A New Malware Campaign Delivers Ursnif Via a Word Document
- Ursnif malware strikes again, and this time it is distributed through a malicious MS Word document.
- Cisco Talos is warning that the malware is operating quite effectively and efficiently, running a series of optimized commands.
- Macro malware is especially dangerous if the users have enabled macros on their Office Suite.
Cisco Talos is warning about a new campaign aiming to propagate the well-known Ursnif banking malware. Cisco’s security researchers tracked this activity through their AMP (Advanced Malware Protection) Exploit Prevention Engine and took proactive action to block Ursnif from successfully infecting its targets. Ursnif attempts to distill the banking login credentials of its victims and is generally a popular choice for attacks of this kind, along with the IceID. The previous campaign for its distribution occurred in April, and the means was email, while this time the wagon is a Microsoft Office document.
According to the Talos report, the infected document contains a malicious VBA macro, which is a set of commands and instructions grouped as one. If the user has already enabled the macro function on their Office suite, then the commands run upon the opening of the document file, otherwise, the user is prompted to enable macros through a relevant message. The running of the macro results in the execution of PowerShell code that is base64 encoded and basically just downloads and runs Ursnif on the victim’s system.
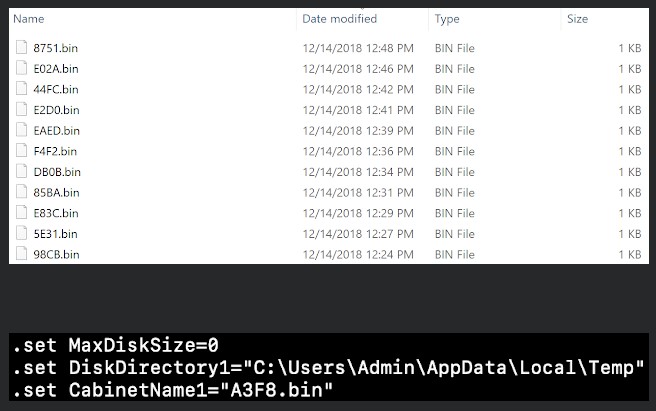
The malware then proceeds to conduct a series of actions such as the creation of a necessary registry entry, leading to the execution of an encoded PowerShell command which subsequently leads to the decoding of an even more complex PowerShell command that constitutes of a decoder, a DLL creation array, and an executor. Ursnif draws API functions from kernel32 and completes an APC (Asynchronous Procedure Calls) injection through the method of queuing it as an alertable thread. Having established the infection, the malware initiates the C2 communication over HTTPS, something that most antivirus solutions will miss, as the Talos team warns. Before the exfiltration of the collected data, Ursnif is compressing them as “CAB” files, making them easier to transfer around, as well as better protected from detection.
image source: blog.talosintelligence.com
The full list of the indicators of compromise is to be found in the Cisco Talos post, but no matter the Ursnif menace, users are generally advised to be especially cautious when receiving documents that they didn’t expect. Finally, never leave macros enabled by default on your Microsoft Office Suite, as this will take away a precious infection prevention step and opportunity from you. Microsoft has even published a relevant set of instructions on how to protect yourself from macro malware.
Have you ever fallen victim of a macro malware attack? Let us know of your experience in the comments section below, and don’t forget to share this story with others through our socials on Facebook and Twitter.