Advanced Malicious Framework Winos4.0 Spreads via Gaming-Related Software
- A Winos4.0-spreading campaign targets Microsoft Windows users, distributing the malware via gaming-related lures.
- This versatile tool can conduct reconnaissance on compromised systems and exfiltrate sensitive user data.
- The malware can easily exfiltrate personal user data from the compromised machines.
A sophisticated threat campaign surfaced, leveraging gaming-related applications – including installation tools, speed boosters, and optimization utilities – to distribute Winos4.0, an advanced malicious framework rebuilt from the notorious Gh0strat malware.
This stealthy operation has been specifically noted for its comprehensive functionality and robust architecture, allowing threat actors to control numerous online endpoints effectively, according to a FortiGuard Labs security report.
Winos4.0 constitutes a significant threat due to its modular components, each dedicated to distinct malicious functions. The framework has been deployed across various attack campaigns, such as Silver Fox, marking it as a versatile tool in cybercriminals' arsenals.
The malware has been found hidden within various gaming-related applications, including installation tools, speed boosters, and optimization utilities. Notably, the decoded DLL file, "you.dll," contains indications of targeting the education sector, hinted at by its file description 校园政务 (Campus Administration).
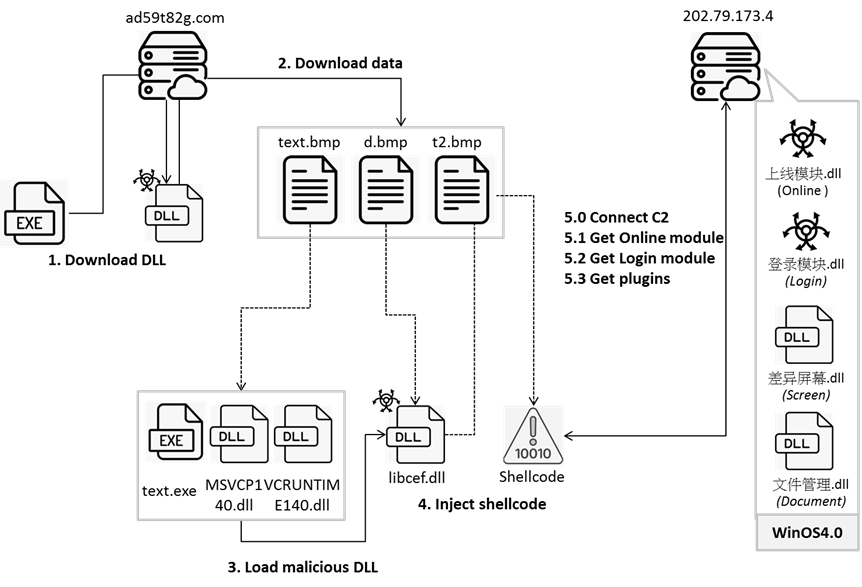
The threat actors achieve initial access by distributing seemingly legitimate game-related applications. Once executed, these applications retrieve a fake BMP file from a remote server, which is then XOR decoded to extract the malicious DLL that sets up the execution environment.
The malware establishes persistence by creating scheduled tasks or adding executables to the registry, depending on the system's security posture. The primary malicious DLL file injects shellcode to execute actions within compromised environments. This file, labeled as "学籍系统" (Student Registration System), further suggests a focus on educational institutions.
Upon establishing persistence, Winos4.0 communicates with a Command and Control (C2) server to download additional modules and execute commands. These modules enable functionalities such as system information collection, environment checks, and core backdoor functionality.
The module also examines whether system monitoring-related software or anti-virus service is present, checks for a crypto wallet extension, and then gathers and stores related information. It also collects system data like host information, including the IP address, computer name, operating system, CPU, disk, network card, directory name, and time.
Two plugins from the C2 server are specifically designed to capture screenshots and manage documents, facilitating the exfiltration of user documents and the gathering of sensitive information while discreetly monitoring activities on compromised machines.
In October, security researchers discovered that users seeking game cheats were targeted by attackers luring gamers to download a Lua-based malware by masquerading it as legitimate cheating script engines. These attacks are getting frequent, so users should only download the software from verified sources.