Iranian Hackers Deploy SnailResin Malware via Aerospace Industry Dream Job Lure
- Iranian threat actor TA455, also known as APT35, was seen posting fake aerospace jobs to distribute malware.
- The group used cross-nation technique sharing and advanced phishing strategies to deploy the SlugResin backdoor.
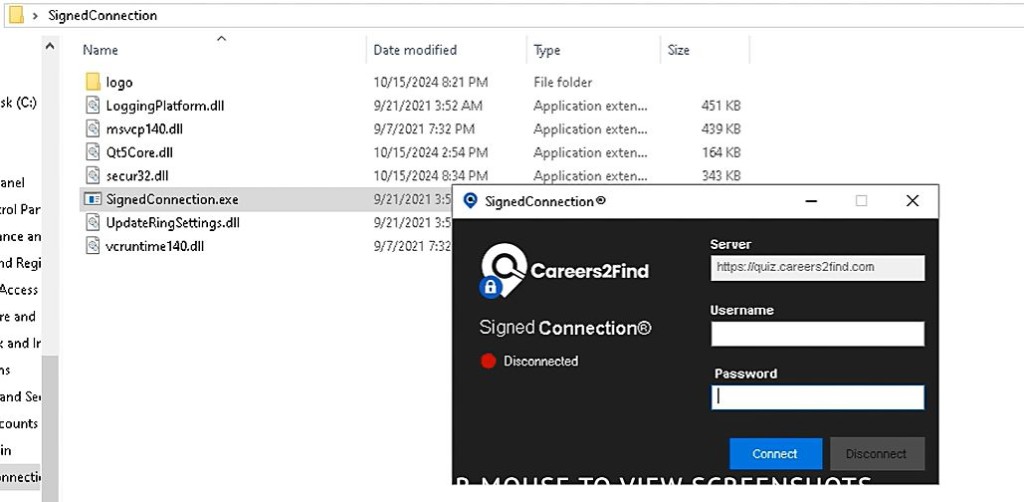
- Victims are directed to a domain impersonating a legitimate job recruitment site, where a downloaded ZIP file triggers a malicious DLL.
A campaign orchestrated by the Iranian threat actor TA455 strategically targets the aerospace sector by employing deceptive "dream job" lures to distribute the SnailResin malware, which subsequently activates the SlugResin backdoor.
ClearSky Cyber Security has uncovered and named the campaign “Iranian Dream Job,” and these findings attribute the malware deployment to a subgroup of the notorious Iranian government cyberwarfare group Charming Kitten APT, also called APT35, Phosphorus or Mint Sandstorm, Ajax Security, and NewsBeef.
The campaign initiates its attack vector through fake recruiting websites and LinkedIn profiles. Unsuspecting victims are directed to download a ZIP file from a domain masquerading as a legitimate job recruitment site. This ZIP file, while appearing harmless, contains an executable file that triggers the malicious DLL file “secur32[.]dll” via DLL side loading.
This campaign's implications are multifaceted. Notably, some cybersecurity firms have identified the malware files as being associated with the North Korean Kimsuky/Lazarus APT group.
This raises the possibility that either Charming Kitten deliberately impersonates Lazarus to obfuscate its activities – or there is a potential collaboration or sharing of tactics and tools between Iran and North Korea.
The campaign has been active since at least September 2023, with prior reports from Mandiant highlighting similar Iranian espionage methods targeting aerospace, aviation, and defense sectors across the Middle East, including Israel and the UAE, as well as Turkey, India, and Albania.
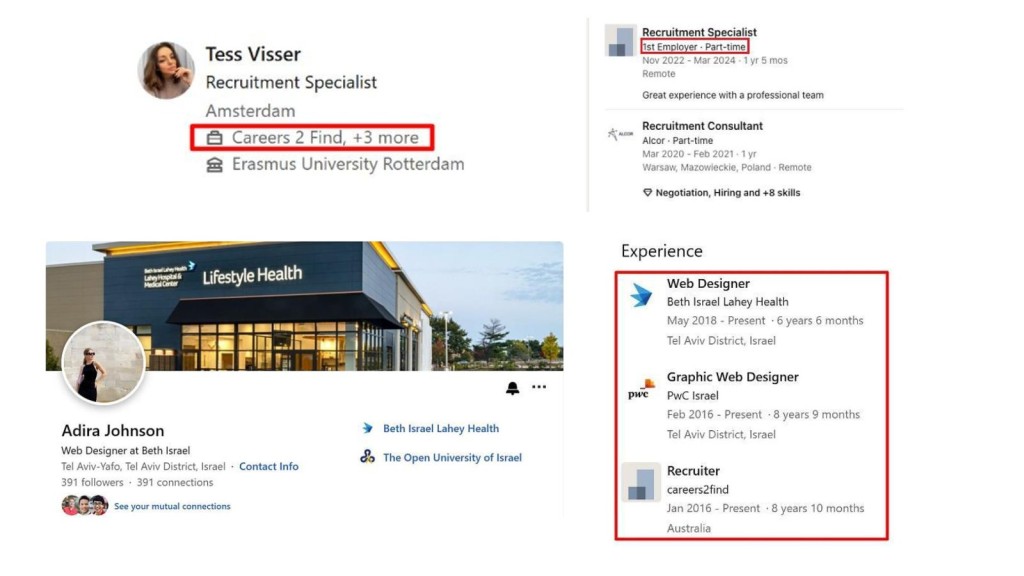
ClearSky's latest findings indicate an evolution of tactics, with newer LinkedIn profiles, such as those linked to a fictitious company, “Careers 2 Find,” succeeding previously identified profiles like “1st Employer.”
During the last few months, North Korean threat actors exploited LinkedIn for malware distribution via fake job offers, sometimes targeting cryptocurrency users on LinkedIn specifically.