HZ Rat Backdoor for macOS Targets Chinese DingTalk and WeChat Users
- A macOS version of the HZ Rat backdoor is targeting people in China, trying to harvest enterprise and personal data.
- Among other information, the malware collects Google Password Manager credentials and DingTalk and WeChat sensitive user data.
- Security researchers say it may have been deployed via fake OpenVPN app installation packages.
An Apple macOS version of the HZ Rat backdoor targets users of two instant messaging apps in China, the latest Kaspersky security report said. The attackers focus on stealing data from enterprise messenger DingTalk and the social and messaging platform WeChat users, possibly bundling the info-stealing malware with a legitimate OpenVPN installer.
First documented in November 2022, the malware has been distributed via self-extracting ZIP archives or malicious RTF documents.
The macOS backdoor samples are similar to the Windows version but with a different payload. Some versions of the backdoor use local IP addresses to connect to the command and control (C2) server, which could indicate a targeted attack and the intention to employ the backdoor for lateral movement.
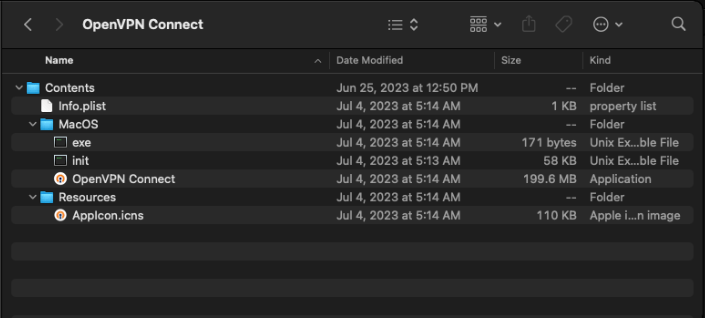
The new version’s dissemination method it yet unknown, but one sample contained an installation package indicating a connection to a fake OpenVPN app.
The installer masquerades as a wrapper for the legitimate OpenVPN Connect client, adding two files to it – an executable and the backdoor.
Hackers focus on collecting data about the victim and their machine, such as the list of applications, Google Password Manager credentials, System Integrity Protection (SIP) status, and System and device details.
However, the malware also targets WeChat and DingTalk user information, such as WeChat ID, email, and phone number, as well as DingTalk organization name, department, username, corporate email address, and phone number.
HZ Rat can execute PowerShell commands and scripts, write arbitrary files to the disk, upload files to the server, and exfiltrate data.
One C2 server is located in the U.S., one in the Netherlands, and the rest are based in China. The fake OpenVPNConnect ZIP archive containing the macOS installation package reportedly was previously downloaded from a Chinese video game developer miHoYo domain, known for Genshin Impact and Honkai.
In recent news, a new RAT named BingoMod by security researchers was seen infecting Android devices to initiate fraudulent money transfers. The malware has account takeover capabilities and is distributed via smishing.