A Critical Vulnerability in AWS Cloud Development Kit Risked Potential Account Takeover
- An Amazon Web Services Cloud Development Kit vulnerability could have led to full account takeover.
- In specific conditions, a potential attacker may have gained admin access to a target's AWS account.
- Security researchers said S3 buckets and IAM roles use predictable naming patterns that could result in S3 Bucket Namesquatting.
A significant Amazon Web Services (AWS) Cloud Development Kit (CDK) flaw could have resulted in full account takeovers under certain conditions, allowing an attacker to potentially gain administrative access to a target's AWS account.
The issue stems from predefined naming conventions for AWS S3 buckets, which could be exploited to orchestrate Bucket Monopoly attacks, leading to unauthorized access to sensitive data, Aqua researchers Ofek Itach and Yakir Kadkoda said in a recent report.
The flaw was responsibly disclosed on June 27, 2024, and subsequently addressed by AWS with the release of CDK version 2.149.0 in July.
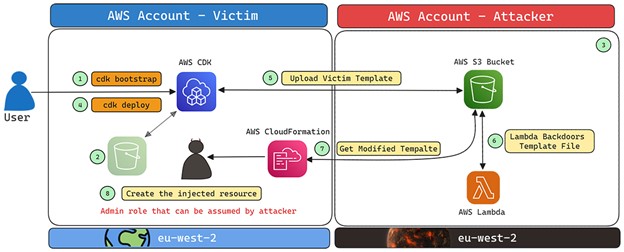
The bootstrapping process in the AWS CDK, which provisions necessary resources like S3 buckets and IAM roles, uses predictable naming patterns. This predictability in naming allows attackers to engage in S3 Bucket Namesquatting, claiming buckets with names based on default qualifiers used by many AWS customers.
In a hypothetical attack scenario, an adversary could create a bucket with a predictable name, allowing it to be used by the victim's CDK deployments. If the victim's CDK has permissions to read/write from this bucket, it could enable the attacker to execute malicious actions by tampering with CloudFormation templates.
Addressing this vulnerability, AWS has enhanced security measures to ensure assets are only uploaded to buckets within the user's account. They have also urged customers to customize their qualifiers during the bootstrapping process to reduce predictability and enhance security.
Users who utilized CDK version v2.148.1 or earlier are advised to update to the latest version and re-run the bootstrap command. Alternatively, they can apply an IAM policy condition to enhance security further.
This disclosure highlights the importance of keeping AWS account IDs confidential, using scoped IAM policies, and avoiding predictable naming conventions for S3 buckets. Security experts recommend generating unique hashes or random identifiers for regions and accounts to protect against potential threats.
In June, AWS announced launching support for FIDO2 passkeys as a method for multi-factor authentication (MFA) – a highly safe and user-friendly option that balances usability and strong security.