New Grandoreiro Banking Malware Variants Add Advanced Tactics to Evade Detection
- The Grandoreiro banking malware returned with improved tactics for avoiding detection, including a new sandbox evasion code.
- It also added a domain generation algorithm and digitally signed legitimate certificates.
- Besides, it employs gathering host information, identifying anti-malware software, and detecting specific user behaviors before execution.
New variants of the notorious banking malware Grandoreiro have been discovered employing sophisticated tactics to elude anti-virus measures. The malware has expanded its reach beyond Latin America and Europe, targeting 1,700 financial institutions across 45 countries.
Kaspersky's recent analysis highlights the persistence and progression of Grandoreiro, which has been active since 2016.
Among the newly observed tactics, Grandoreiro now utilizes a domain generation algorithm (DGA) for command-and-control (C2) communications and incorporates ciphertext stealing (CTS) encryption along with mouse tracking to focus on avoiding detection while increasing its effectiveness.
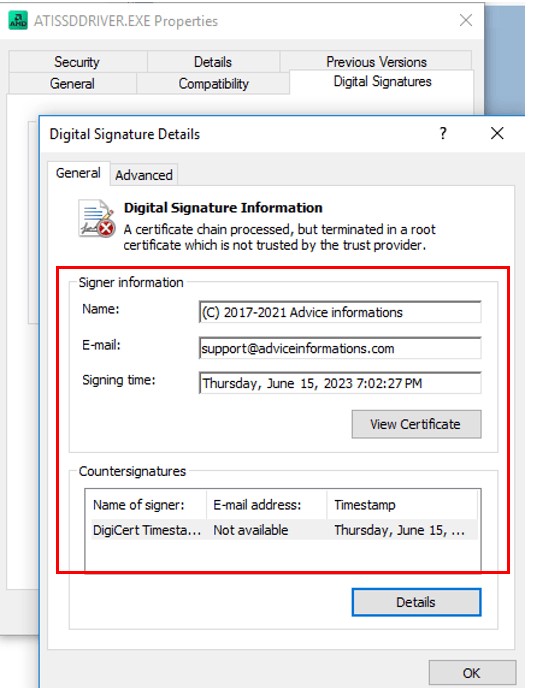
Additionally, 2024 campaigns have been identified using notably large portable executables, disguising them as AMD External Data SSD drivers to bypass sandbox environments to avoid the radar of conventional security systems. The new sandbox evasion code has been implemented in the downloader.
The malware is primarily distributed through phishing emails, with a secondary distribution channel via malicious advertisements on Google, which the search engine fails to remove. Notably, Grandoreiro's operations now include "lighter, local versions" specifically aimed at banking customers in Mexico, reflecting a strategic targeting approach.
Most Grandoreiro attacks use a DLL sideloading technique that employs digitally signed legitimate binaries to run the malware.
Grandoreiro's advanced capabilities include gathering host information, identifying anti-malware software, and detecting specific user behaviors to halt execution, highlighting its adaptive threat model. Furthermore, the malware acts as a clipper, rerouting cryptocurrency transactions to wallets controlled by the attackers.
One of the most notable updates is the introduction of a CAPTCHA barrier before executing the main payload, designed to circumvent automated security analysis.
Additionally, the latest version of Grandoreiro supports self-updates, keystroke logging, Outlook email monitoring for specific keywords, and attempts to mimic legitimate user behavior to deceive anti-fraud systems.
Despite recent law enforcement efforts that led to the arrest of some group members, the cybercriminal gang behind Grandoreiro continues to evolve and adapt.