New NGate NFC Data-Stealing Android Malware Clones Contactless Payment Cards
- A recent crimeware campaign added a new Android malware feature that intercepts NFC data to steal funds.
- Hackers can steal this data from smartphone wallet apps and withdraw cash or transfer funds to their accounts.
- Victims are persuaded to install malicious software via websites or apps impersonating legitimate banks.
A new Android malware can steal near field communication (NFC) data from victims’ payment cards via mobile smartphones’ wallets as part of a novel crimeware campaign that targeted clients of three Czech banks. The data is then relayed to the device of a criminal that can withdraw cash, the latest report from ESET Research says.
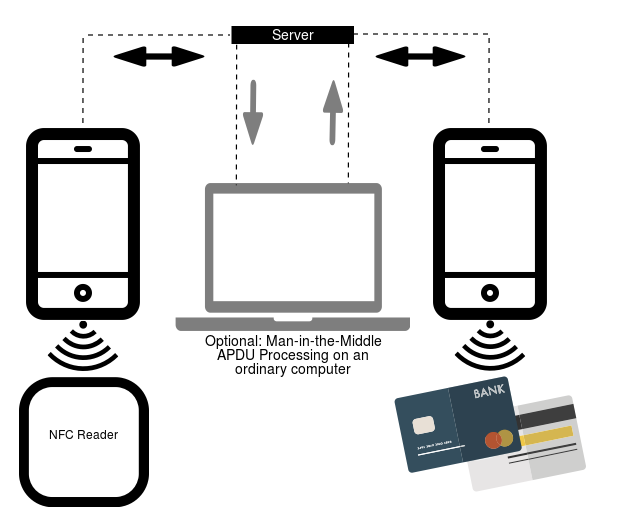
According to the security report, the group has operated in Czechia since November 2023. Security researchers track this malware as NGate since the technique is based on NFCGate, a tool designed by students at the Technical University of Darmstadt, Germany, to capture, analyze, or alter NFC traffic.
NGate was first seen in March 2024, when Android malware was added to the mix of standard malicious techniques like social engineering and phishing.
NGate allows attackers to clone NFC data from victims’ physical payment cards and relay this data to an attacker-controlled device that can emulate the original card and withdraw money from an ATM. If cash withdrawal fails, funds from the victims’ accounts could also be transferred to other bank accounts.
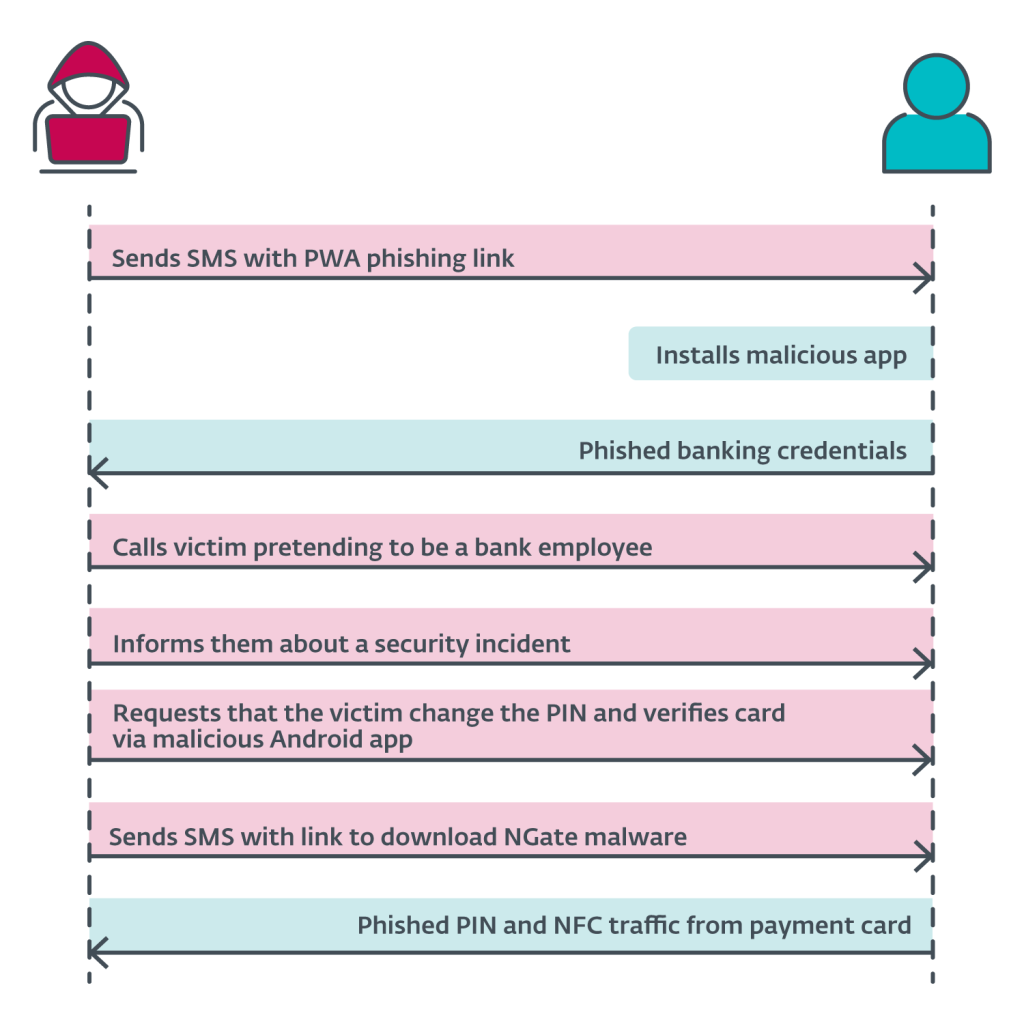
Victims compromised their own Android devices, downloading and installing the malware via communications impersonating legitimate bank domains or apps available on the Google Play store. What’s more, users did not have to root their devices.
Once opened, NGate displays a phishing website that collects and sends users’ banking information to the attacker’s server.
The NFCGate tool, which is available on GitHub, sends an NFC signal through a server from one Android device to another that can mimic or emulate it. The tool can capture NFC traffic from NFC apps and send this NFC data to another device, where it mimics or replays data it has previously intercepted.
ESET researchers identified six different NGate apps specifically targeting clients of three banks in Czechia between November 2023 and March 2024. The report adds that the Czech police apprehended a 22-year-old who had been stealing money from ATMs in Prague.
The activity is part of a broader campaign distributed via automated voice calls, SMS messages, and social media malvertising on Facebook and Instagram, which leverages Progressive Web Applications (PWAs) and WebAPKs to steal mobile users' financial credentials. The hackers target Czechia, Hungary, and Georgia users with phishing apps impersonating legitimate banks.
In other attack scenarios, threat actors with physical access to the payment card could clone NFC tags or copy and emulate the cards via a rooted and customized Android device. However, as of April 2024, Google requires users to provide verification for every NFC payment, even for unlocked devices.