Exploited Roundcube Webmail Flaw Poses Threat to CIS Government Emails
- An exploit of a vulnerability in the Roundcube Webmail client targets CIS government organizations.
- Hackers leveraged a medium-severity stored XSS flaw that allows remote code execution to steal credentials.
- Threat actors used specifically crafted emails that appear empty but contain a document attachment.
Hackers have been actively exploiting a vulnerability in the Roundcube Webmail client, targeting government organizations across the Commonwealth of Independent States (CIS). The exploitation leverages a medium-severity stored XSS (cross-site scripting) vulnerability that has been active since June.
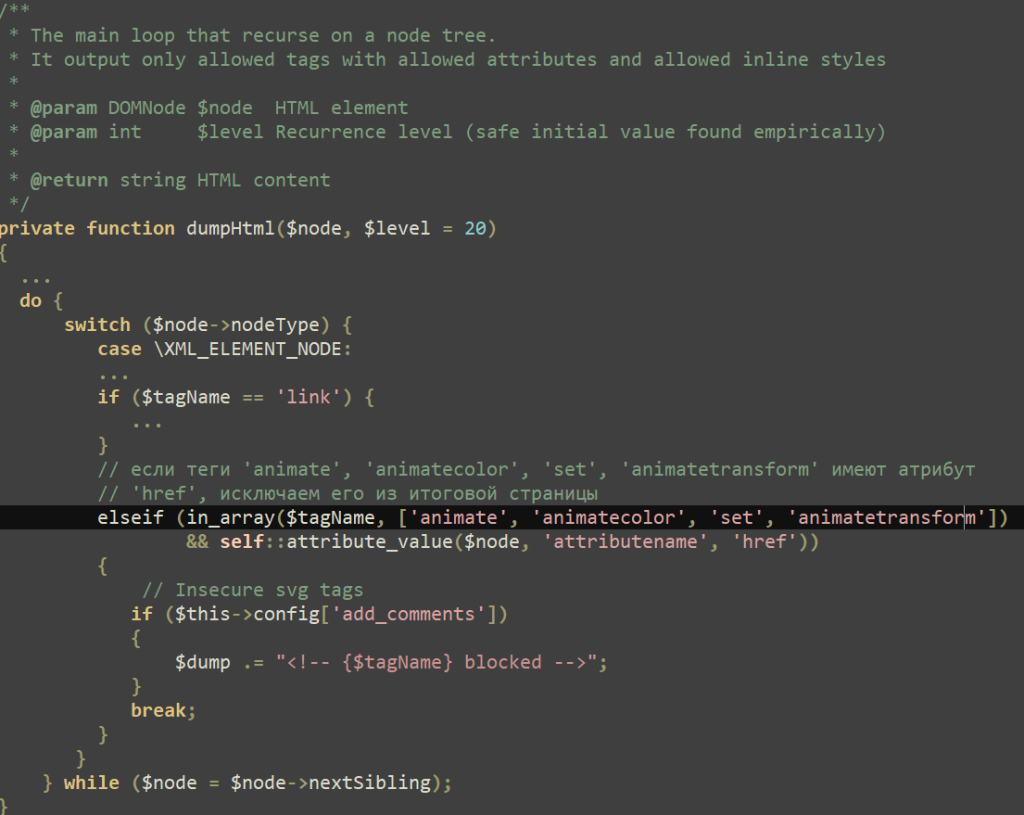
Discovered by cybersecurity firm Positive Technologies in September, this vulnerability, identified as CVE-2024-37383, allows threat actors to execute malicious JavaScript code when unsuspecting users open specifically crafted emails.
Roundcube Webmail, a popular open-source solution among commercial and governmental entities, has been under attack due to improper processing of SVG elements in emails. This flaw circumvents syntax checks, enabling malicious code to run on user pages.
The attacks involve emails that appear empty but contain a .DOC attachment. Crucially, hidden within the code is a base64-encoded JavaScript payload disguised as an "href" value.
This payload not only prompts the download of a decoy document but also injects an unauthorized login form to steal users' credentials, which are then transmitted to a remote server hosted on Cloudflare infrastructure.
To exacerbate the situation, attackers have been using the ManageSieve plugin to exfiltrate messages, further compromising affected systems. Vulnerable Roundcube versions include those earlier than 1.5.6 and versions 1.6 to 1.6.6. System administrators are advised to update to versions 1.5.7, 1.6.7, or the latest 1.6.9 as a precautionary measure.
This isn't the first time Roundcube has been targeted. Earlier in the year, CISA alerted organizations about CVE-2023-43770, another XSS vulnerability in Roundcube.
Additionally, in October 2023, a zero-day XSS flaw tracked as CVE-2023-5631 was exploited by Russian hackers known as 'Winter Vivern' against European government entities and think tanks.
In August, the Russian government and IT organizations were targeted by a new spear-phishing campaign that security researchers call EastWind. The campaign delivered an updated version of CloudSorcerer, novel PlugY backdoors, and the GrewApacha trojan.