Nvidia Container Vulnerability Allowing Complete Host Takeover Affects 35% of Cloud Environments
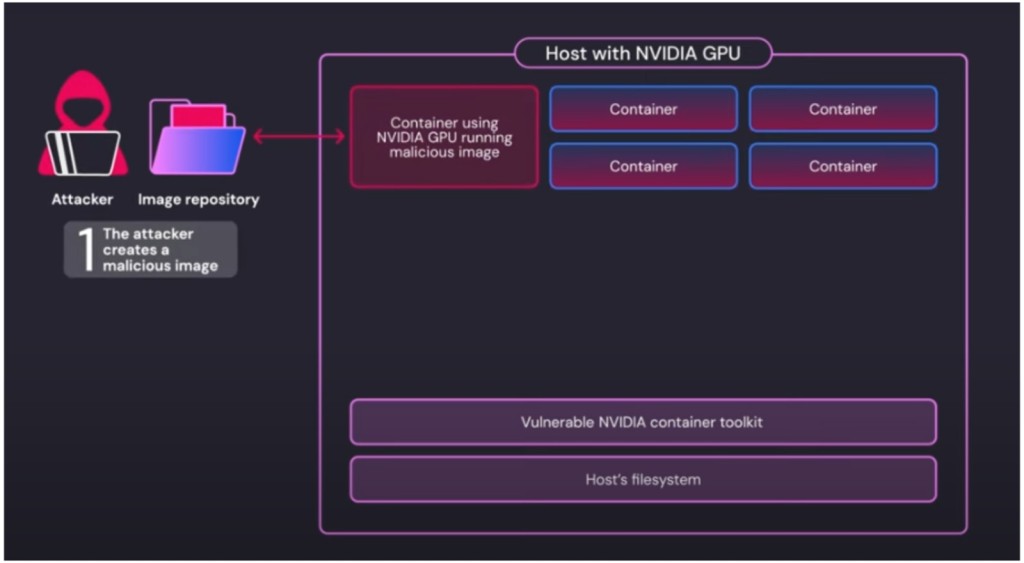
- A new Nvidia Container Toolkit critical flaw allows potential attackers who control a specially crafted image to escape containers.
- The image can end up being executed via supply chain or social engineering attacks or direct access to shared GPU resources.
- Running the malicious image on a system leads to a complete host takeover.
A newly identified critical vulnerability in Nvidia's Container Toolkit, designated as CVE-2024-0132, is a “Time of Check Time of Use” (TOCTOU) flaw that allows malicious actors to escape containers and gain full control of the host system. Security researchers at Wiz disclosed the bug to Nvidia on September 1, and a patch was released on Wednesday.
Once the exploit is successful, attackers may execute arbitrary code, cause denial of service, escalate privileges, disclose sensitive information, or tamper with data. The threat is particularly acute in environments that handle third-party container images or AI models, increasing the risk of executing a malicious image.
The TOCTOU CVE-2024-0132 flaw enables an attacker who controls a specially crafted container image to gain full access to the underlying host system once the image is executed via the vulnerable toolkit and escapes from that container.
The hacker can get the image to run on the target platform by a supply chain or social engineering attack or by having direct access to shared GPU resources. The attacker can then reach the Container Runtime Unix sockets and execute arbitrary commands with root privileges, leading to a complete host takeover.
The flaw affects all versions of the Container Toolkit up to v1.16.1 and Nvidia GPU Operator up to v24.6.1 and earned a severity rating of 9.0 out of 10 on the Common Vulnerability Scoring System (CVSS).
The updated versions, Container Toolkit v1.16.2 and Nvidia GPU Operator v24.6.2 address the vulnerability. Notably, this flaw does not impact setups utilizing the Container Device Interface (CDI).
According to Wiz, approximately 33 percent of cloud environments globally run a vulnerable version of Nvidia's Container Toolkit. This widespread use, particularly in Kubernetes-powered infrastructures, heightens the risk of unauthorized access to confidential data and system control. AI service providers allowing customer-deployed GPU-enabled container images are especially vulnerable.