Snowflake Extortions Hacker May Be an American Soldier, Security Experts Say
- As the investigation regarding the Snowflake cyberattacks continues, a new person of interest takes the stage.
- A recently arrested hacker reportedly collaborated with Kiberphant0m, who sold exfiltrated data when ransoms were not paid.
- Kiberphant0m might be a U.S. Army soldier recently stationed in South Korea.
Security investigators are scrambling to piece together the identity of a notorious hacker known as “Kiberphant0m,” believed to be behind significant data theft and extortion schemes targeting cloud storage platform Snowflake customers.
Recent evidence strongly suggests that Kiberphant0m might be a U.S. Army soldier who is or was recently stationed in South Korea, according to security expert Brian Krebs.
The attacks first surfaced when hackers accessed sensitive customer data stored on Snowflake accounts that lacked adequate protection, such as multi-factor authentication. By exploiting these vulnerabilities, the cybercriminals raided data repositories from industry giants, including AT&T, which reported major breaches earlier this year.
AT&T confirmed that hackers accessed and stole sensitive customer data, including details linked to approximately 110 million individuals. Reports suggested that AT&T paid $370,000 for the deletion of stolen records.
Authorities have already arrested two suspects connected to these breaches. Canadian authorities apprehended Alexander Moucka (alias Judische/Waifu), indicted on 20 criminal counts in the U.S., while another suspect, John Erin Binns, is currently detained in Turkey.
Investigators revealed that Moucka collaborated with Kiberphant0m, who was tasked with selling stolen data when victims refused to pay ransoms. Despite these arrests, Kiberphant0m’s activities continue unabated.
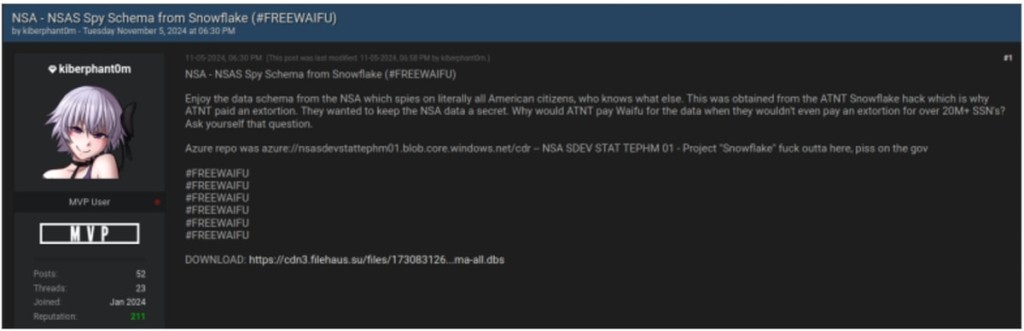
Following Moucka's detention, Kiberphant0m posted further data and dire threats on hacker forums, including details of what they claimed were U.S. high-profile call logs and NSA data schemas.
Kiberphant0m continues to pose a significant threat, doubling down on extortion efforts. They recently posted fraudulent sale offers, including sensitive Verizon call logs tied to government agencies and emergency responders. More concerning, they offered a SIM-swapping service, enabling the takeover of phone numbers for malicious purposes.
Authorities are intensifying their efforts to identify and apprehend Kiberphant0m, using patterns from their multiple cybercrime personas and communications across forums like Telegram and Discord.
If proven, the connection to an active-duty member of the U.S. military adds another layer of severity to the case. It raises critical questions about internal vetting and the ramifications of cybercrime links within governmental institutions.
A member of the infamous ShinyHunters hacking group revealed how they reportedly stole customer data from Snowflake accounts via a breached EPAM employee account.