SmokeLoader Malware Returns, Attacks Manufacturing, Healthcare, and IT Companies in Taiwan
- The SmokeLoader malware was seen again in attacks that targeted Taiwanese companies in various sectors.
- Its integrated plugins enable it to steal sensitive data, including login credentials, cookies, email addresses, and browser information.
- The modular and versatile malware resurfaced due to the widespread availability of cracked versions distributed online.
Entities across Taiwan's manufacturing, healthcare, and information technology sectors have become the focus of a sophisticated malware campaign involving SmokeLoader, according to Fortinet's FortiGuard Labs.
SmokeLoader, first advertised on cybercrime forums in 2011, is a modular malware downloader known for its versatility and advanced evasion techniques. The malware enables data theft, distributed denial-of-service (DDoS) attacks, and cryptocurrency mining, underscoring its adaptability.
While traditionally used to deliver secondary payloads, the latest attacks demonstrate it executes its own suite of malicious activities by using plugins retrieved from its command-and-control (C2) server.
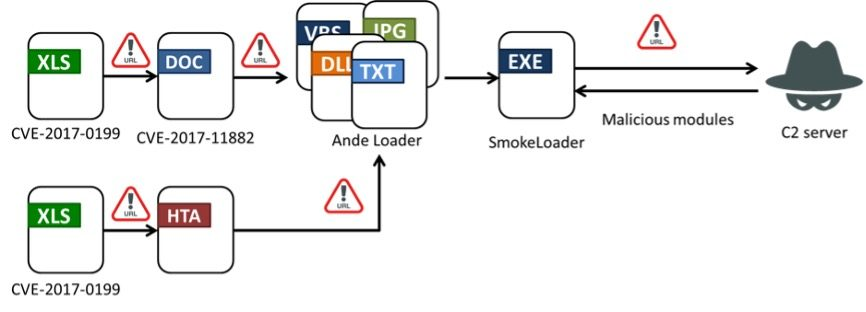
Fortinet’s report highlights the campaign's tactics, which begin with phishing emails containing Microsoft Excel attachments. These attachments exploit long-known vulnerabilities, such as CVE-2017-0199 and CVE-2017-11882, to deploy an intermediary malware, Ande Loader. Once installed, Ande Loader facilitates the deployment of SmokeLoader on compromised systems.
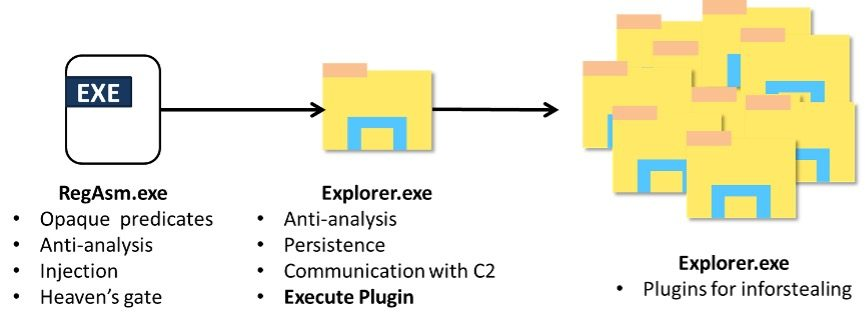
SmokeLoader operates through two distinct components—a stager and a main module. The stager decrypts, decompresses, and injects the main module into an explorer.exe process. This main module is tasked with establishing persistence, communicating with the C2 servers, and executing commands.
Plugins integrated into the malware enable it to steal sensitive data, including login credentials, cookies, email addresses, and browser information, from popular software such as Outlook, FileZilla, Thunderbird, and WinSCP.
SmokeLoader is engineered with numerous evasion techniques that hinder detection and analysis, being able to detect analysis environments, obfuscate its code, and generate fake network traffic to send investigators down false paths.
Instead of downloading a completed file for the final stage, SmokeLoader uses its plugins. These techniques, coupled with frequent updates and enhancements, make SmokeLoader particularly challenging to combat.
The malware saw a significant decline following Operation Endgame in May 2024, a Europol-led effort that dismantled infrastructure linked to multiple malware families, including SmokeLoader, Bumblebee, TrickBot, and IcedID. Over 1,000 C2 domains associated with SmokeLoader were taken offline, and more than 50,000 infections were neutralized.
However, SmokeLoader has resurfaced due to the widespread availability of cracked versions distributed online, highlighting a sustained threat to global businesses. This accessibility continues to empower adversaries leveraging new C2 infrastructures for their operations.
Entities in Taiwan are often targeted by cyberattacks. A Taiwanese government-affiliated research institute was reportedly targeted by the APT41 cybercriminal group to deliver malware like ShadowPad, Cobalt Strike, and other customized tools.