should run a full system scan. Also, check for and terminate any unexpected processes named “ultralytics_runner.” Next, remove any suspicious files in the “/tmp” directory on Unix-based systems. Lastly, update to version 8.3.47 or later—but it's crucial to stay vigilant regarding potentially malicious releases in the future.