Russian “BlueAlpha” APT Group Found to Abuse Cloudflare Tunneling
- BlueAlpha is using Cloudflare to conceal its GammaDrop staging infrastructure.
- The use of Cloudflare Tunneling helps BlueAlpha to implement obfuscation techniques.
- Cyber-sec researchers recommend a series of mitigation strategies.
“BlueAlpha,” which reportedly is a state-sponsored advanced persistent threat (APT) group tied to the Russian Federal Security Service (FSB), is found to rely on Cloudflare to obfuscate its operations. This perilous APT group has been active since at least 2014, and its operations overlap with those of other groups such as Gamaredon, Shuckworm, Hive0051, and UNC530.
As discovered by Insikt Group’s researchers, BlueAlpha currently uses Cloudflare Tunnels to stage GammaDrop malware. Cloudflare Tunnels is a secure tunneling software that allows individuals and companies to connect resources to Cloudflare’s network without using a publicly routable IP address. As such, it protects Web servers from DDoS attacks and other direct cyber-attacks.
However, as this latest instance shows, malicious actors often use Cloudflare Tunnels to conceal their staging infrastructure. BlueAlpha relies on Cloudflare’s tunneling to evade traditional network detection mechanisms in this case.
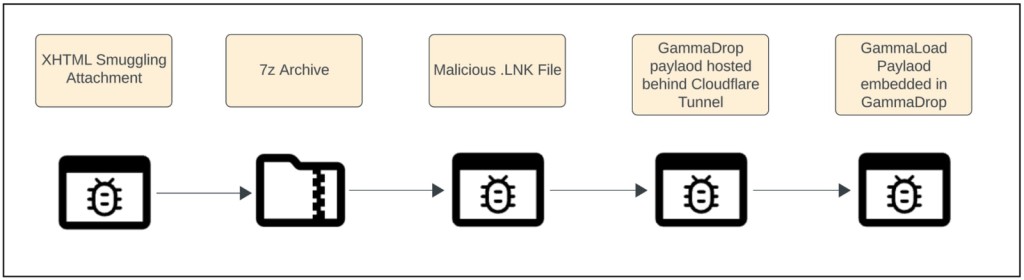
The group propagates malware through HTML smuggling, which allows malware delivery through embedded JavaScript in HTML attachments. Furthermore, DNS fast-fluxing further complicates efforts to disrupt command-and-control (C2) communications, enabling the APT group to communicate with infected devices.
The procedure described above is used to stage BlueAlpha’s often-used GammaDrop malware suite (in use since at least October 2023), which can act as a dropper, writing GammaLoad to disk and ensuring persistence. GammaLoad can then beacon to its C2 server to execute malicious code.
Insikt Grop also recommends a series of mitigation strategies, such as enhancing email security to inspect and block HTML smuggling techniques. Also, it’s crucial to restrict the execution of malicious files through application control policies. Organizations are also advised to monitor network traffic to flag requests to trycloudflare.com.
In the past, Cloudflare was under frequent attacks by copyright owners and various other authorities to step up its efforts in battling against piracy. However, as we see now, this DNS provider is now used by an even wider range of malicious actors.