Horns&Hooves Campaign: Fake Email Delivers NetSupport & BurnsRAT to Deploy Rhadamanthys and Meduza InfoStealers
- A newly identified campaign spreads sophisticated RATs, ultimately deploying stealer malware such as Rhadamanthys and Meduza.
- Security researchers uncovered hackers send ZIP archive email attachments that contain JScript scripts pretending to be business documents.
- The hackers target private users, retailers, and service businesses, most of them from Russia.
A newly identified malware campaign has emerged as a significant threat, targeting private users, retailers, and service businesses, predominantly in Russia. Dubbed Horns&Hooves by Kaspersky, the campaign employs highly deceptive phishing techniques to deliver the malicious payload.
The campaign has already compromised over 1,000 victims since its inception in March 2023, spreading sophisticated remote access trojans (RATs) such as NetSupport RAT and BurnsRAT, with the ultimate aim of deploying stealer malware such as Rhadamanthys and Meduza.
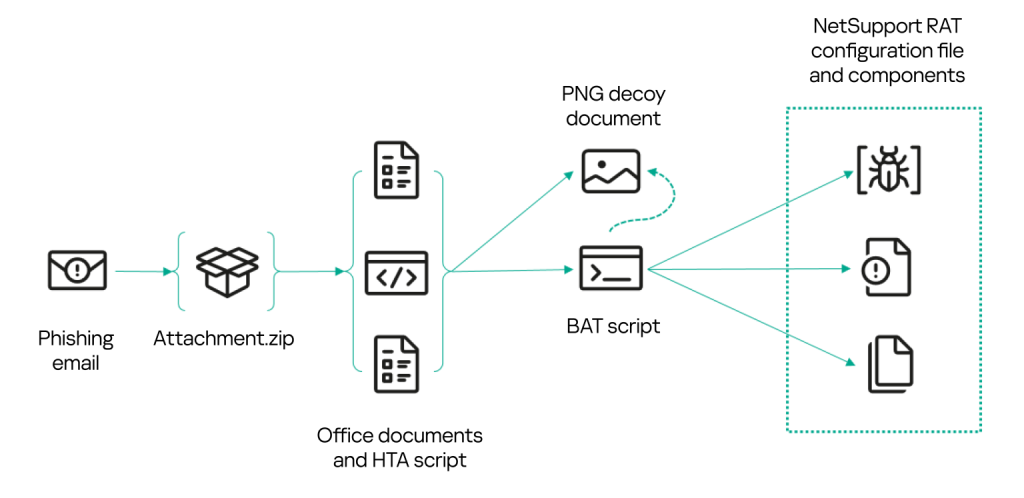
The email campaign delivers lookalike email attachments in the form of a ZIP archive containing JScript scripts, according to the Kaspersky analysis report, skillfully disguised as business-related documents, such as requests and bids, significantly increasing their chances of being opened by unsuspecting recipients.
Additionally, some ZIP archives include organization-related documents mimicking legitimate sources to further bolster the phishing emails' credibility. These tactics indicate a systematic approach by the threat actors, focusing on enhancing the success rate of these attacks.
The downloaded script proceeds to execute multiple tasks, culminating in installing the NetSupport RAT malware that connects to a command-and-control (C2) server managed by the attackers.
By May 2023, the intermediate JavaScript files began impersonating legitimate JavaScript libraries like Next.js to activate the NetSupport RAT infection chain. A separate variant deployed around the same time dropped an NSIS installer responsible for running BurnsRAT.
BurnsRAT, once deployed, offers the attackers extensive control over compromised systems. "Although the backdoor supports commands for remotely downloading and running files, the main task of this component is to start the Remote Manipulator System (RMS) as a service and send the RMS session ID to the attackers' server," explained Ushkov.
RMS enables remote interaction with victim systems, file transfers, and command executions across geographical locations.
The Horns&Hooves campaign may be the work of TA569, a threat actor also known as Gold Prelude, Mustard Tempest, and Purple Vallhund. TA569 is associated with the FakeUpdates (SocGholish) malware and has previously acted as an initial access broker for ransomware groups responsible for deploying malware, such as WastedLocker.
Kaspersky pinpointed overlaps in the NetSupport RAT license and configuration files used by TA569, strengthening the connection. Recent iterations included redesigned BAT scripts for installing NetSupport RAT and updates to embed the malware within the JavaScript code itself, reducing the dependency on external downloads and complicating detection.