Fortinet Flaw Allows to Compromise VPN Credentials via DEEPDATA Malware Exploit
- DEEPDATA malware abuses a critical FortiClient for Windows vulnerability to exfiltrate VPN credentials from compromised environments.
- Security experts observed a cyber espionage group leveraging this zero-day vulnerability.
- Associated with other tools, the malware could conduct extensive surveillance across communication services like WhatsApp, Telegram, and Microsoft Outlook.
A significant vulnerability in Fortinet's FortiClient for Windows has been identified, allowing the DEEPDATA malware to exploit the unpatched security flaw to steal VPN credentials. This discovery has underscored a critical risk to enterprise cybersecurity as threat actors leverage advanced tools to compromise sensitive information.
A cyber espionage group dubbed BrazenBamboo is responsible for exploiting this zero-day vulnerability, as revealed by Volexity in a recent report.
The ramifications extend beyond VPN credential theft. DEEPDATA, along with associated tools like DEEPPOST and LightSpy, enables BrazenBamboo to conduct extensive surveillance across multiple communication platforms, including WhatsApp, Telegram, and Microsoft Outlook.
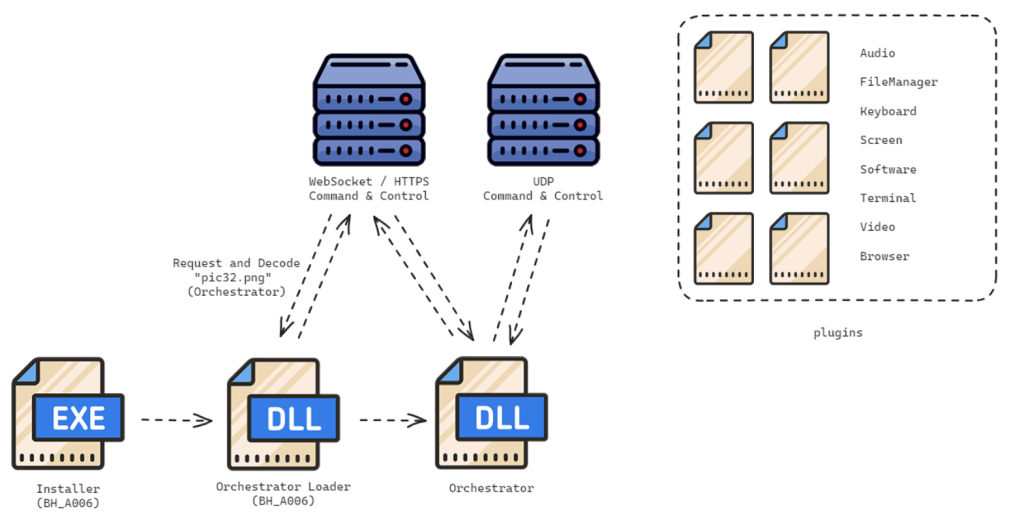
DEEPDATA, part of a broader suite of modular malware frameworks, targets Windows-based systems to extract extensive data, utilizing a DLL loader ("data.dll") to deploy various plugins, including a "FortiClient" DLL engineered to capture VPN credentials from memory.
The LightSpy framework, previously linked to known China-affiliated threat actor APT41, has been adapted for use on macOS, iOS, and now Windows, highlighting the group's cross-platform capabilities.
Volexity reported the Fortinet flaw on July 18, 2024, yet it remains unpatched, leaving systems vulnerable. The ongoing threat posed by DEEPDATA and related malware emphasizes the need for immediate action by organizations utilizing Fortinet products to mitigate potential exploitation.
In other recent news, over 61,000 outdated D-Link network-attached storage devices were confirmed to remain exposed online due to a critical command injection vulnerability, as the company announced its intentions to leave it unaddressed.
This month, CISA identified two critical vulnerabilities in PTZOptics cameras with older firmware that allow OS command injection and authentication bypass, posing a significant risk, as attackers could gain control over IoT devices and steal sensitive information from the compromised networks.