Novel Card Skimmer Campaign Targets Customers of Magento-Based Online Shops
- Hackers implant code in compromised online stores using the e-commerce platform Magento.
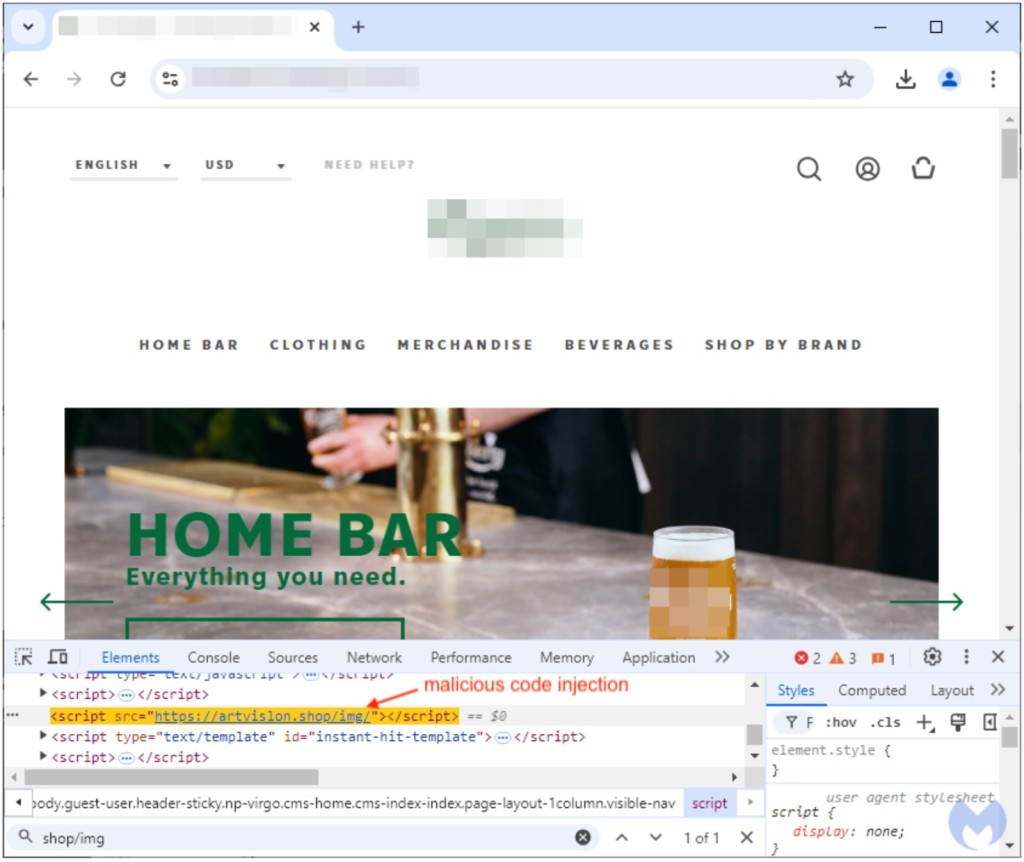
- The seemingly harmless script tag loads JavaScript content from a remote website.
- Once on the checkout page, the shoppers’ payment card details are stolen as they type in.
A few hundred online stores based on the e-commerce platform Magento have been injected with digital skimmers in a new malware campaign that exfiltrates credit card numbers, expiration dates, and CVV/CVC in real-time, as the user types these details, the latest Malwarebytes report says.
A seemingly harmless line of code was injected by the attackers. The script tag loading content from a remote website had the same naming pattern across the compromised e-shops and loaded JavaScript.
The security researchers identified over a dozen attacker-controlled websites created to receive the stolen data and 1,121 unique card information theft attempts from Malwarebytes users who happened to shop at one of the compromised stores.
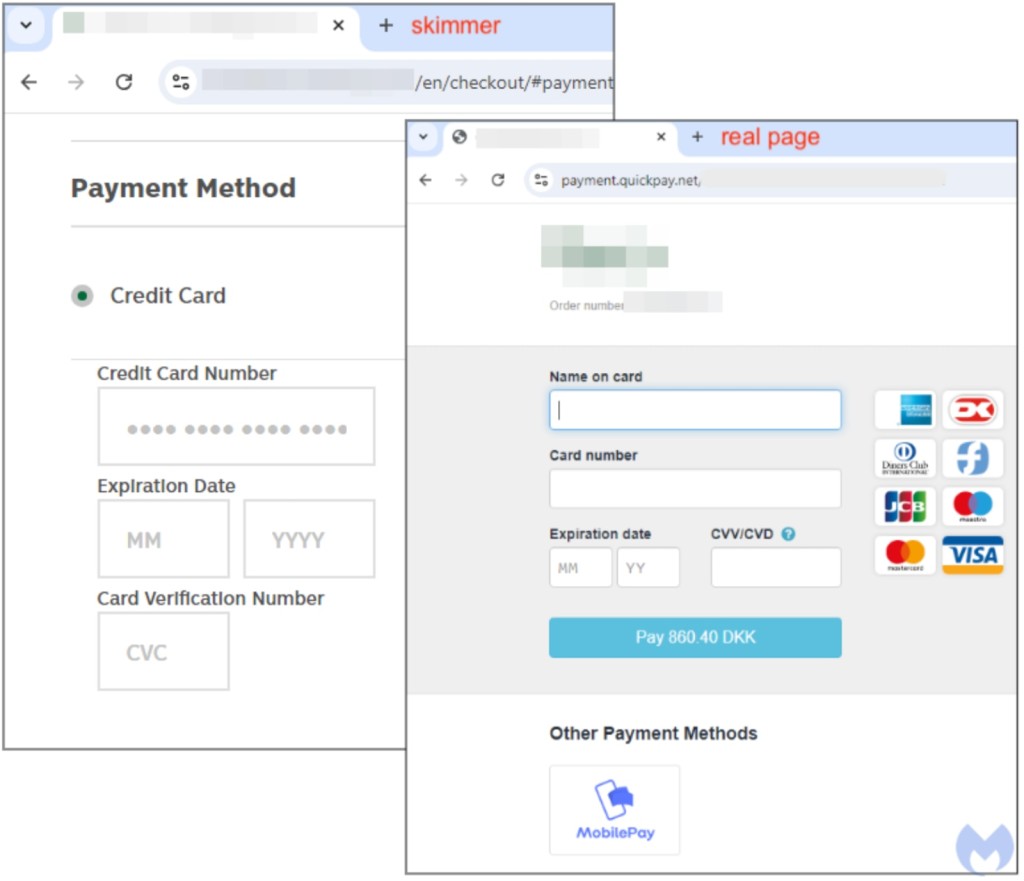
Card skimmers activate on the checkout page, and in this case, it sometimes seamlessly altered the payment flow by introducing a fake “Payment Method” frame and sometimes intervened before the external payment company page for websites that used such services.
The malware transmits and stores credit card numbers, expiration dates, and CVCs in real-time.
Security experts believe the threat actors likely used the same vulnerability to plant their malicious code due to the compromises looking similar. Impacted online stores have been notified and taken action, and Cloudflare has already flagged malicious infrastructure as phishing.
In June, a new variation of the “gtag” credit card skimming attacks called Caesar Cipher Skimmer was deployed to several different CMS platforms, infecting WordPress, Magento, and OpenCart, affecting almost 80 sites. In August, a threat actor was seen exploiting a PrestaShop “gtag” Web socket connection to exfiltrate an online store’s customer credit card details.